Table of Contents
1. Introduction
In this blog post, we will take a look at the security blog post published by AWS. The post is about detecting bot traffic using a rate-based rule and CAPTCHA action.
This method will require a CAPTCHA test to IP addresses that access pages like contact forms multiple times to block the bots and allow human access by issuing a token after passing a test and allowing access for a period of time without retaking a test.
Use AWS WAF CAPTCHA to protect your application against common bot traffic
2. What is CAPTCHA?
We’ve published a blog post about CAPTCHA, but the action has been available since November 8th, 2021 (PDT).
This action allows you to set up a test to differentiate computers from humans by only using AWS WAF rules.
3. What is a rate-based rule?
Rate-based rules will track the request rate from each requester’s IP address and trigger an action when the number of requests exceeds the specified rate limit. By using this, a rule can temporarily block requests from IP addresses that are sending an excessive amount of requests.
Refer to a blog post below for more information on the rate-based rules.
How to use rate-based rules
4. Creating a rule
In this post, we are going to create a rule that shows the CAPTCHA test when there are 100 requests in five minutes to a path "/test."
First, select "Add my own rules and rule groups" from "Add rules" on the Web ACLs page.
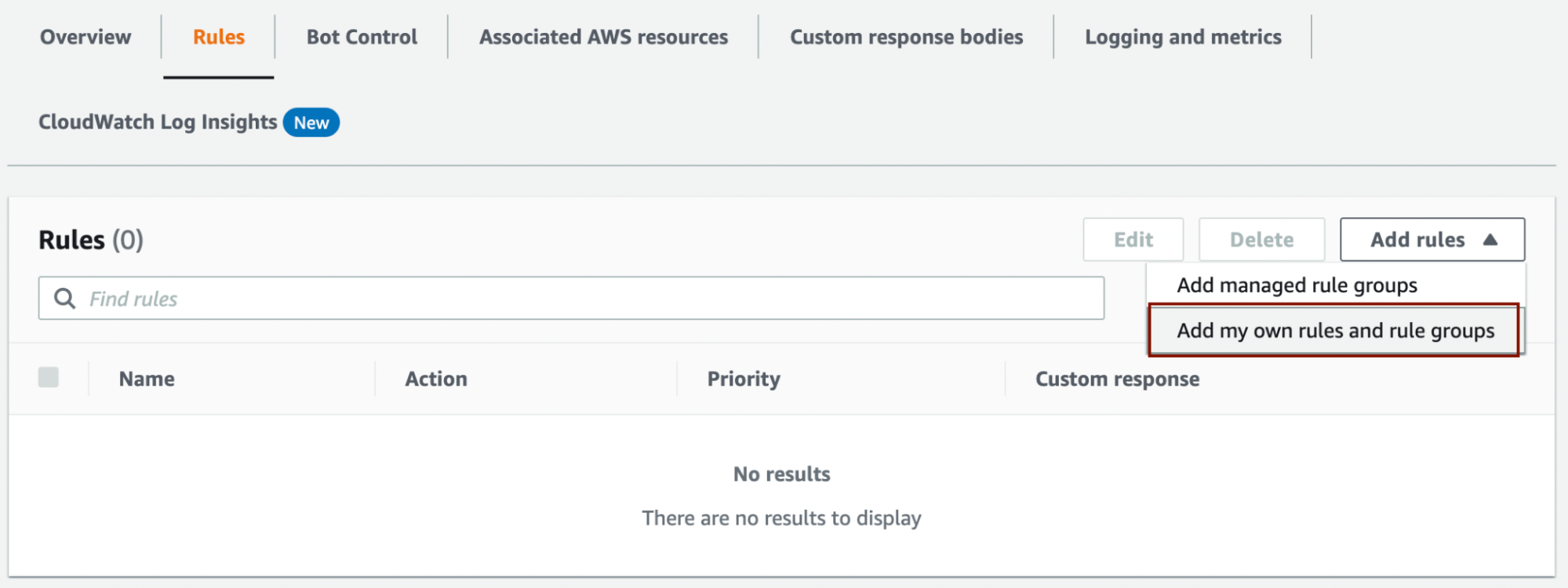
Enter the rule name (CaptchaOnRBR in the image below) and select "Rate-based rule" under the Type.
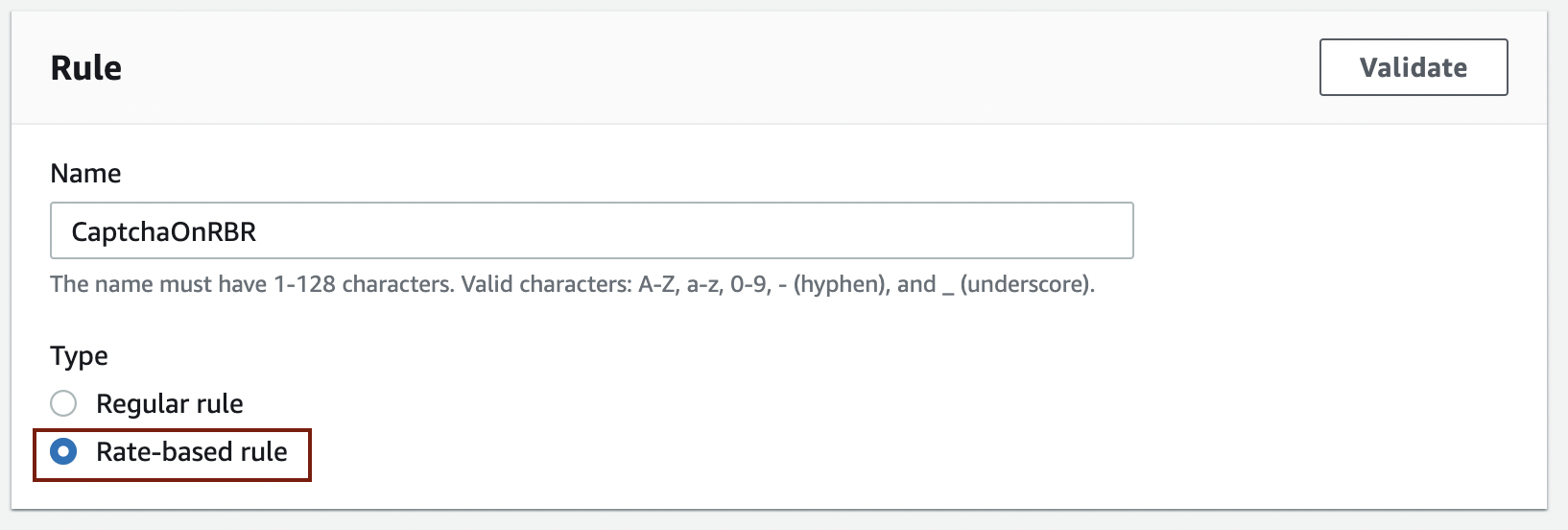
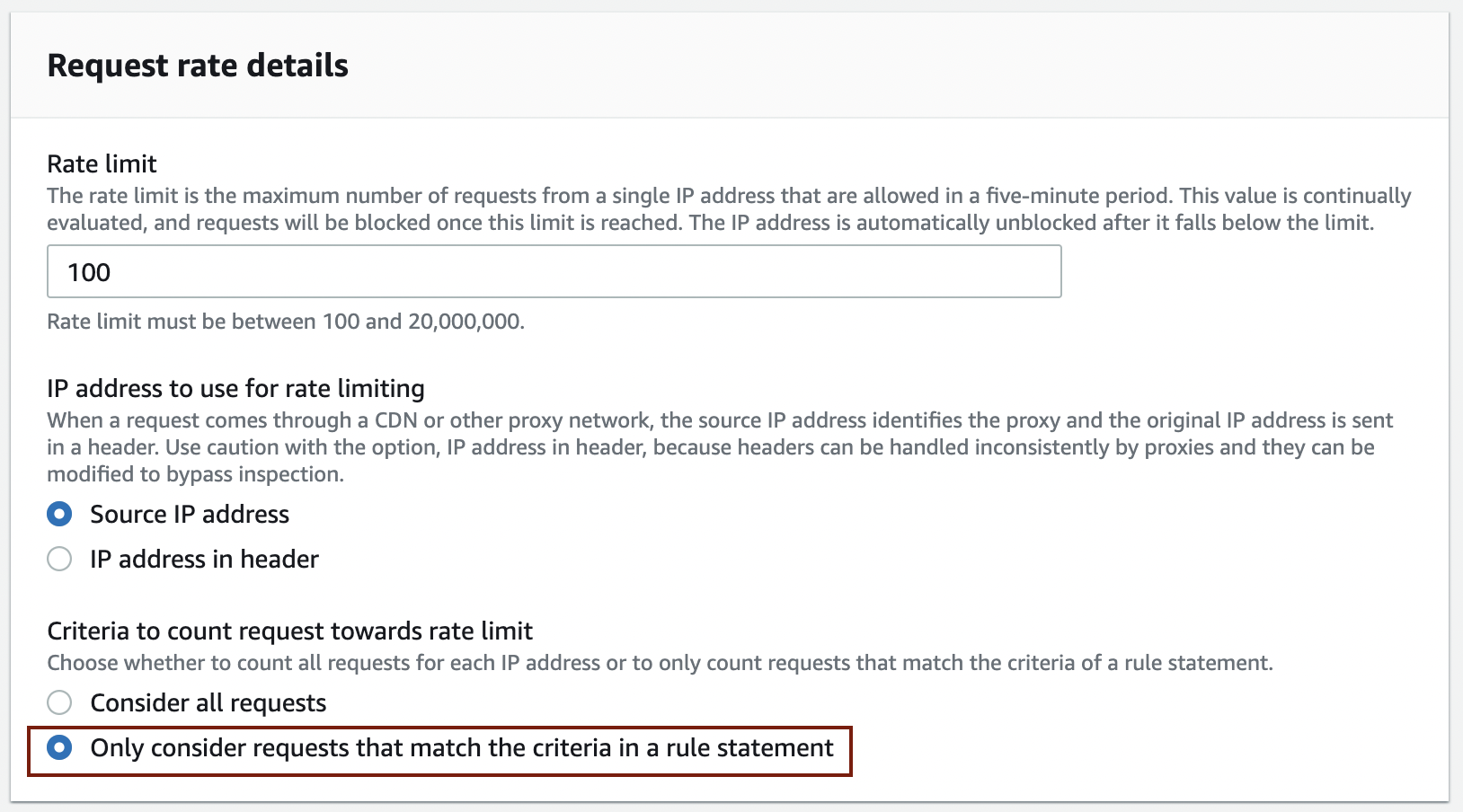
Under the Request rate details section, enter 100 in Rate limit and select Source IP address for the IP address to use for rate limiting.
We are going to apply rate-based rules when requests are sent to the URI "/test," so select Only consider requests that match the criteria in a rule statement under the Criteria to count request towards rate limit.
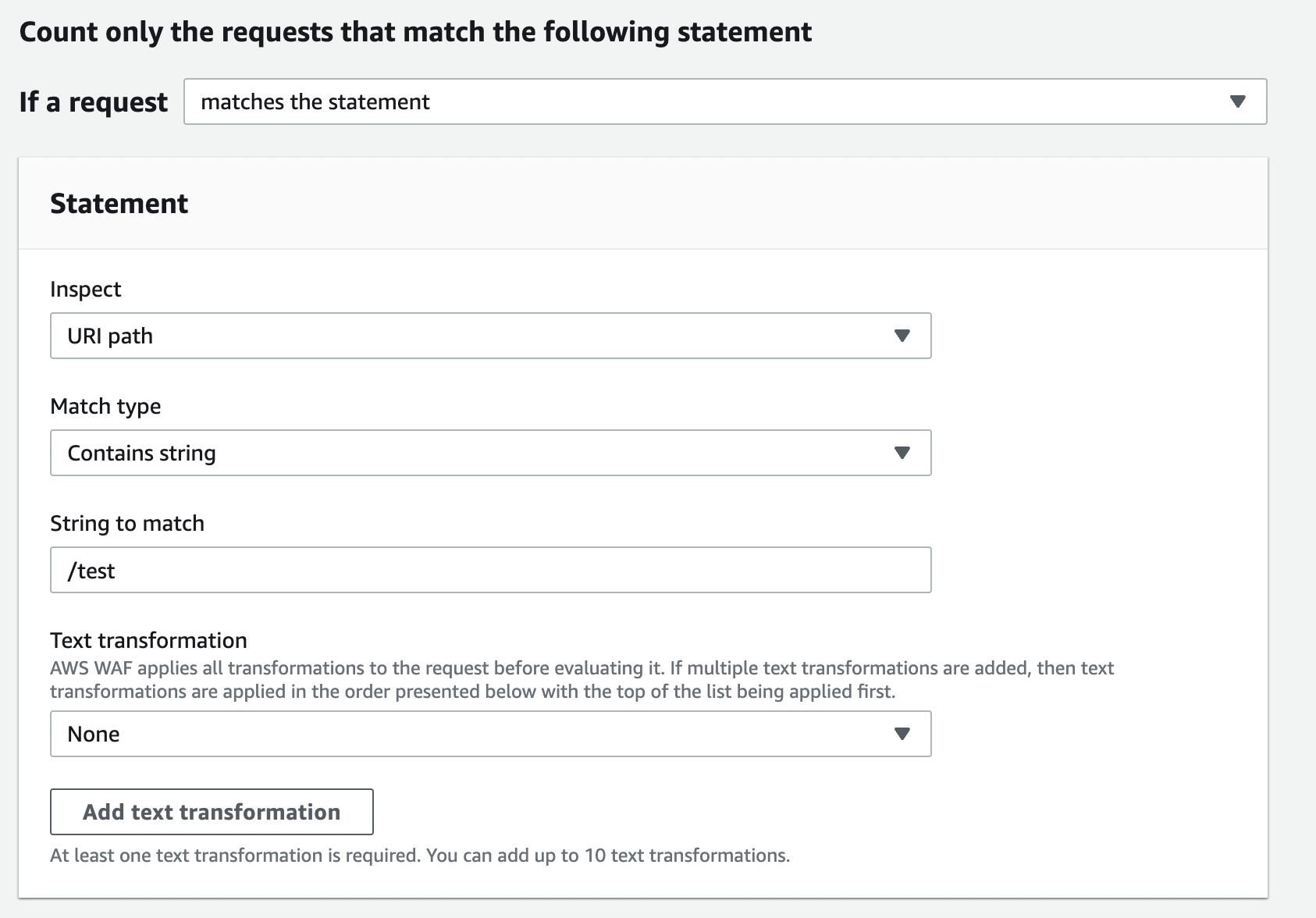
The section to specify details such as URI will be shown by selecting this option. Enter the items below.
- If a request matches the statement
- Inspect: URI path
- Match type: Contains string
- String to match: /test
- Text transformation: None
Lastly, configure the Action and Immunity time.
Select CAPTCHA for the action.
Immunity time is set to 300 by default, but we are going to check the Set a custom immunity time for this rule and change the time to 60 in this post.
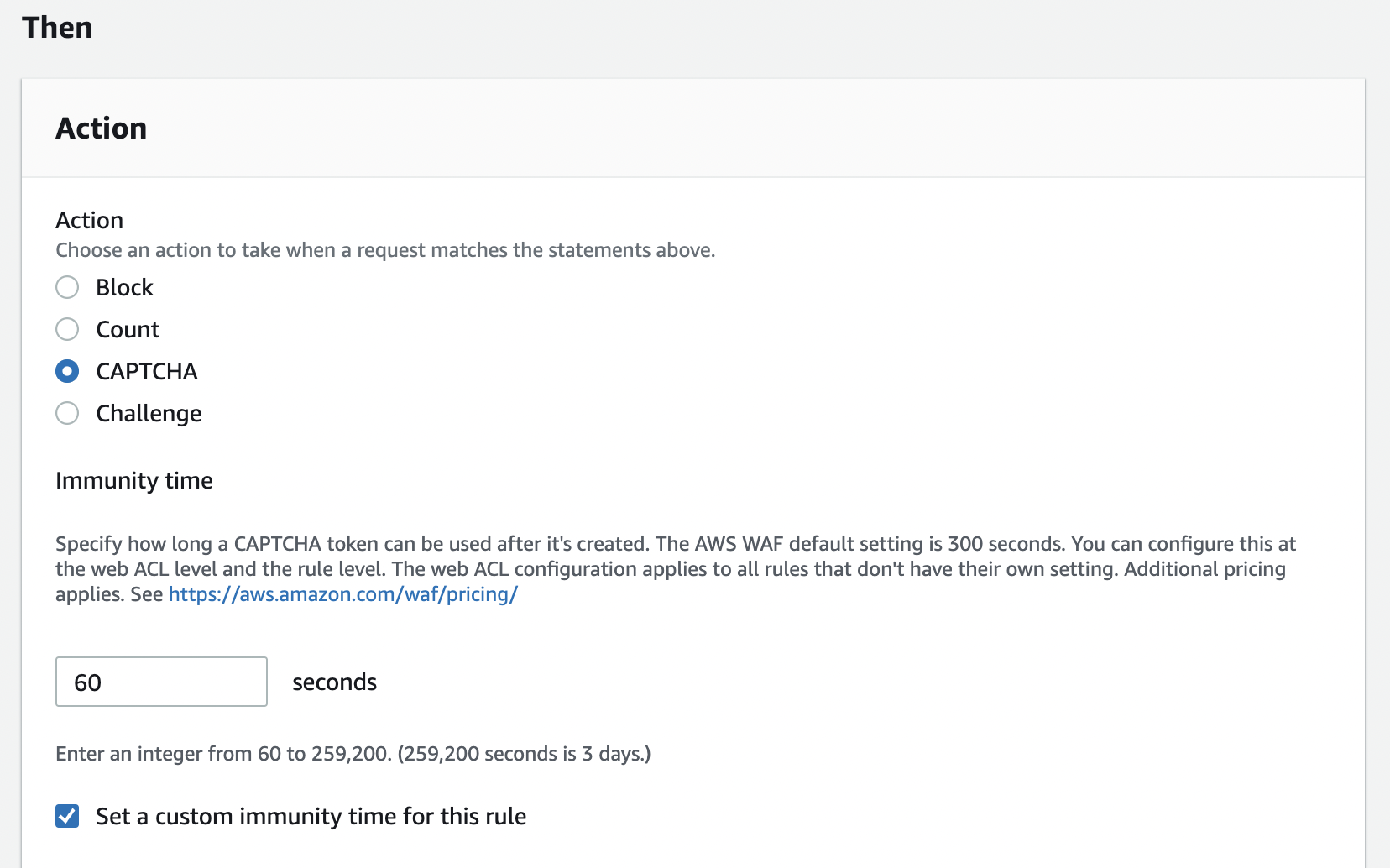
Complete the procedure by clicking the Add rule button and setting the priority.
When we tested from multiple devices after adding the rule, we were presented with the CAPTCHA test after reaching the threshold.
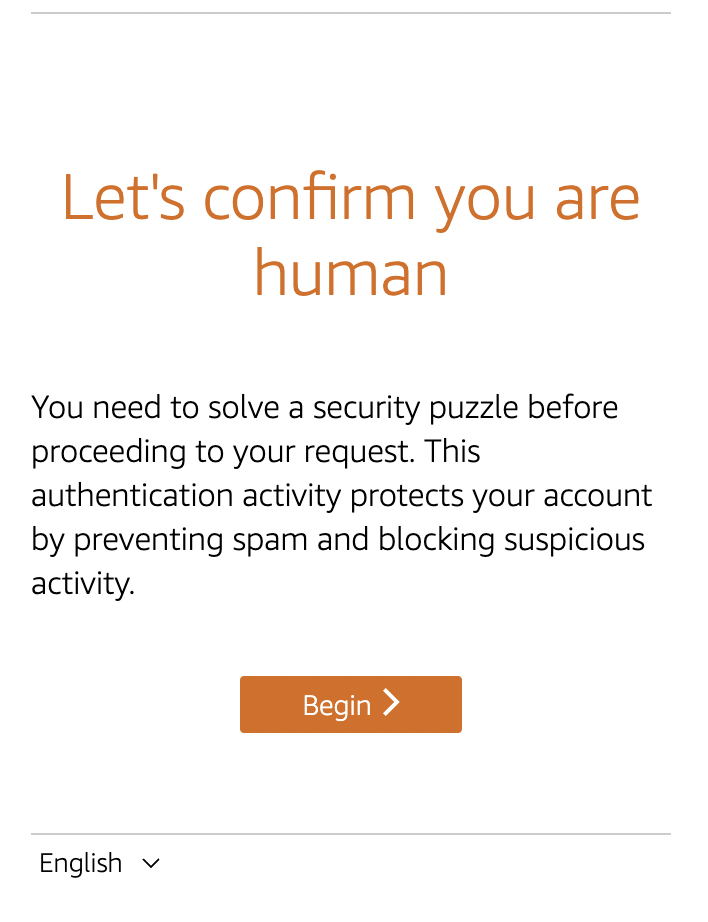
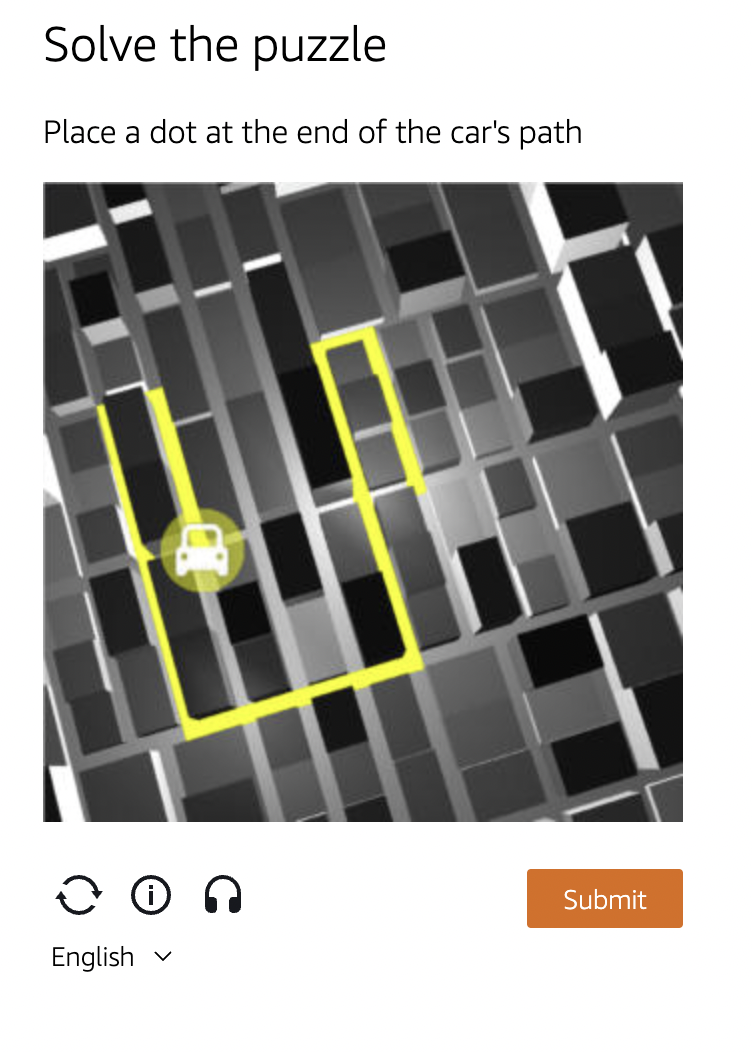
Once you pass the CAPTCHA test, a Cookie will be provided like below (an excerpt from a WAF log).
{
"name": "Cookie",
"value": "aws-waf-token=The token will be inserted here"
},
An excerpt from a WAF log:
"captchaResponse": {
"responseCode": 405,
"failureReason": "TOKEN_MISSING"
}
5. Conclusion
This setting could be beneficial to avoid false positives because the rule will not simply block a specific IP address. Practicality may depend on the website, but it can be a balanced option between security and user experience if you want to accurately block large amount of requests from bots while preventing false positives.
The suitable threshold is different from website to website, so consider what can be accepted in terms of infrastructure and application when creating a rule. We also recommend using the COUNT action to figure out the threshold.




