【Table of contents】
1. Introduction
AWS released a new version of AWS WAF on Nov 25, 2019. In this blog, we explained about the AWS Management Console Operations (Pattern sets & Rule groups).
Part 1: [new AWS WAF] Summary of changes
Part 2: [new AWS WAF] AWS Management Console Operation (Managed Rules)
Part 3: [new AWS WAF] AWS Management Console Operations (Original Rules)
Part 4: [new AWS WAF] AWS Management Console Operations (Pattern Sets & Rule Groups) (this blog)
Part 5: [new AWS WAF] JSON Explanation
2. What is a pattern set?
The pattern set used in AWS WAF Classic for regular expressions can now be applied to IP restrictions. A pattern set is a set of pre-defined contents (regular expression, IP restrictions) that is used to associate with the rule construction.
For example, if you make a pattern that allows all the IPs of your affiliated companies, you can use that IP pattern set as a whitelist in your new environment, and then you can also prepare an IP pattern set for your own company, which is a little narrower, and use it differently depending on the characteristics of your site. Since you only need to make changes to the pattern set side, this is a nice feature for those who manage multiple systems.
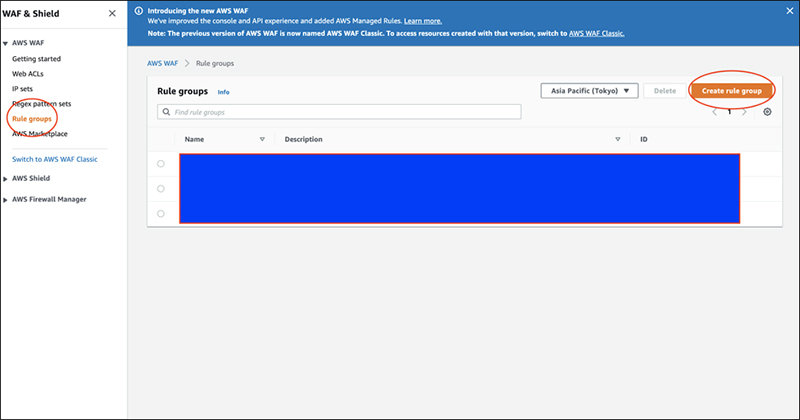
3. How to register?
Select "Regex pattern sets" from the menu on the left and click "Create regex pattern set" on the top right of the screen.
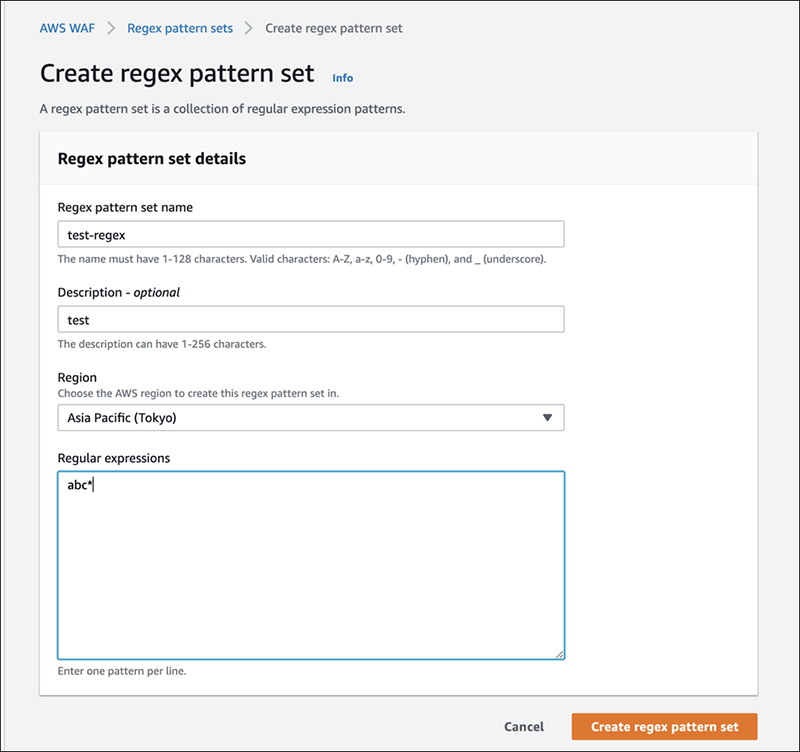
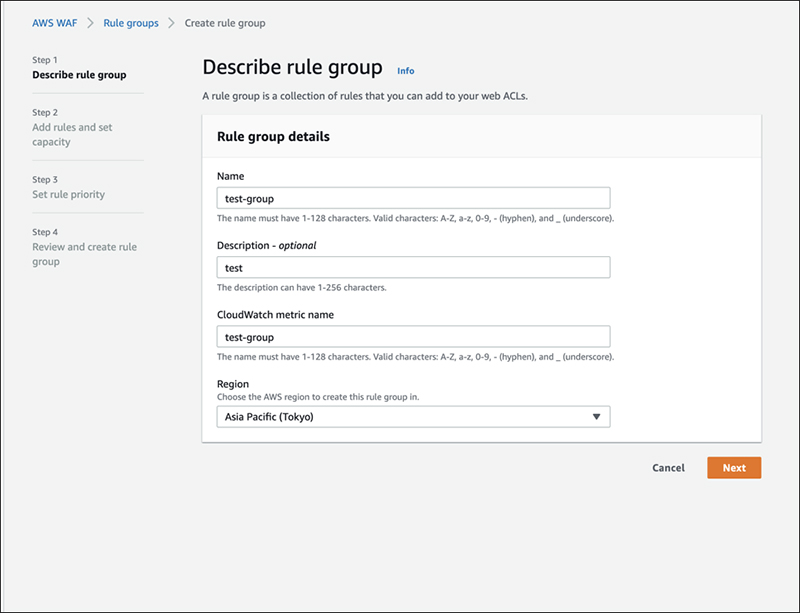
On the next screen, enter a name, description and regular expressions.
One regular expression pattern is written in each line.
Finally, click "Create regex pattern set" to finish.
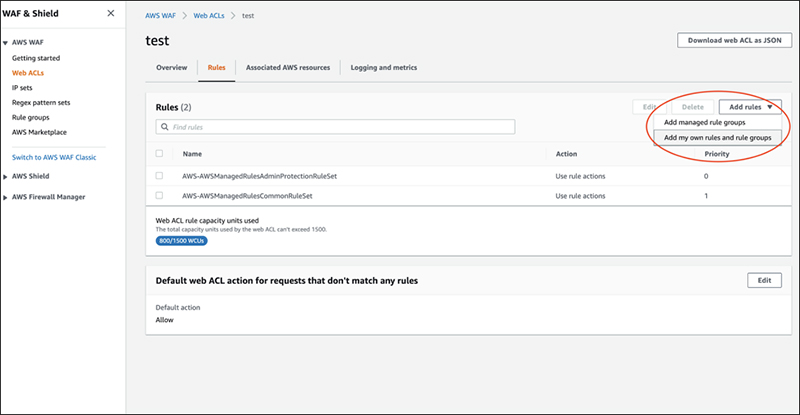
Now, we will attach the rule to the Web ACL. Click "Add rules" and select "Add my own rules and rule groups" from the drop-down menu.
We will create the rule in the same way as the previous original rules edition.
The "Match type" you choose this time will be the rule for the regular expression.
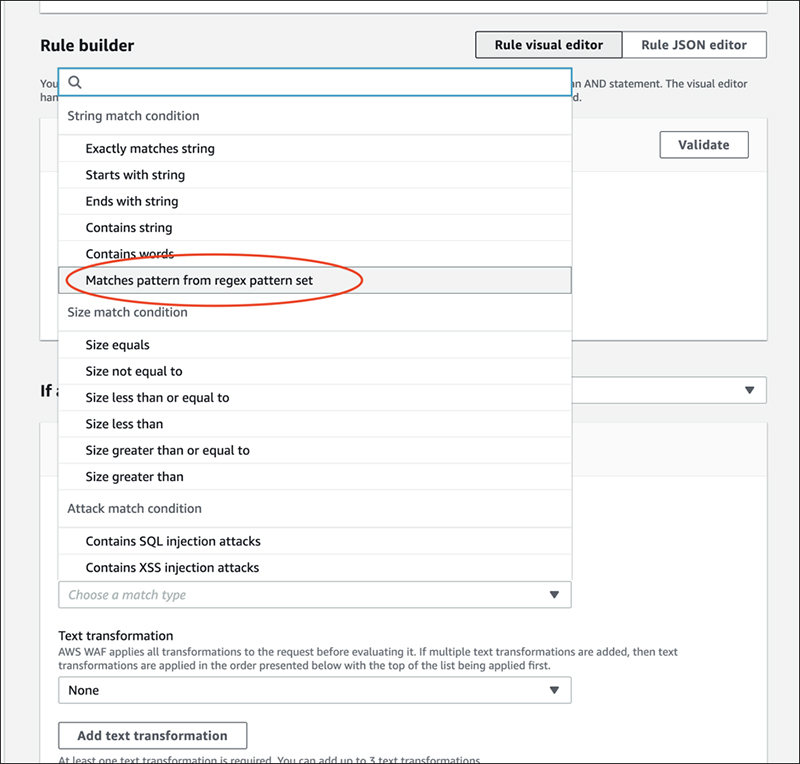
When "Match type" is selected, an item to select a regular expression pattern set has been added. Select the pattern set you just created.
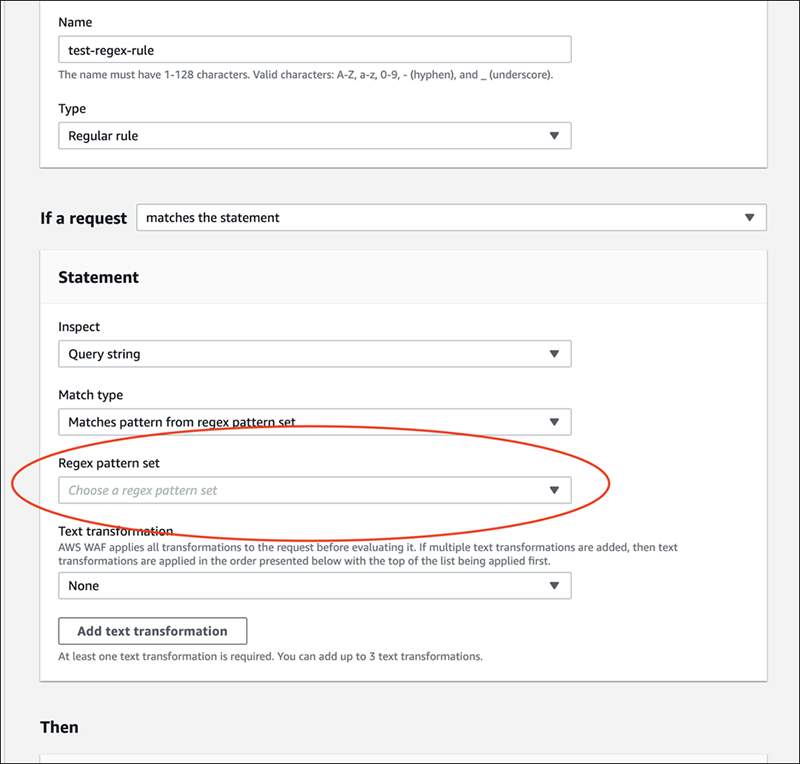
Proceed and save, and you're done setting up the rule.
Now, let's look at it in JSON format.
{
"Name": "test-regex-rule",
"Priority": 0,
"Action": {
"Block": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "test-regex-rule"
},
"Statement": {
"RegexPatternSetReferenceStatement": {
"FieldToMatch": {
"QueryString": {}
},
"ARN": "arn:aws:wafv2:ap-northeast-1:***********:regional/regexpatternset/test-regex/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX",
"TextTransformations": [
{
"Type": "LOWERCASE",
"Priority": 0
}
]
}
}
}
The content of pattern set was not shown, and only the ARN link can be seen.
Updating the content does not change the ARNs, therefore updating the pattern set will update the target associated with it.
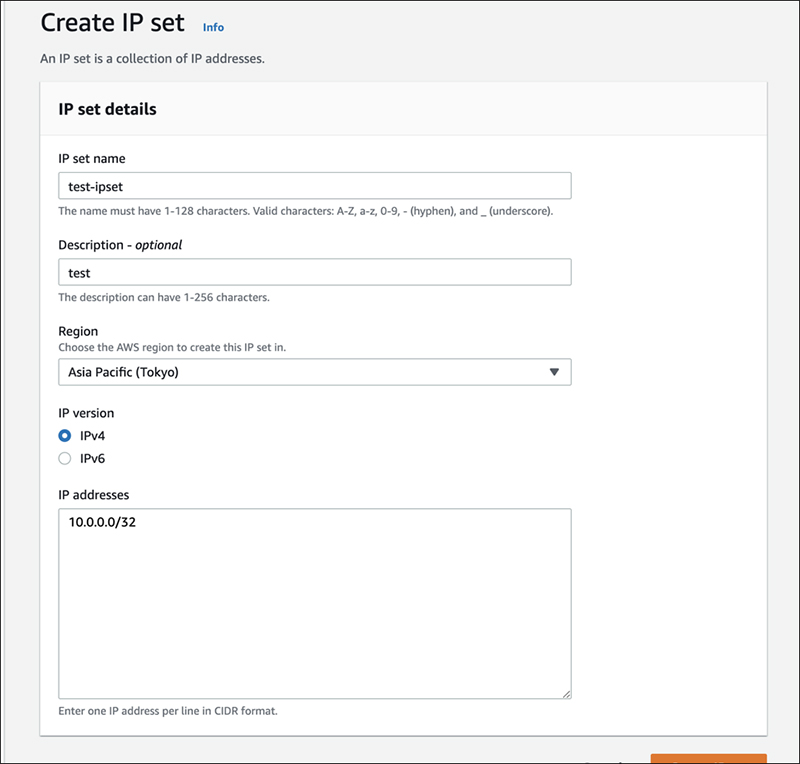
The IP pattern set is also the same, so we will only check the setting screen.
4. What is a rule group?
While it was also available in AWS WAF Classic, the ability to group multiple rules together is also invoked in ARN. As with other rule sets, rewriting a rule group will change the rules that are connected to it, so this is a useful feature if you are managing multiple web ACLs.
First, let's create one.
Enter a name.
This is the rule and capacity setting screen. Let's try putting in some rules.
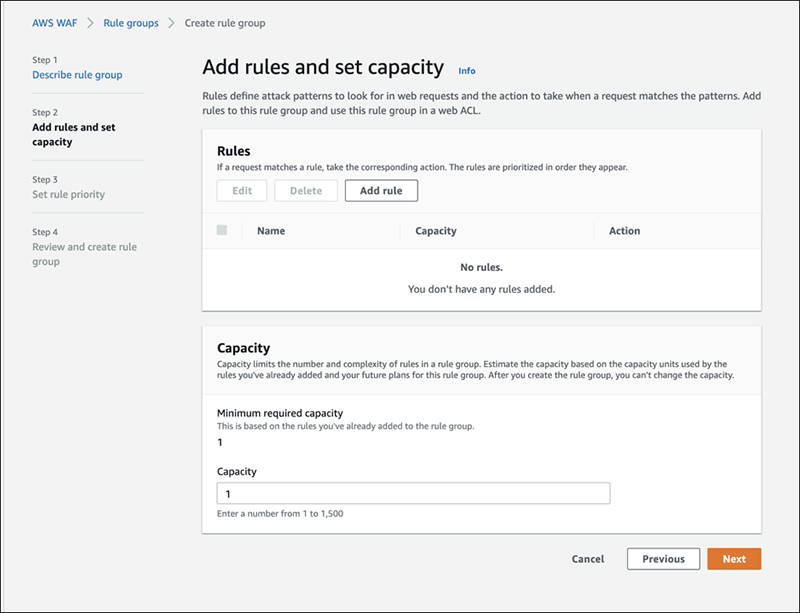
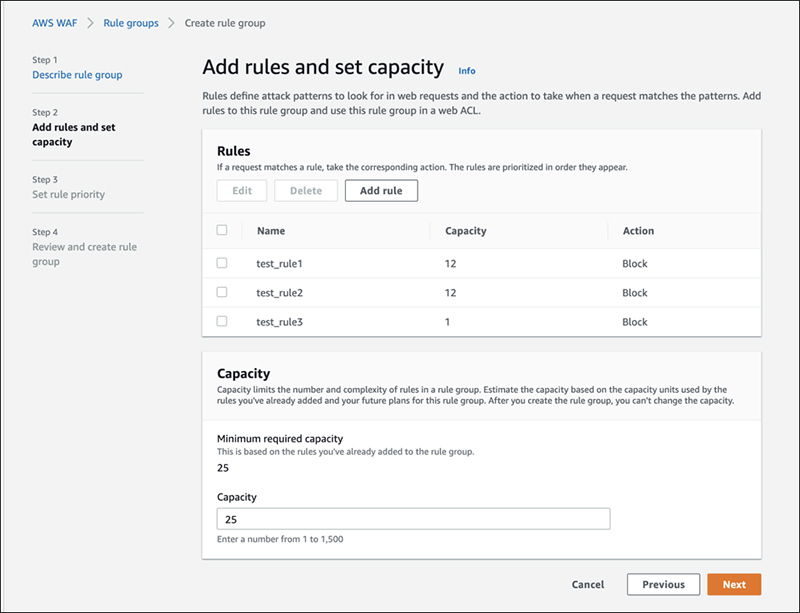
Once the rules are added, the capacity was automatically updated.
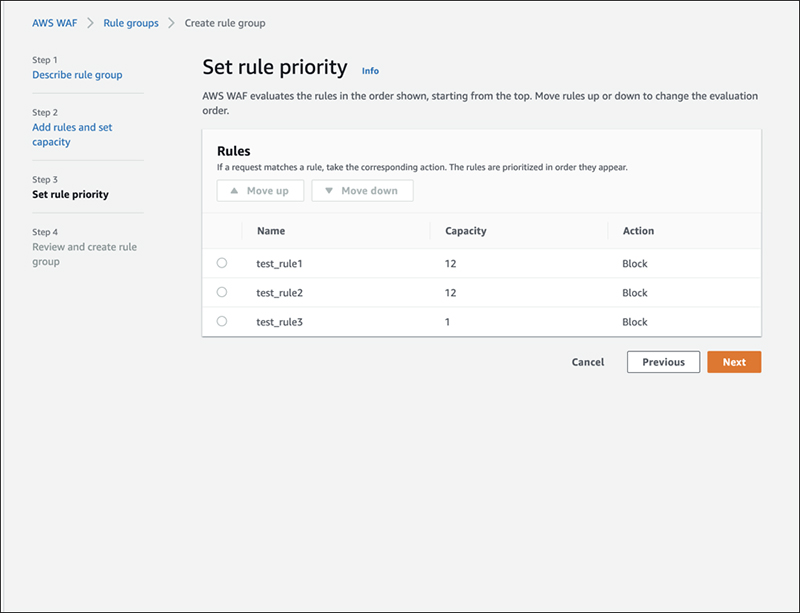
On the next screen, you can change the rule order and set rule priority.
Finally, there is a confirmation screen. Please review and click “Create rule group”.
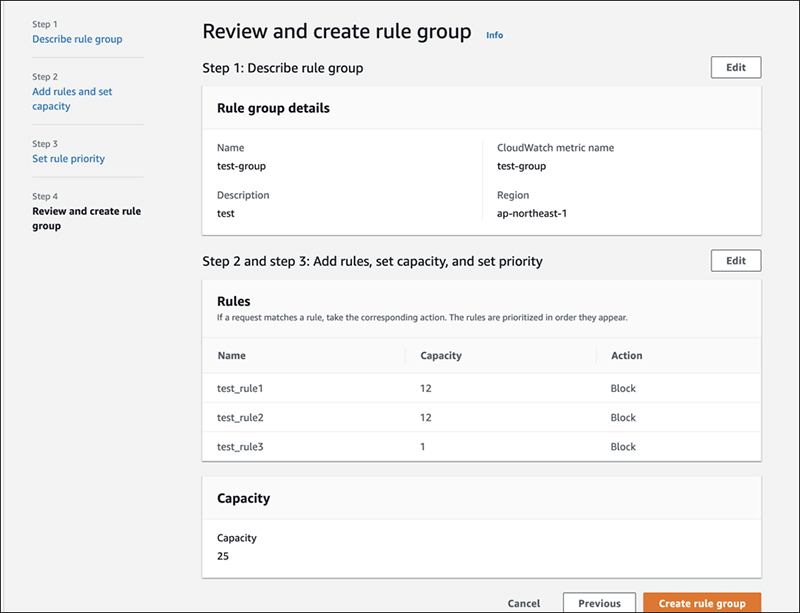
The setup itself was easy.
However, there was one problem when the auto-updated content with the registered rules was used without editing the capacity.
When we tried to add a rule to the rule group from the management console, we got a warning message that it would exceed capacity and we couldn't add it. Given that changes would occur, we needed to declare it in advance, with some value. This capacity is a cost at WCU. It's easier to understand if you think of it as managed rules that you can create on your own.
Now, let's actually attach it.
Rules can be added from the web ACL screen.
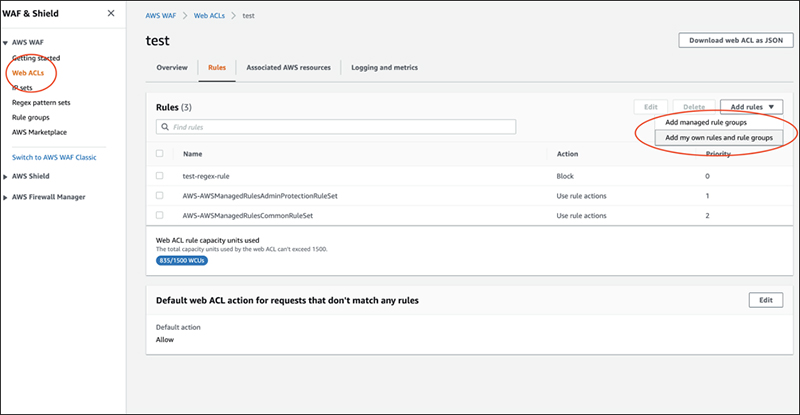
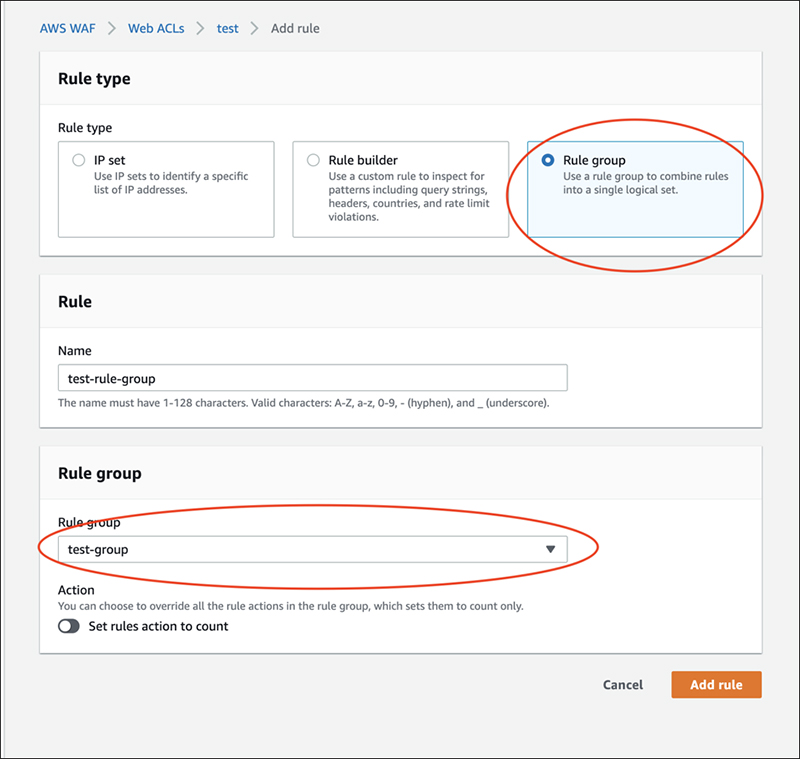
Just select a rule group and then select a registered rule group and you're done.
It is also possible to register the entire rule group in COUNT mode.
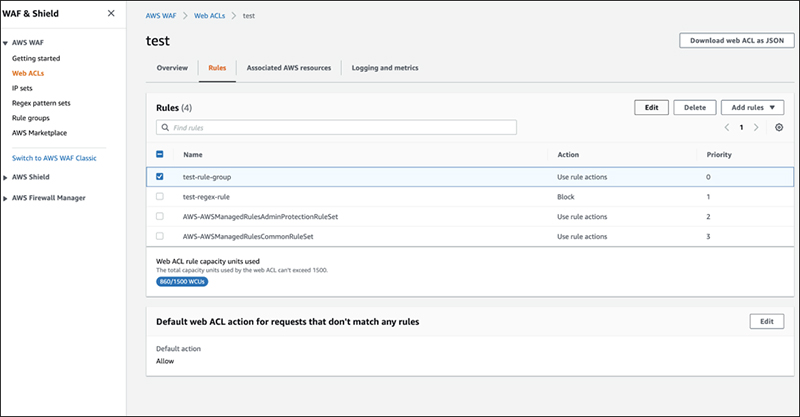
As with managed rules, it is also possible to change only specific rules in a rule group to COUNT mode. To do this, select the target rule group and click “Edit”.
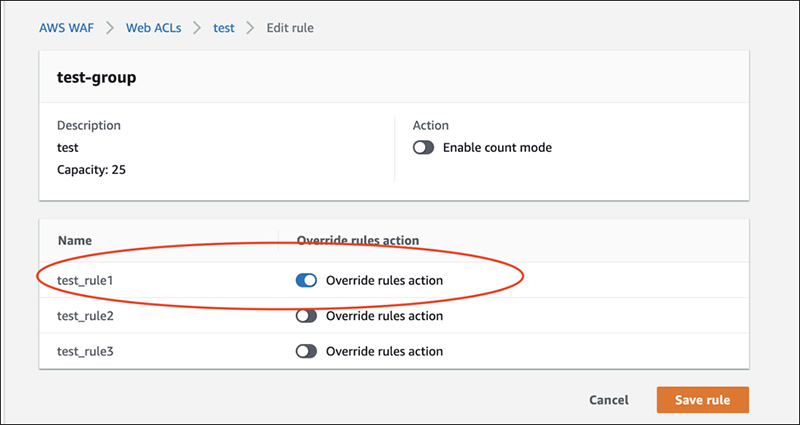
You can now put a specific rule in COUNT mode.
Let’s check the status in JSON.
Similar to the regular expression ruleset, it is called by ARN.
Also, similar to managed rules, we could see that some rules were ExcludedRules.
{
"Name": "test",
"Id": "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX",
"ARN": "arn:aws:wafv2:ap-northeast-1:************:regional/webacl/test/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX",
"DefaultAction": {
"Allow": {}
},
"Description": "",
"Rules": [
{
"Name": "test-rule-group",
"Priority": 0,
"Statement": {
"RuleGroupReferenceStatement": {
"ARN": "arn:aws:wafv2:ap-northeast-1:************:regional/rulegroup/test-group/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX",
"ExcludedRules": [
{
"Name": "test_rule1"
}
]
}
},
"OverrideAction": {
"None": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "test-rule-group"
}
},
{
"Name": "test-regex-rule",
"Priority": 1,
"Statement": {
"RegexPatternSetReferenceStatement": {
"ARN": "arn:aws:wafv2:ap-northeast-1:************:regional/regexpatternset/test-regex/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX",
"FieldToMatch": {
"QueryString": {}
},
"TextTransformations": [
{
"Priority": 0,
"Type": "LOWERCASE"
}
]
}
},
"Action": {
"Block": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "test-regex-rule"
}
},
{
"Name": "AWS-AWSManagedRulesAdminProtectionRuleSet",
"Priority": 2,
"Statement": {
"ManagedRuleGroupStatement": {
"VendorName": "AWS",
"Name": "AWSManagedRulesAdminProtectionRuleSet",
"ExcludedRules": [
{
"Name": "AdminProtection_URIPATH"
}
]
}
},
"OverrideAction": {
"None": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "AWS-AWSManagedRulesAdminProtectionRuleSet"
}
},
{
"Name": "AWS-AWSManagedRulesCommonRuleSet",
"Priority": 3,
"Statement": {
"ManagedRuleGroupStatement": {
"VendorName": "AWS",
"Name": "AWSManagedRulesCommonRuleSet",
"ExcludedRules": [
{
"Name": "UserAgent_BadBots_HEADER"
},
{
"Name": "SizeRestrictions_URIPATH"
},
{
"Name": "EC2MetaDataSSRF_URIPATH"
}
]
}
},
"OverrideAction": {
"None": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "AWS-AWSManagedRulesCommonRuleSet"
}
}
],
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "test"
},
"Capacity": 860
}
5. Conclusion
With the WCU in mind, it's possible to create and manage your own rule sets.




