Table of Contents
- 1. Introduction
- 2. What is Account Creation Fraud Prevention (ACFP)?
- 3. How to add ACFP rules
- 4. Overview of the rules in ACFP
- 5. Usage with WafCharm
- 6. Conclusion
1. Introduction
AWS WAF announced the release of rules to prevent the creation of fake or fraudulent accounts in AWS WAF Managed Rules on June 13th, 2023.
The name of the rule group "Account Creation Fraud Prevention" can be shortened to ACFP.
AWS WAF Fraud Control launches account creation fraud prevention and reduced pricing
We will take a look at the new rule group in this post.
2. What is Account Creation Fraud Prevention (ACFP)?
ACFP includes rules to protect against attackers attempting to create fake accounts or fraudulent accounts. The rules can block suspicious requests that include abnormal activity when attempting to create an account.
In addition, they can also inspect responses to block client sessions or IP addresses with a high volume of unsuccessful account creation requests when protecting CloudFront distributions.
Please keep in mind that AWS WAF will charge an added fee when using this rule. Refer to the AWS WAF Pricing for more details.
3. How to add ACFP rules
You can add the ACFP rule group with the procedure below.
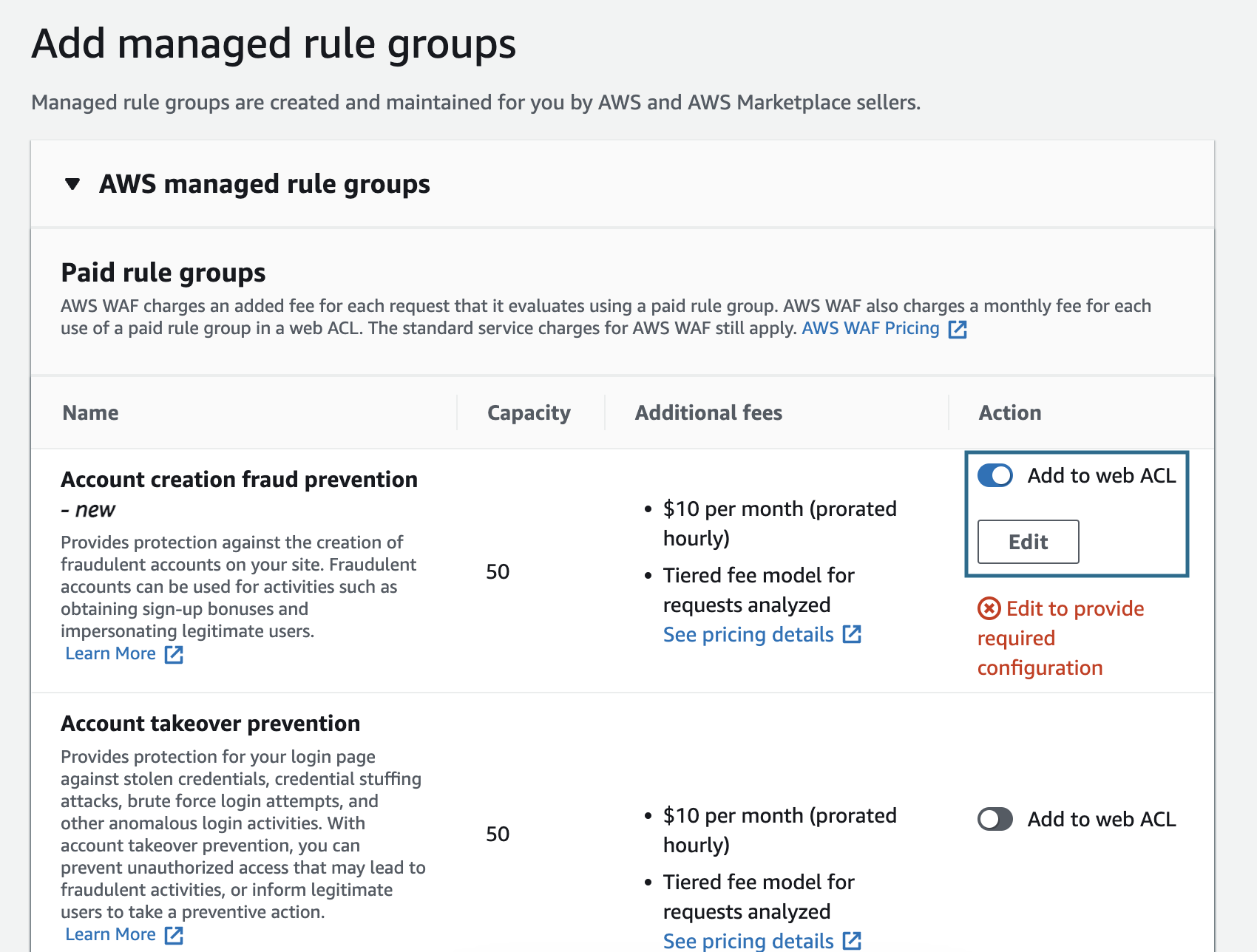
1. Click the [Add rules] button placed on the right side of the web ACL page and click [Add managed rule groups].
2. Open [AWS managed rule groups]
3. Click the [Add to web ACL] toggle button on the right side of [Account creation fraud prevention].
4. Click the [Edit] button.
5. Input necessary information under [Scope of inspection] and [Rule group configuration] and click the [Save] button.
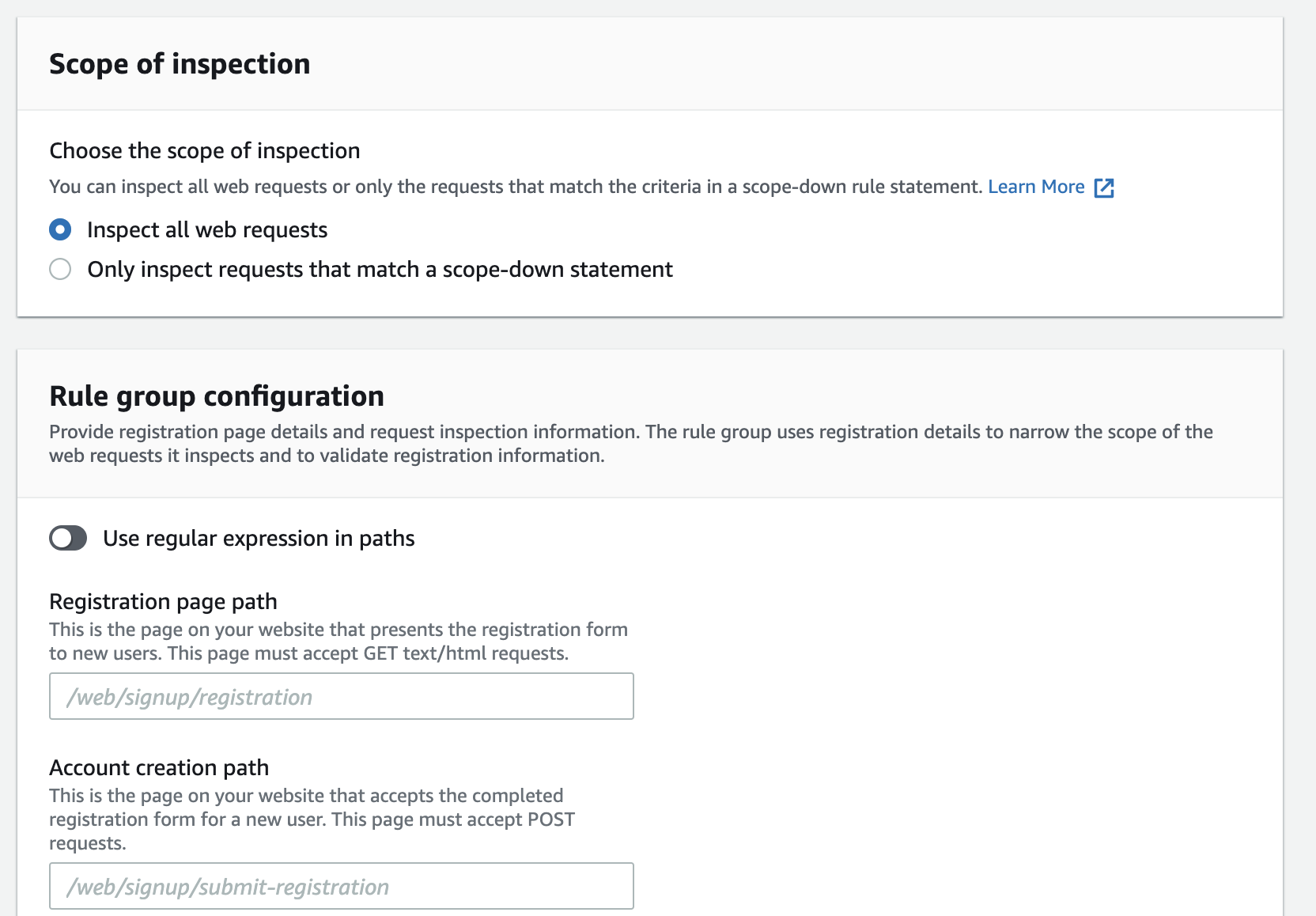
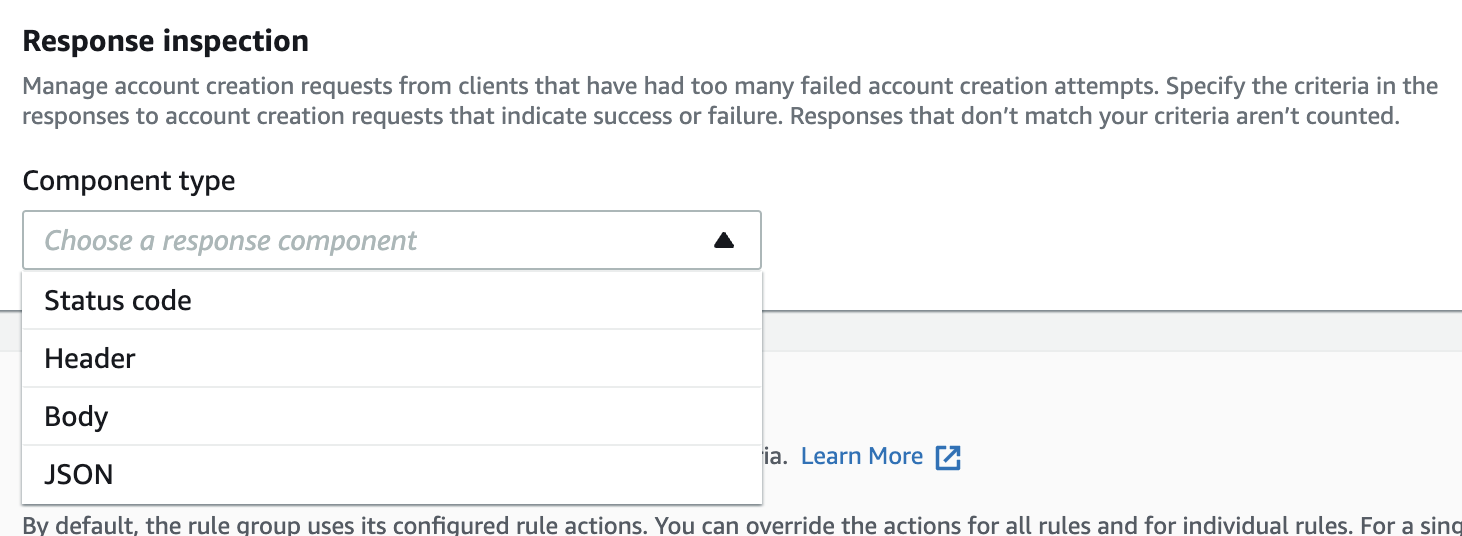
Since ACFP inspects account creation, you must specify details such as paths to the registration form page and account creation page. For web ACLs associated with CloudFront, there is a section for response inspection as well.
In addition, you will have to add SDK into your application after applying the rule group to your web ACL in order to fully use the ACFP rules because ACFP has rules that use tokens.
Please refer to the AWS Security Blog for more details on how to configure the rule group and add SDK.
Prevent account creation fraud with AWS WAF Fraud Control – Account Creation Fraud Prevention
4. Overview of the rules in ACFP
There are multiple rules in ACFP, such as a rule to inspect all requests and apply challenge action, a rule to inspect highly suspicious IP addresses, and a rule to inspect credentials using a stolen credential database. These rules utilize tokens added by SDK and labels, and some rules require SDK implementation for the rules to be functional.
Below is the list of rules and a brief description.
| Rule name | Description |
|---|---|
| UnsupportedCognitoIDP | Inspects for web traffic going to an Amazon Cognito user pool. ACFP isn't available for use with Amazon Cognito user pools, and this rule helps to ensure that the other ACFP rule group rules are not used to evaluate user pool traffic. |
| AllRequests | Applies the Challenge action to requests that access the registration page path. |
| RiskScoreHigh | Inspects for requests whose IP addresses are considered to be highly suspicious. |
| SignalCredentialCompromised | Searches the stolen credential database for the credentials that were submitted in the request. |
| SignalClientInteractivityAbsentLow | Inspects the request's token for data that indicates abnormal human interactivity with the application. This rule requires SDK implementation. |
| SignalAutomatedBrowser | Inspects the request's token for indicators that the client browser might be automated. |
| SignalBrowserInconsistency | Inspects the request's token for inconsistent browser interrogation data. |
| VolumetricIpHigh | Inspects for high volumes of requests sent from individual IP addresses. |
| VolumetricSessionHigh | Inspects for high volumes of requests sent from individual client sessions. |
| AttributeUsernameTraversalHigh | Inspects for a high rate of requests from a single client session that use different usernames. |
| VolumetricPhoneNumberHigh | Inspects for high volumes of account creation requests that use the same phone number. |
| VolumetricAddressHigh | Inspects for high volumes of account creation requests that use the same physical address. |
| VolumetricAddressLow | Inspects for low and medium volumes of account creation requests that use the same physical address. |
| VolumetricIPSuccessfulResponse | Inspects for a high volume of successful account creation requests for a single IP address. AWS WAF only evaluates this rule in web ACLs that protect Amazon CloudFront distributions. |
| VolumetricSessionSuccessfulResponse | Inspects for a high volume of success responses from the protected resource to account creation requests that are being sent from a single client session. AWS WAF only evaluates this rule in web ACLs that protect Amazon CloudFront distributions. |
| VolumetricSessionTokenReuseIp | Inspects for the use of a single token among more than 5 distinct IP addresses. |
Please refer to the document below for a more detailed overview of the ACFP rules.
AWS WAF Fraud Control account creation fraud prevention (ACFP) rule group
5. Usage with WafCharm
AWS Managed Rule Account Creation Fraud Prevention can be used with WafCharm rules.
6. Conclusion
With the addition of ACFP, you can now protect against account creation.
Although complex configuration is required in advance, you will be able to protect the account creation and sign-in flow by using the ACFP rule with the account takeover prevention (ATP) rule. These rules would be beneficial to those who manage websites with account creations and sign-ins.




