This post was originally written in Japanese in the past.
Table of Contents
- 1. Introduction
- 2. What is AWS WAF Fraud Control account takeover prevention (ATP) rule?
- 3. How to set up the rule
- 4. Testing the rule
- 5. Effects on WafCharm
- 6. Conclusion
1. Introduction
AWS WAF was updated on February 11th, 2022 to offer AWS WAF Fraud Control account takeover prevention (ATP) in Managed Rules. We will take a look at how to set up the rule.
2. What is AWS WAF Fraud Control account takeover prevention (ATP) rule?
It is a managed rule provided by AWS to prevent accesses that frandulently take over account information or monitor and control access that may seem to have leaked already. ATP stands for Account Takeover Prevention.
The rule contains two main parts.
- Rule to detect abnormal login trials
- Rule to check credential information suspected of leakage obtained from dark web
In the rule to detect abnormal login trials, it seems like it will detect accesses that continue to try to login using the same accout with different passwords and vise versa or detect sessions that extend over long period of time.
Dark web refers to web that uses internet but cannot be accessed via typical browsers. Because all accesses are anonymous, it could be used for illegal activities. Leaked account information can also be exchanged on the dark web, so the provided rule can cross-check against the information.
| Rule Name | Description and label |
|---|---|
| VolumetricIpHigh |
Inspects for high volumes of requests sent from individual IP addresses. The rule applies the following labels to requests.
awswaf:managed:aws:atp:aggregate:volumetric:ip:high |
| AttributePasswordTraversal |
Inspects for attempts that use password traversal. awswaf:managed:aws:atp:aggregate:attribute:password_traversal |
| AttributeLongSession |
Inspects attempts that use sessions that last for a long period of time. awswaf:managed:aws:atp:aggregate:attribute:long_session |
| AttributeUsernameTraversal |
Inspects attemps that uses user name traversal. awswaf:managed:aws:atp:aggregate:attribute:username_traversal |
| AttributeCompromisedCredentials |
Inspects attemps that uses stolen crendentials. awswaf:managed:aws:atp:aggregate:attribute:compromised_credentials |
| VolumetricSession |
Inspects a large amount of requests sent from individual sessions. awswaf:managed:aws:atp:aggregate:volumetric:session |
| MissingCredential |
Inspects missing credentials. awswaf:managed:aws:atp:signal:missing_credential |
| TokenRejected |
Inspects tokens rejected by token validation service. awswaf:managed:token:rejected |
|
No rules provided. Rule group add labels for matching requests; no actions are taken on the requests. |
Label indicates that a credential used in a request is present in the stolen credentials database. awswaf:managed:aws:atp:signal:credential_compromised |
|
No rules provided. Token service adds labels to matching requests; no actions are taken on the request. |
Label indicates that a token within a request is accepted by token validation service. awswaf:managed:token:accepted |
There are rules that only add labels so you could control the response by adding a subsequent rule to utilize the labels.
Refer to the blog post below for how to use the labels.
How to use label feature in AWS WAF
3. How to set up the rule
We will create a Web ACL under the region “us-east-1” that has Account takeover prevention rules available to try them.
Go to your Web ACL’s rules page, click on the “Add rules” button and select “Add managed rule groups” button.
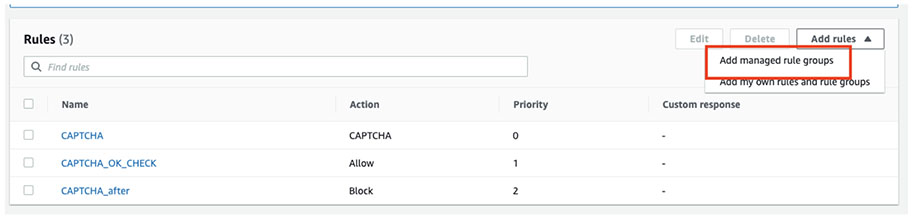
Add “Account takeover prevention” rule group.
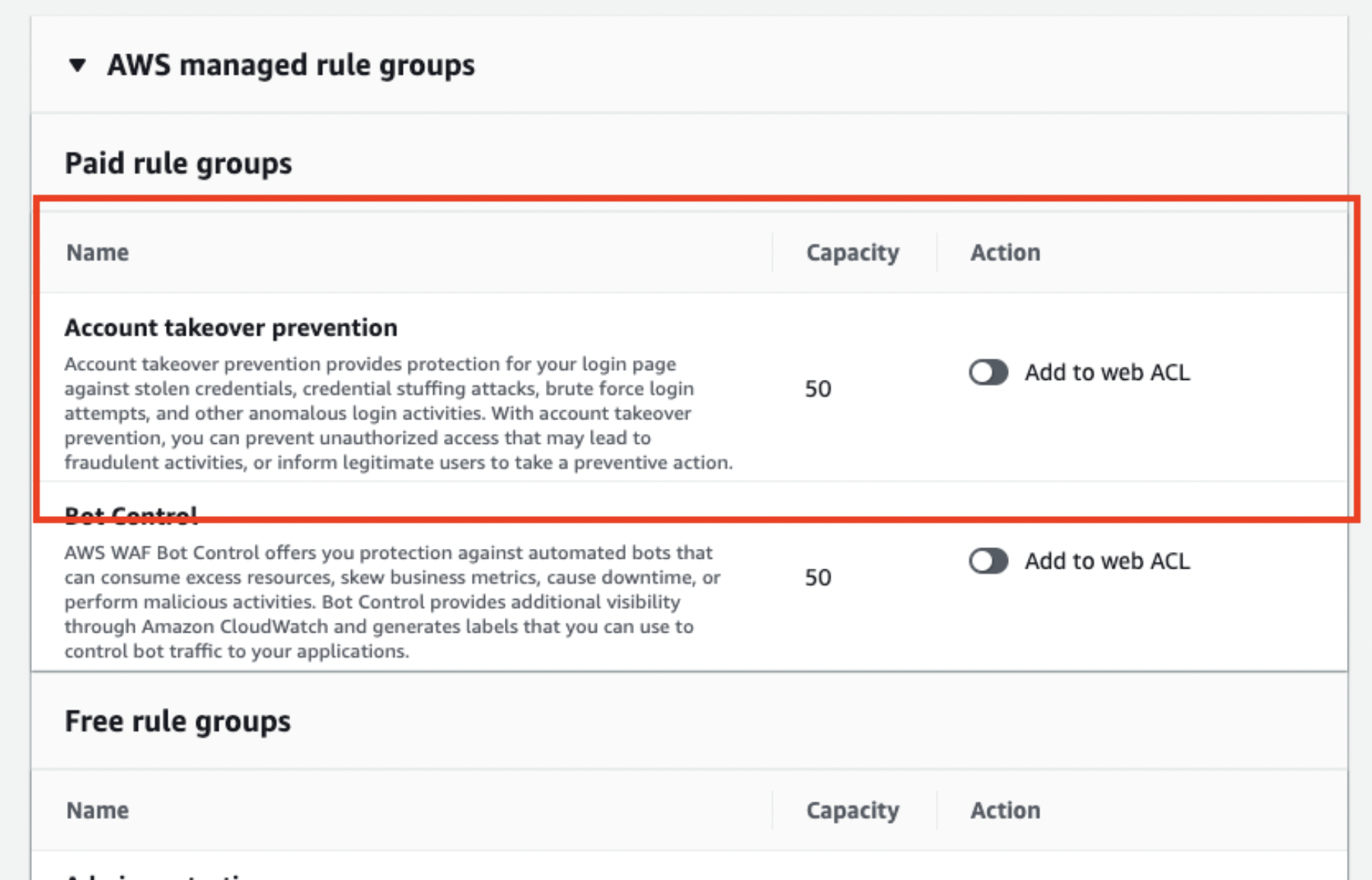
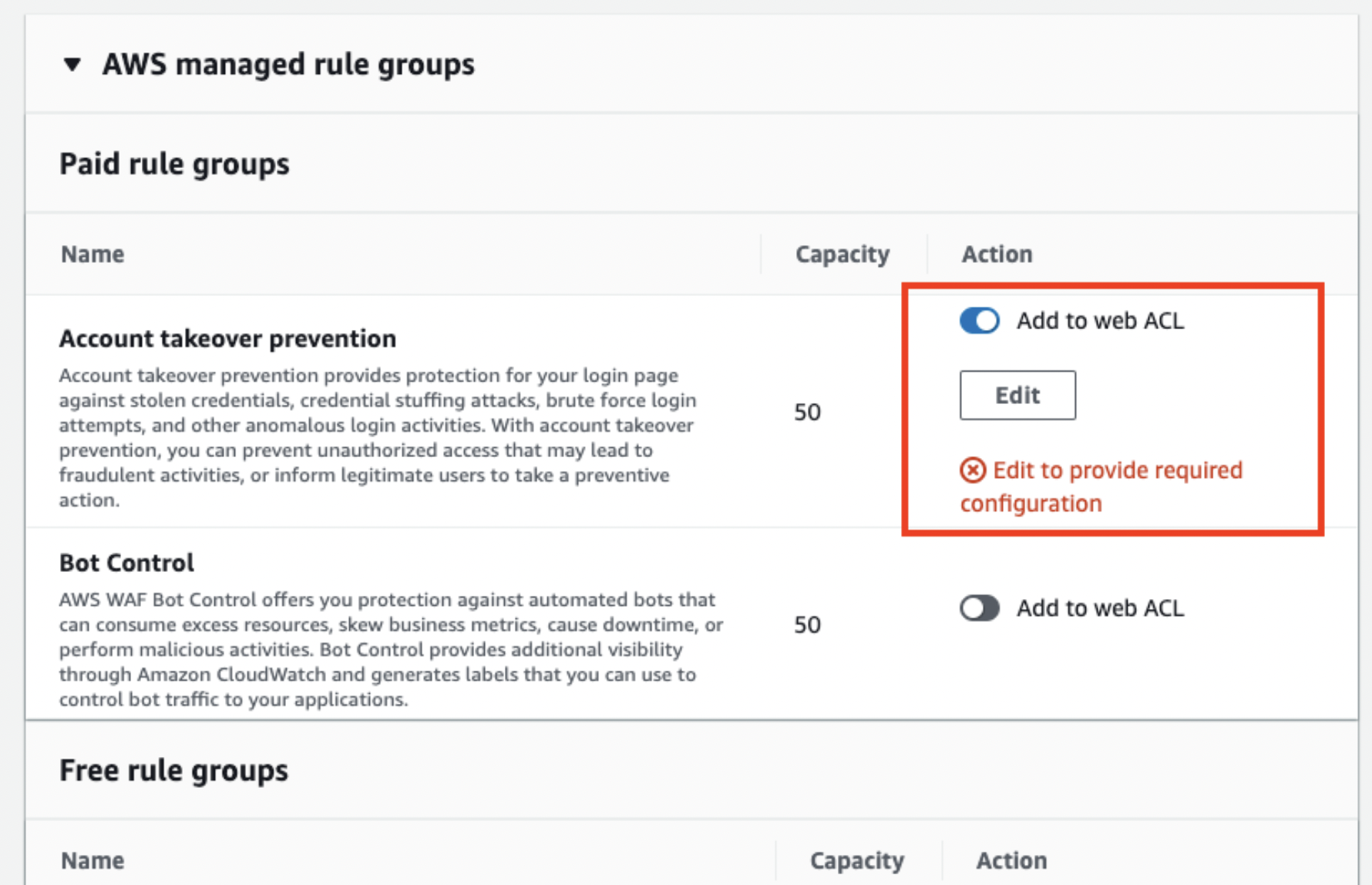
You will be asked to edit the rule group, so open the edit page.
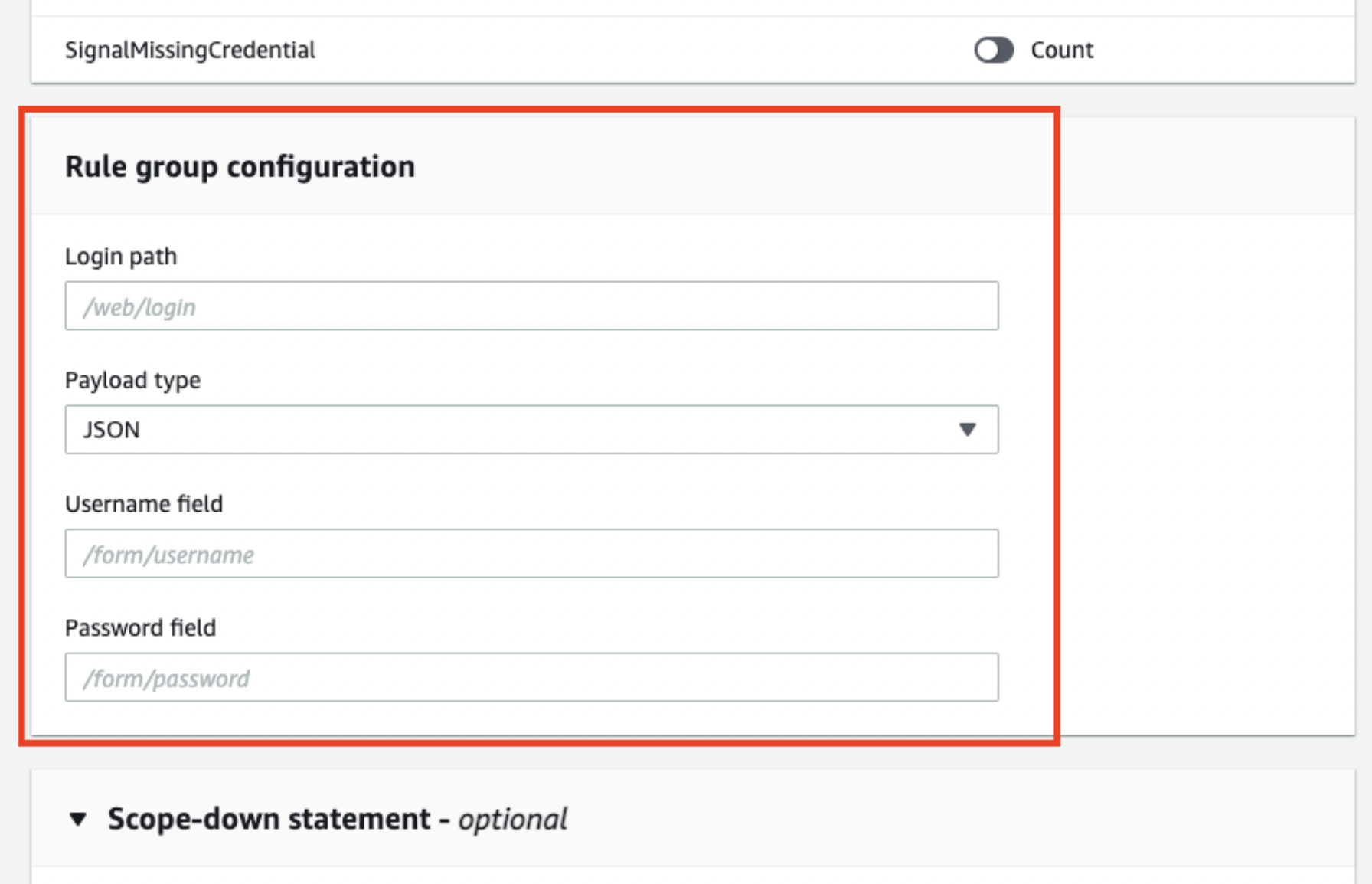
Enter login path and account information format.
Once you’re done saving the configuration, you will be able to add rules at the bottom of the page.
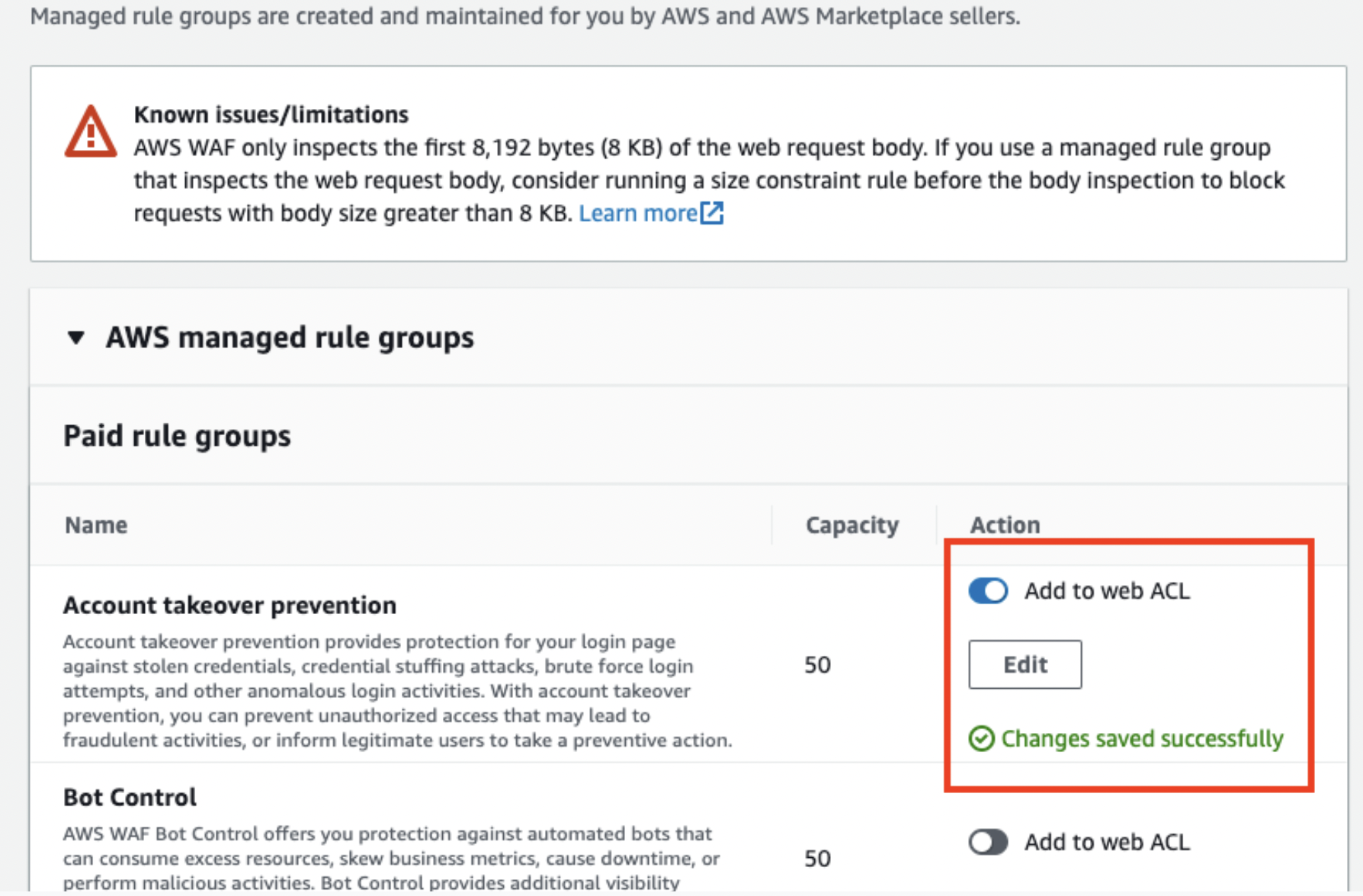
You can check the login path information you’ve set up earlier after you add the rule. You can also edit the setting from the “Edit” button.
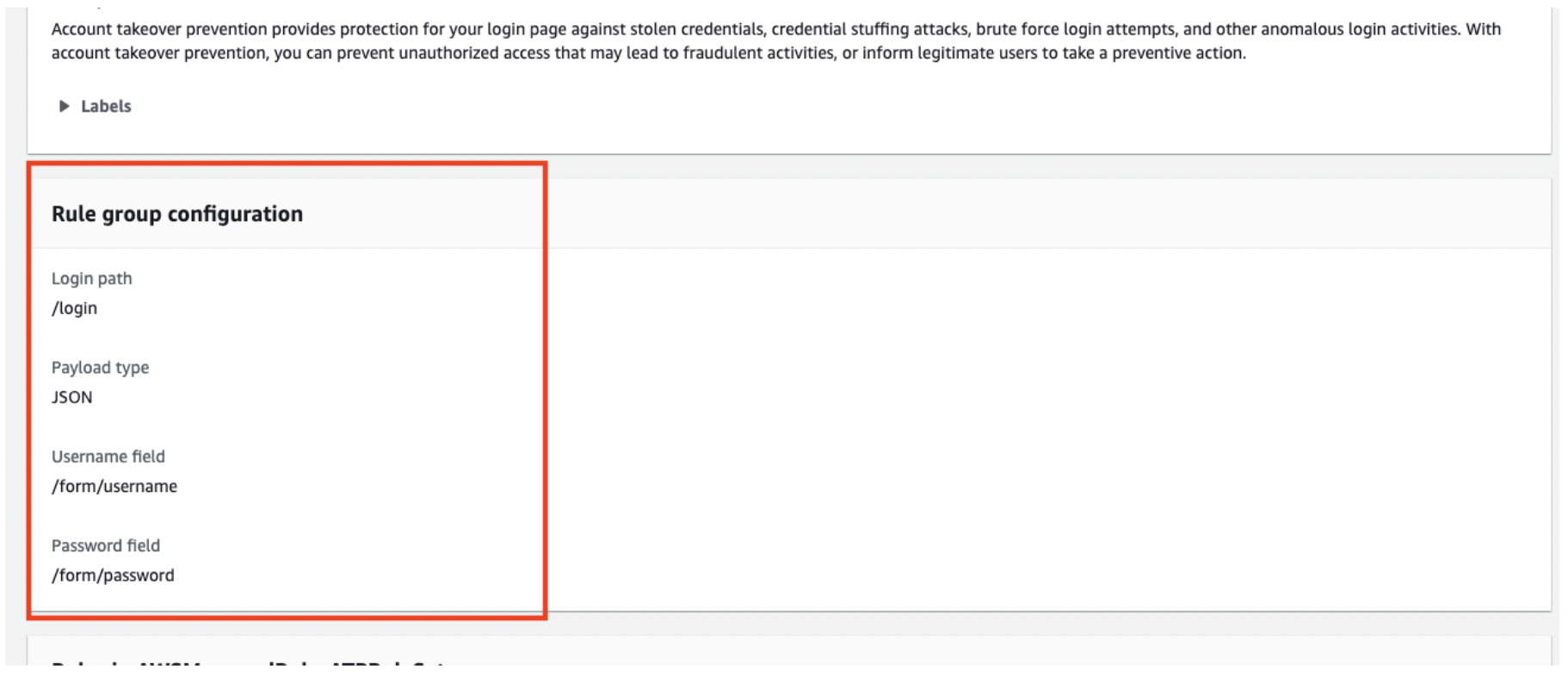
Although it is not required to do so, using the application integration feature will allow you to strengthen detection against automated attacks. Below is the official information.
The integration SDKs manage token authorization for your client applications, and help ensure that login attempts to your protected resource are only allowed after the client has acquired a valid token. Additionally, the SDKs gather information about the client to determine whether it's being operated by a bot or by a human being.
When you click on the “Application Integration SDKs” listed in the left menu, you can see the list of configurable ACLs.
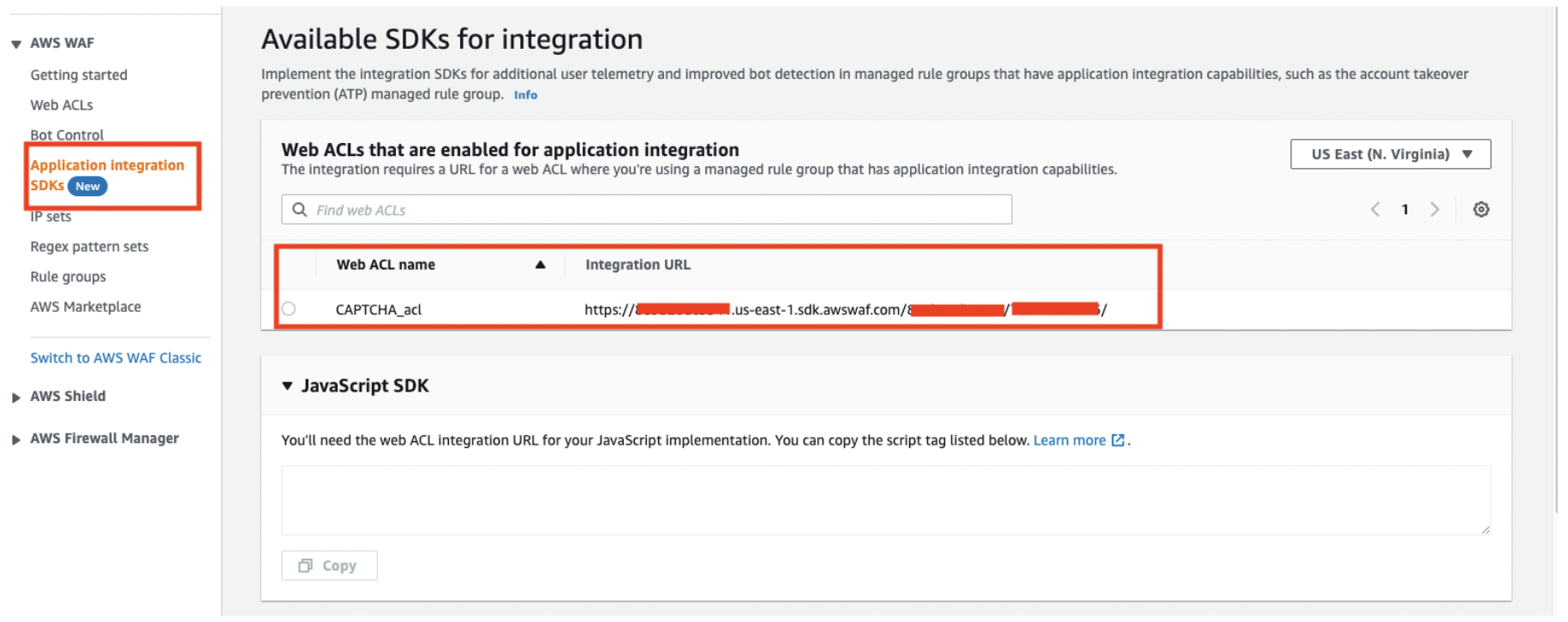
Code for JavaScript SDK will be generated when you select an ACL.
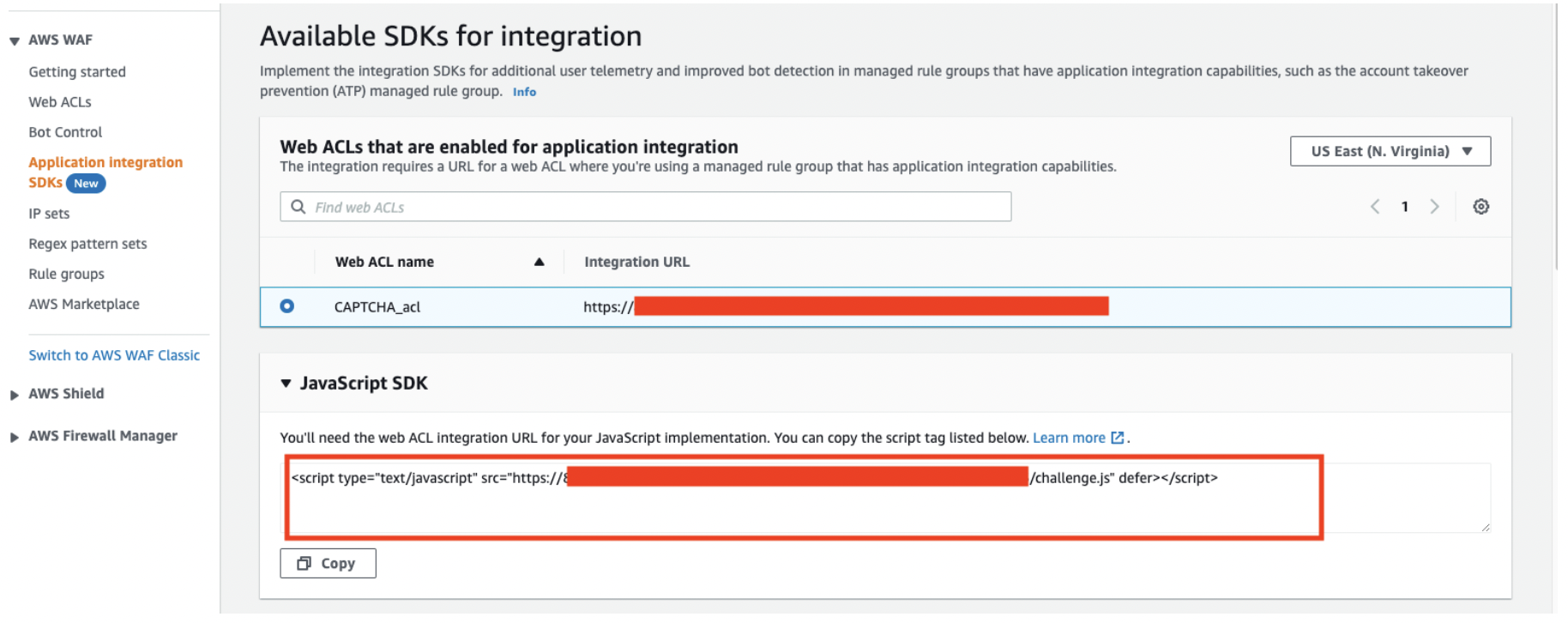
You can manage the token authentification by embedding it into the application.
Please refer to the official information for details.
*SDKs for Android and iOS mobile applications are available as well.
AWS WAF client application integration
4. Testing the rule
We tested the rule to see what kind of requests will be detected.
We prepared a simple testing environment that returns HTML using API Gateway and Lambda.
To demonstrate a case with incomplete information, we deleted the password property from the JSON file that was passed on and it was detected as MissingCredential. When password property was present but lacked the actual value, it was not detected.
To test the case for stolen credentials, you can use the account information provided by AWS. When we used this credential to test the rule, we could see that the intended label was applied and shown in the WAF log.
````
"labels": [
{
"name": "awswaf:managed:aws:atp:signal:credential_compromised"
}
]
````
We could also block the request by using the attached label and creating a subsequent rule.
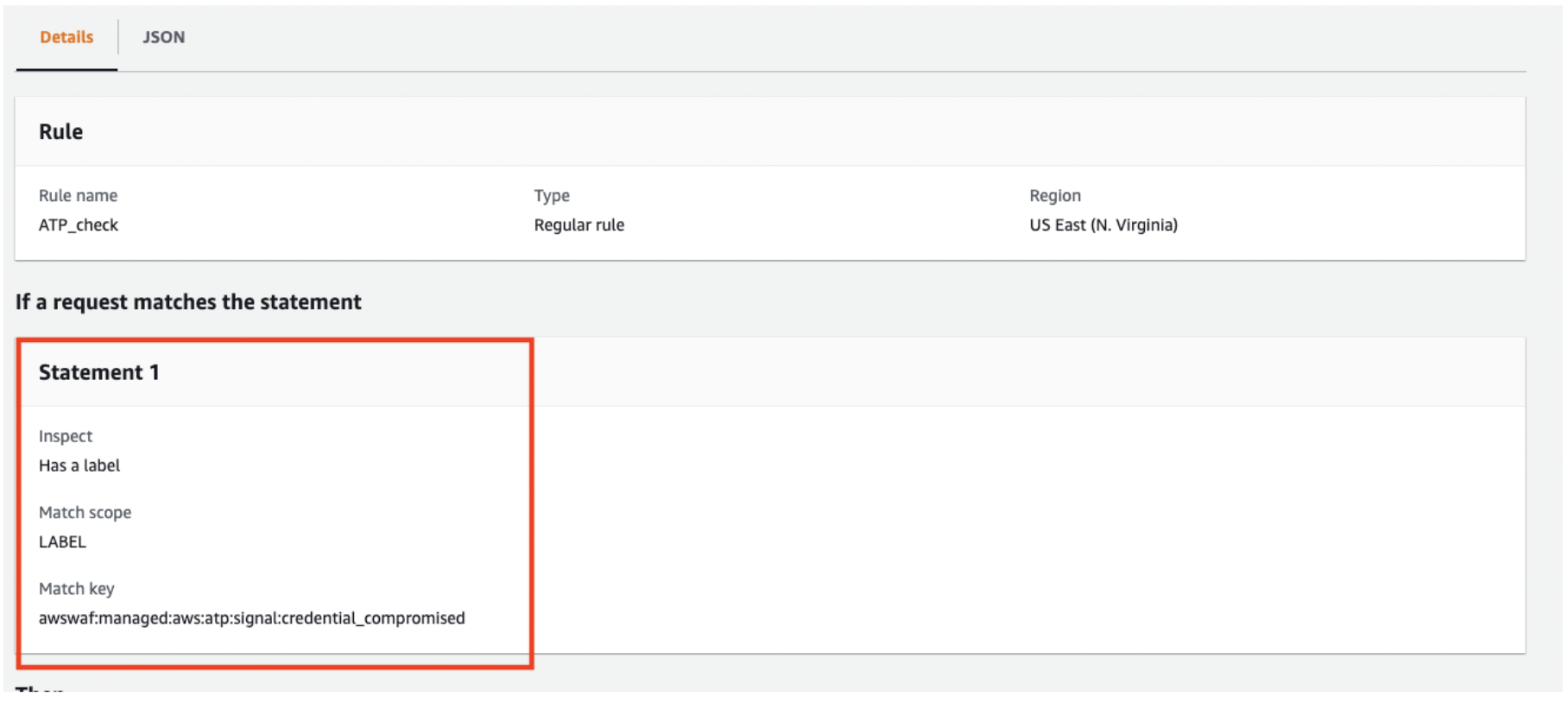
When we repeatedly accessed the environment with the same IP address, account, and password, it matched the VolumetricIpHigh rule. Labels have levels from low to high and the number of labels increased gradually.
````
"labels": [
{
"name": "awswaf:managed:aws:atp:aggregate:volumetric:ip:low"
},
{
"name": "awswaf:managed:aws:atp:aggregate:volumetric:ip:high"
},
{
"name": "awswaf:managed:aws:atp:aggregate:volumetric:ip:medium"
}
]
````
In the VolumetricIpHigh rule, you will be blocked once you reach the level high. If you want to stop the request at the low level, you can add a rule that uses the label after this labeling rule to have a strict policy.
However, there could be cases where requests come from the same site depending on the environment, so be careful when applying this setting.
We tried to detect requests with the AttributePasswordTraversal rule by using a fixed account and changing the passwords, but it was detected by the VolumetricIpHigh rule first, so we could not successfully test the rule with the same IP address.
For the application integration feature, we embedded JavaScript in the HTML set in Lambda and checked if tokens could be applied. We could see that the token was applied with a name “aws-waf-token” after accessing it from the browser.
````
{
"name": "cookie",
"value": "aws-waf-token=520afcXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX:XXXXXXXXXXXXXXXX:XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=="
}
````
It was stated that with application integration, it can assess if the operation was done by bots or humans, but there were no indications of test access, so we could not determine what kind of actions will be taken for this feature.
5. Effects on WafCharm
You can use the account takeover prevention (ATP) rule group with WafCharm rules.
6. Conclusion
We could see that the managed rule provided by AWS has lots of features for preventing fraudulent access that uses account information. It is a paid service, but we recommend them.
Please note that as of February 17th, 2022, it is not available in all regions.




