*This entry was originally written in Japanese in the past based on AWS WAF Classic.
Table of Contents
- Introduction
- Basic structure of AWS WAF
- How to protect web application with AWS WAF
- Requests you can allow/block in AWS WAF
- How to block on AWS WAF
- Conclusion
Introduction
We have introduced specific settings and procedures of AWS WAF in the blog posts before, but it is important to understand how AWS WAF works for advanced usage. In this three-part series, we will look at topics from basic structure to ways to utilize Condition and Filters to block requests on AWS WAF.
- Part 1: AWS WAF Classic Explained - Basic Structure (this post)
- Part 2: AWS WAF Classic Explained - Relationship between Conditions and Filters
- Part 3: AWS WAF Classic Explained - Structure of string and regex matching and examples usage
Basic structure of AWS WAF
First, let’s take a look at the big picture. AWS WAF’s structure is shown in the figure below.
Structure of AWS WAF
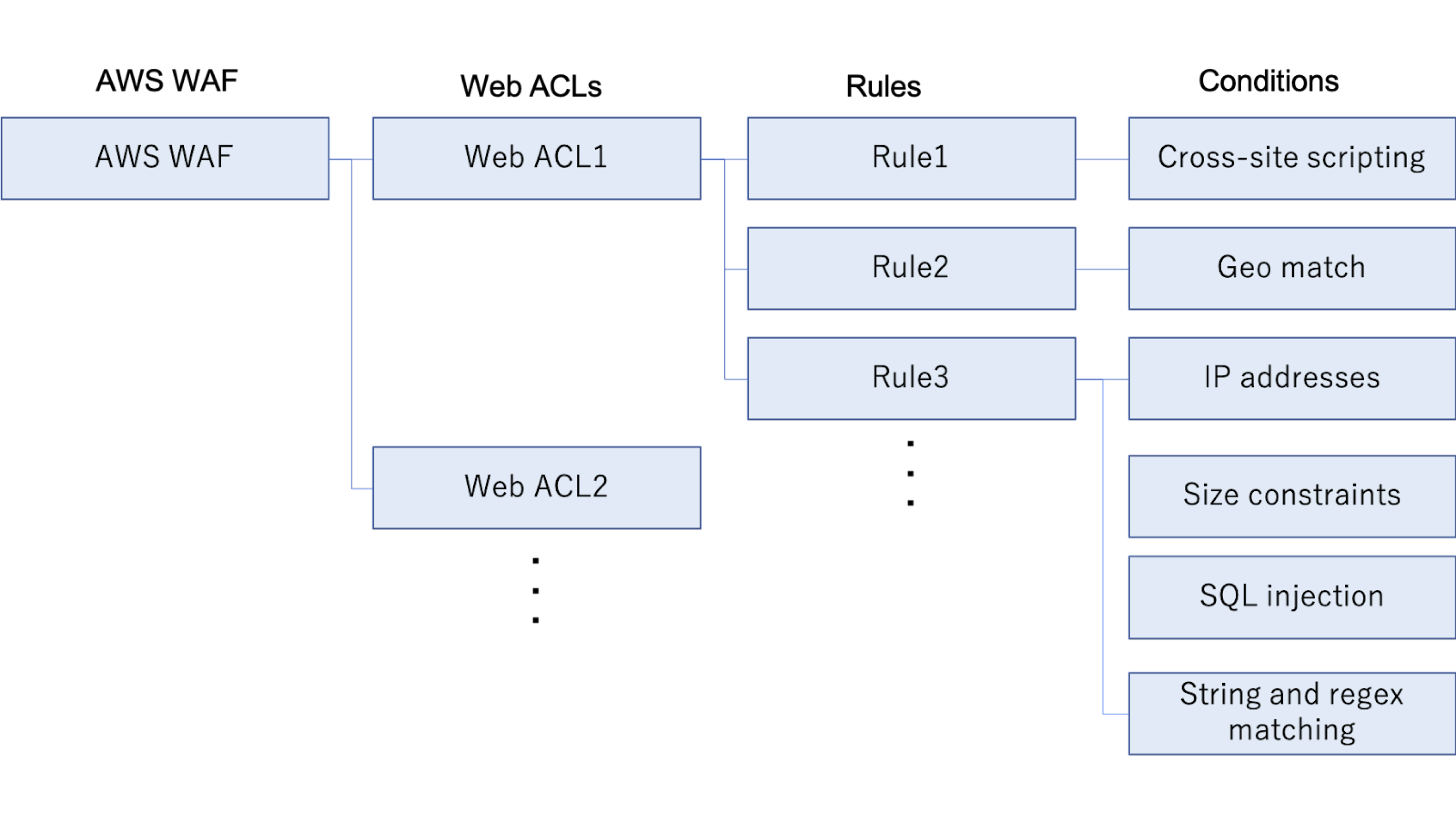
AWS WAF
- Web Application Firewall provided by AWS
- Protect L7 (HTTP/HTTPS) application layer
- Regulate accesses by Web ACL
- Protects against web application specific attacks like SQL injection and XSS
Web ACL
- Apply rules with web access control list
- 10 rules can be attached to one web ACL
- CloudFront, ALB and API Gateway can be attached to Web ACL for usage
Rules
- Apply Conditions that indicate specific requirements
- Up to 10 conditions can be applied to one rule
Conditions
- Define specific conditions of attacks you want to prevent
- Conditions for SQL injection and XSS are provided by AWS
- Conditions for application-specific attacks have to be stated separately
How to protect web application with AWS WAF
By following the AWS WAF Classic Explained posts, you can achieve five points in AWS WAF explained below.
- Create a condition based on the purpose of access control
- Create a rule that includes the created condition
- Create a Web ACL to apply rules
- Apply rules to the created Web ACL
- Apply Web ACL to either CloudFront, ALB, or API Gateway
This post is an introduction to AWS WAF, so if you can picture the nested relationships of each element, you’ll be good to go.
Requests you can allow/block in AWS WAF
In AWS WAF, you can allow or block the types of requests explained below.
It is important to select the rules according to your website’s purposes because there is a limit to the number of rules you can apply to one Web ACL in AWS WAF.
For the limitations, refer to the official document: AWS WAF Classic quotas
- Requester’s IP address matches a specific IP address or range of IP addresses
- Requester’s IP address is from a certain country
- Matching string in certain part of the request (regex is available)
- Length of specified parts of requests exceeds the set limit
- SQL injections or XSS is contained in requests
How to block on AWS WAF
For specific procedures to block requests, refer to the blog posts below.
- How to Block SQL Injection Attacks with AWS WAF
- How to Block a Request that Contains a Specific String in URI with AWS WAF
- Block Attacks from Specific IP Addresses in AWS WAF
Conclusion
We hope you can deepen your understanding of AWS WAF Classic.
In the next post, we will focus on Conditions and Filters, the core elements of blocking attacks, to explain AWS WAF’s structure.
Next post:
Next post: AWS WAF Classic Explained: Part 2 Relationship between Conditions and Filters



