【Overview】
In this blog, we will show how to create a rule that blocks requests including typical SQL injection attack patterns and check if it is actually blocked.
【Creating a Condition】
1. Select "SQL injection" from the AWS WAF console.
2. Click “Create condition”.
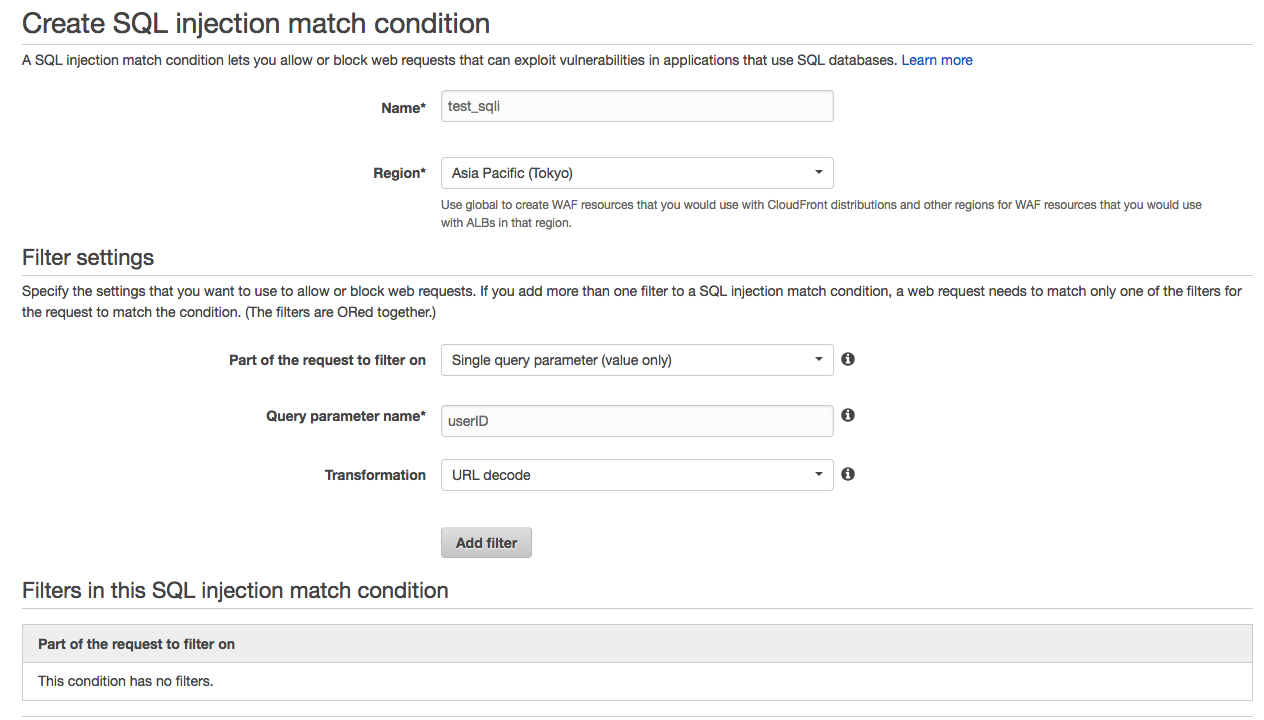
3. On the next screen, perform the following steps:
・Name*:Enter an arbitrary name. We will use "test_sqli".
・Part of the request to filter on:Select "Single query parameter (value only)".
・Query parameter name*:Select "userID".
・Transformation:Select "URL decode".
・Click "Add Filter" to add the condition.
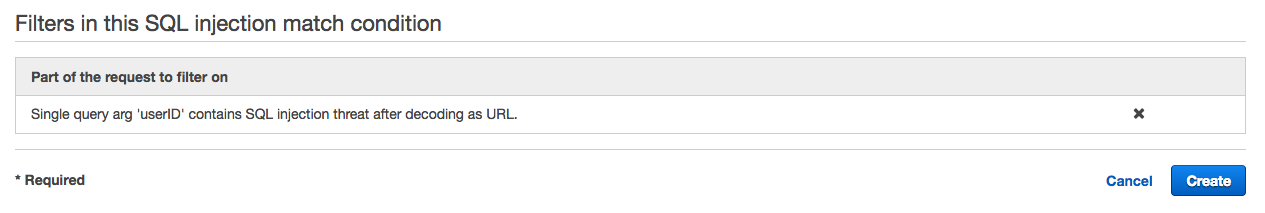
4. Confirm the addition of filter in "Filters in this SQL injection match condition" and click "Create".
5. Condition is created.
【Creating a Rule】
1. Select “Rules” from the AWS WAF console.
2. Click "Create rule".
3. On the next screen, perform the following steps:
・Name*:Enter an arbitrary name. We will use "test_rule_sqli".
・Rule type*:Select "Regular rule".
・Under "When a request", select “does” / “match at least one of filters in the SQL injection match condition".
・Select the condition "test_sqli" you created earlier.
・Make sure that the contents of the conditions is reflected and click "Create".
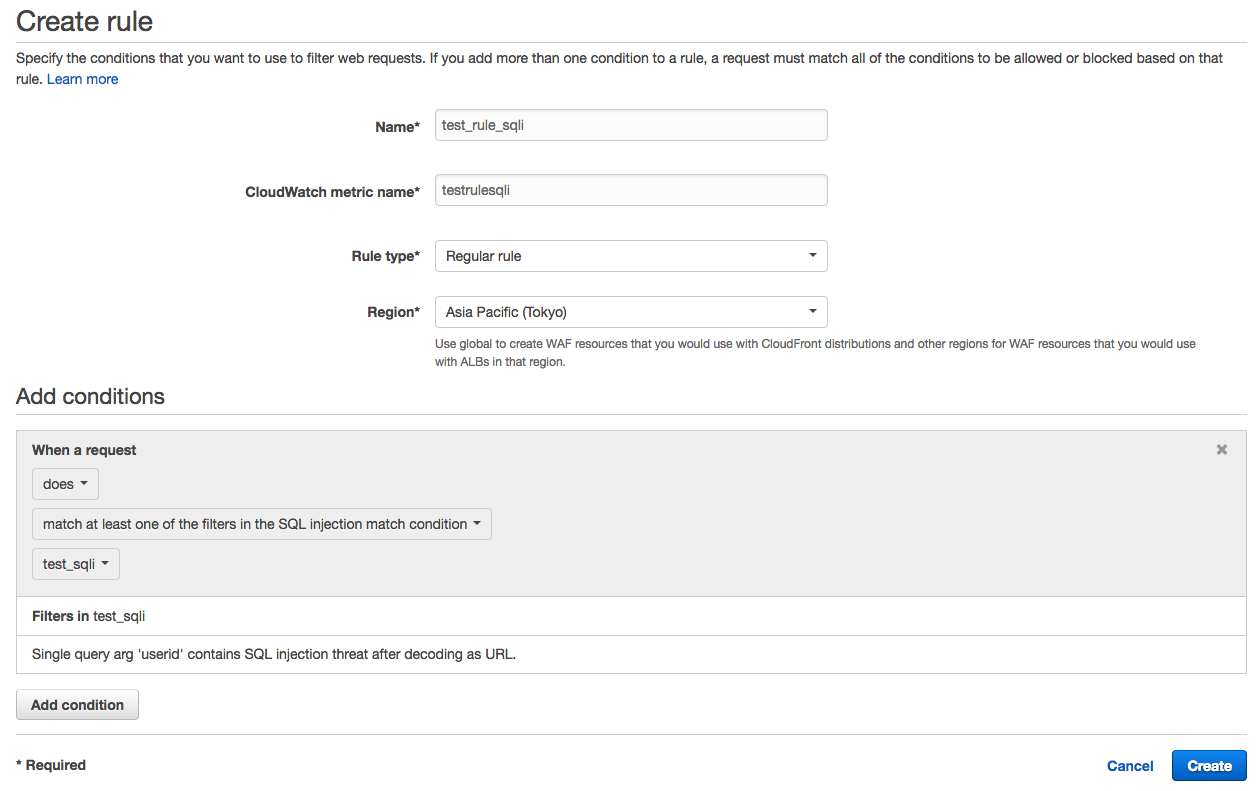
4. Rule is created.
【Adding to the ACL (Access Control List)】
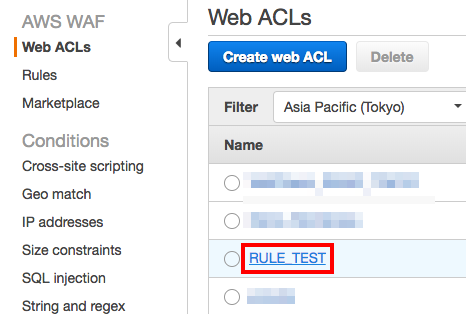
1. Select “Web ACLs” from the AWS WAF console and click the target Web ACL.
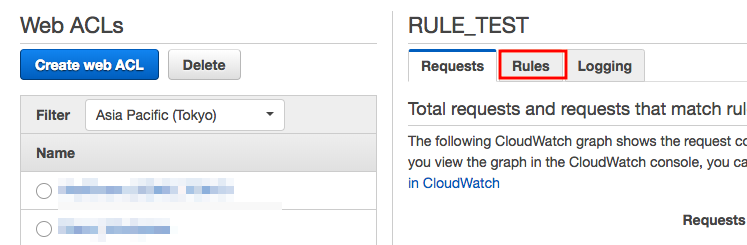
2. Select the "Rules" tab.
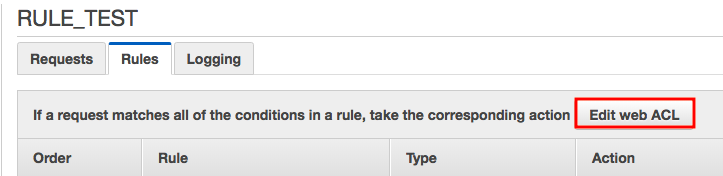
3. Click "Edit web ACL".
4. Select the rule "test_rule_sqli" you created earlier and click "Add rule to web ACL".
Under "If a request matches all the conditions in a rule, take the corresponding action", select “Block” for action for this rule.
Next, for "Default action", select "Allow all requests that don't match any rules" and click "Update".
※ "Default action" is an action for the requests that don't match any rules and can be set as "Allow" or "Block".
Please not that if this is set to "Block", all requests except those allowed by the rules will be blocked.
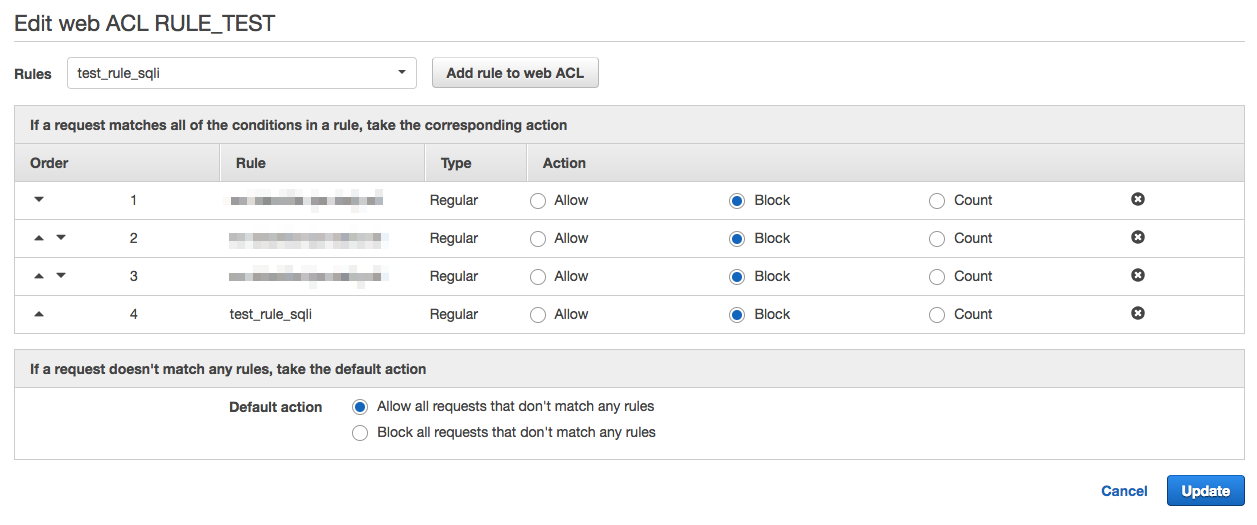
5. Rule will be added to the Web ACL.
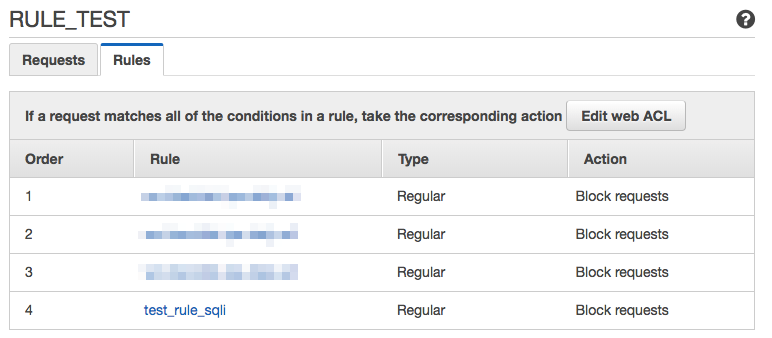
6. Now, let's actually test it.
We applied the rule and accessed「http://example.com」.
We were able to access without any problems.
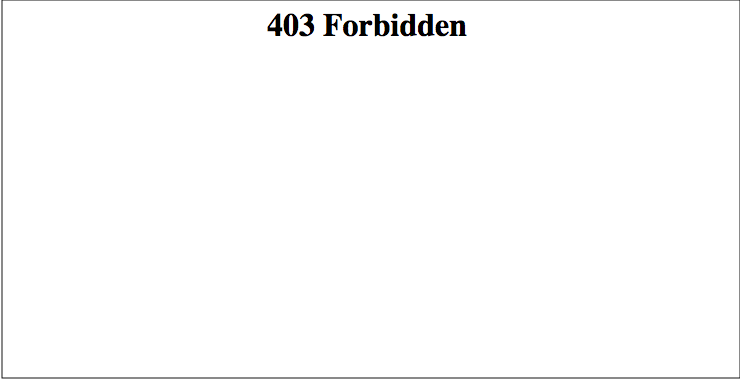
7. Next, when we try to access the same with an SQL injection,
「http://example.com/?userID=20%27%20 or% 20% 271% 27% 3d% 271」,
a "403 Forbidden" error was returned.
【Summary】
This time we introduced a method to set a rule to block SQL injection attacks in AWS WAF.
It's a very simple rule, but we showed how to use AWS WAF to block requests that contain specific query characters in the URI.
If you think "WAF is confusing", try for yourself.



