Table of Contents
- 1. Introduction
- 2. Example 1: service is only available in certain conditions
- 3. Example 2: requests from admin users are falsely detected
- 4. Example 3: other requests to allow
- 5. Conclusion
1. Introduction
In a past blog post, we looked at how to use the label feature to exclude specific URIs from inspection in AWS WAF.
How to use the label feature in AWS WAF
In this blog post, we will take a look at other examples of to allow specific requests.
2. Example 1: service is only available in certain conditions
If you are providing the service under specific conditions, you can create a rule to restrict access and use managed rules together.
In the examples below, we will look at restrictions based on country code and IP address.
Restriction based on country
Apply a rule to block requests from non-specified countries and managed rules if you are only providing services in a certain country.
If you want to restrict the country and block any suspicious requests, using the rules and priorities below is effective.
- A rule to block any countries that are not specified
- Managed rules
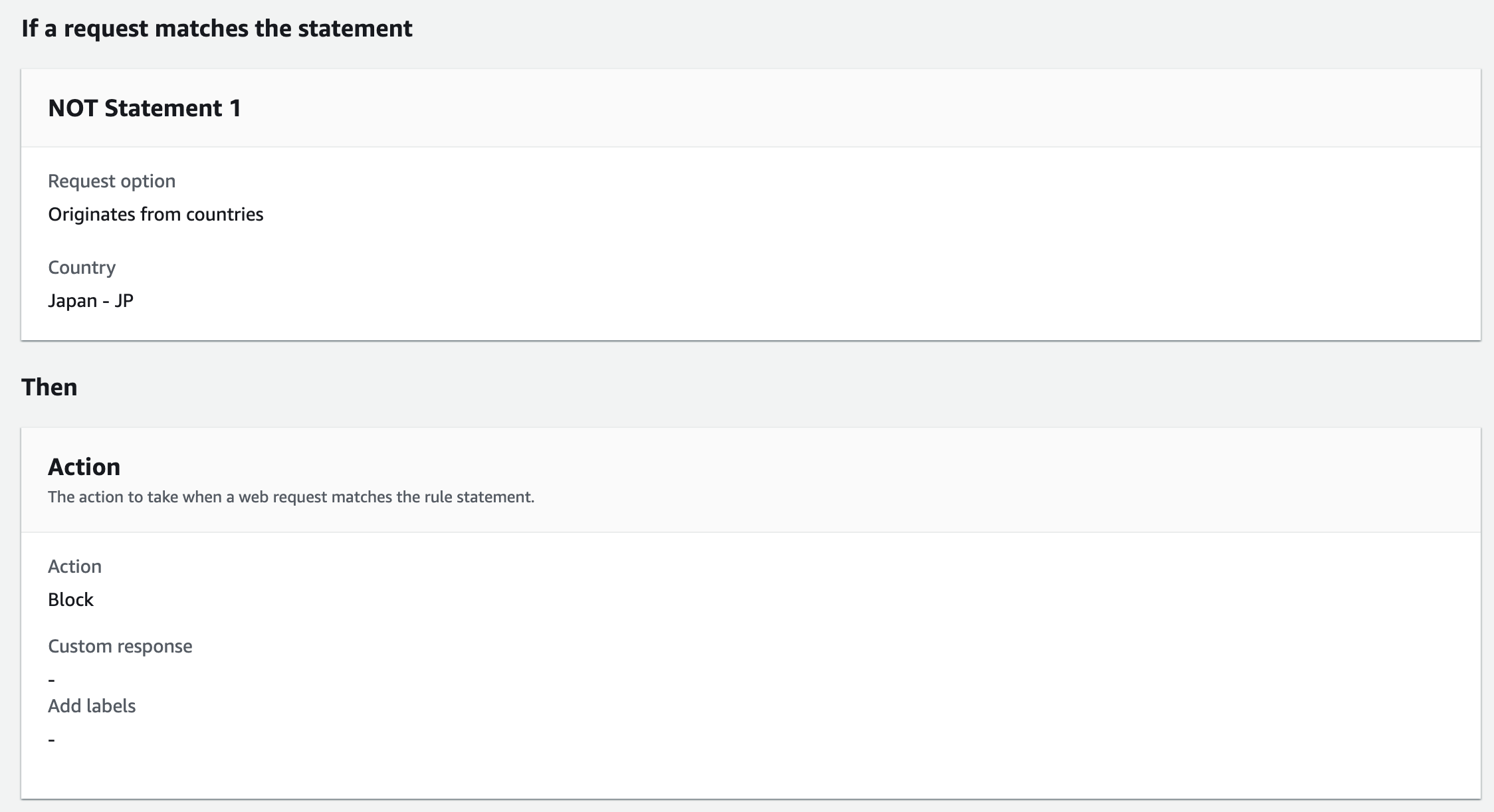
Use Not Statement and geo match statement for a rule to block any countries that are not specified.
Example of the conditions for use:
- If a request: doesn't match the statement (NOT)
- Inspect: Originates from a country in
- Country codes: Japan - JP
- IP address to use to determine the country of origin: Source IP address
- Action: Block
Restriction based on IP address
If you want to allow access only from specific IP addresses, apply a rule that blocks requests from IP addresses that are not specified in the rule.
The rule and the priority will be the same as above.
- A rule to block any IP addresses that are not specified
- Managed rules
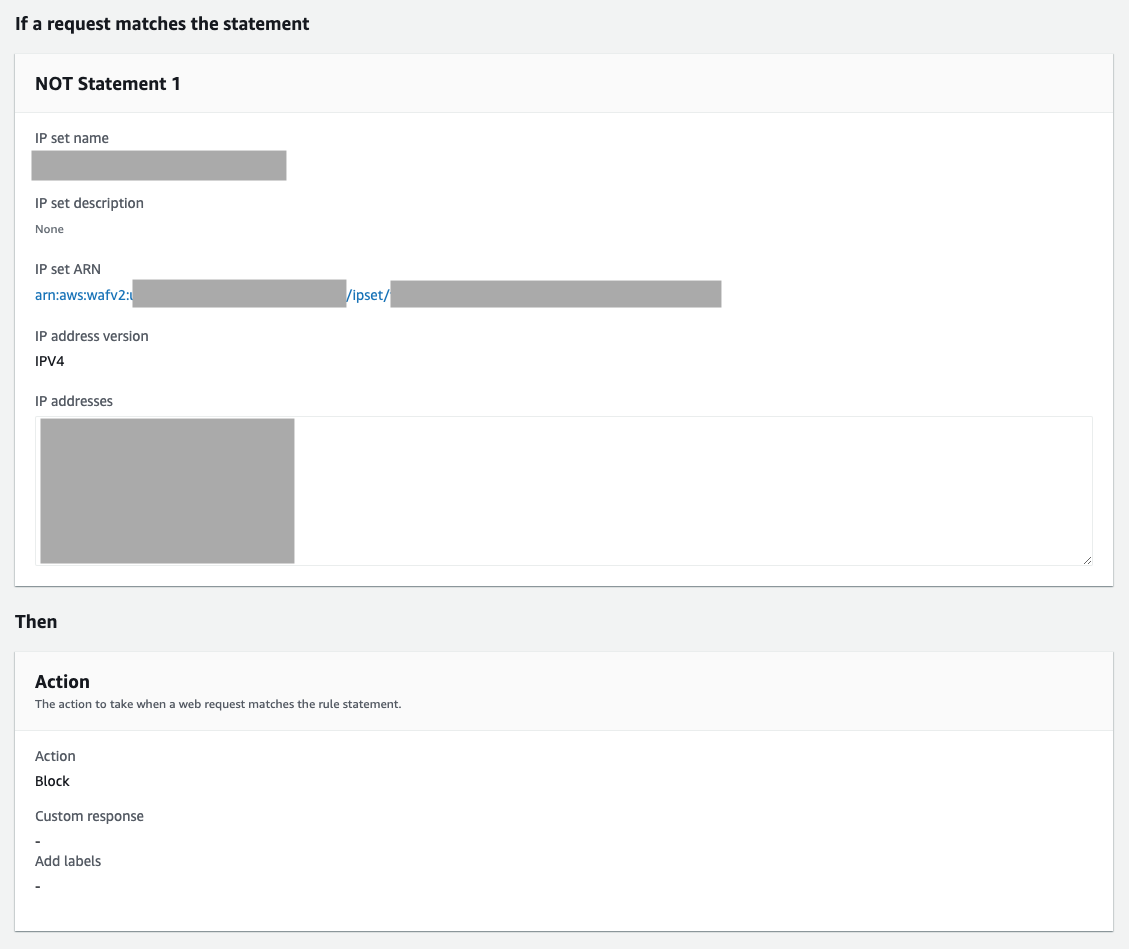
In this case, you must create IP sets first unlike geo match statement. Refer to the AWS document Creating and managing an IP set on how to create IP sets. After you've created your IP sets, choose the options below to create the rule.
Example of the conditions to use:
- If a request: doesn't match the statement (NOT)
- Inspect: Originates from an IP address in
- IP set: Name of your IP set
- IP address to use to determine the country of origin: Source IP address
- Action: Block
Please keep in mind that the rules above expect that the default web ACL action (Default web ACL action for requests that don't match any rules) is set to ALLOW.
*This means that any requests that don't match the rules will be allowed.
If you want to block everything and explicitly allow certain requests (based on IP addresses), select BLOCK for the default web ACL action and apply the rules/priorities below.
- Managed rule
- A rule to allow IP addresses that are specified
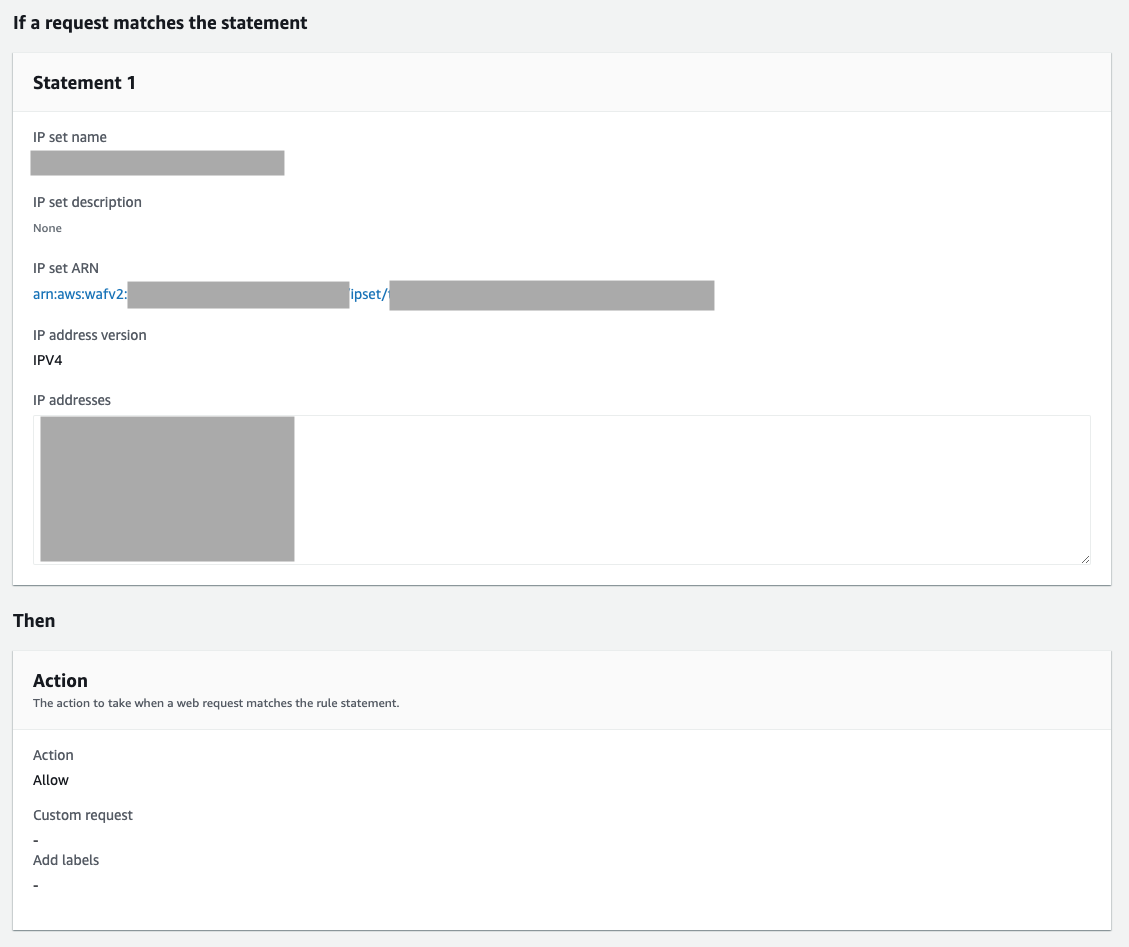
Example of the conditions to use:
- If a request: matches the statement
- Inspect: Originates from an IP address in
- IP set: Name of your IP set
- IP address to use to determine the country of origin: Source IP address
- Action: Allow
3. Example 2: requests from admin users are falsely detected
Requests from administrators (admin users) during updates etc., could match the WAF rules unexpectedly. Let's consider a way to exclude such requests from the specific rule that matches admin users' requests.
Here are three examples in this post.
We have a similar scenario explained in the blog post below, so please refer to it as a reference as well.
How to use the label feature in AWS WAF
Admin permissions are usually given to limited users and have specific IP addresses, so the first example is going to be based on the IP addresses. Managed rules provided by AWS have a label for each rule, so we are going to use AWS Managed Rules and IP addresses in this case.
The rule and priority is as below.
- Managed rules
Change the rule action of the rule that matched the admin users' requests to COUNT - A label of the said rule & a rule to block IP addresses that are not specified
The second rule [Label of the said rule & a rule to block IP addresses that are not specified] must be added after you've changed the rule action of the matched rule in managed rules to COUNT.
To change the rule action of the rule in managed rules, refer to Overriding rule actions in a rule group to override the action.
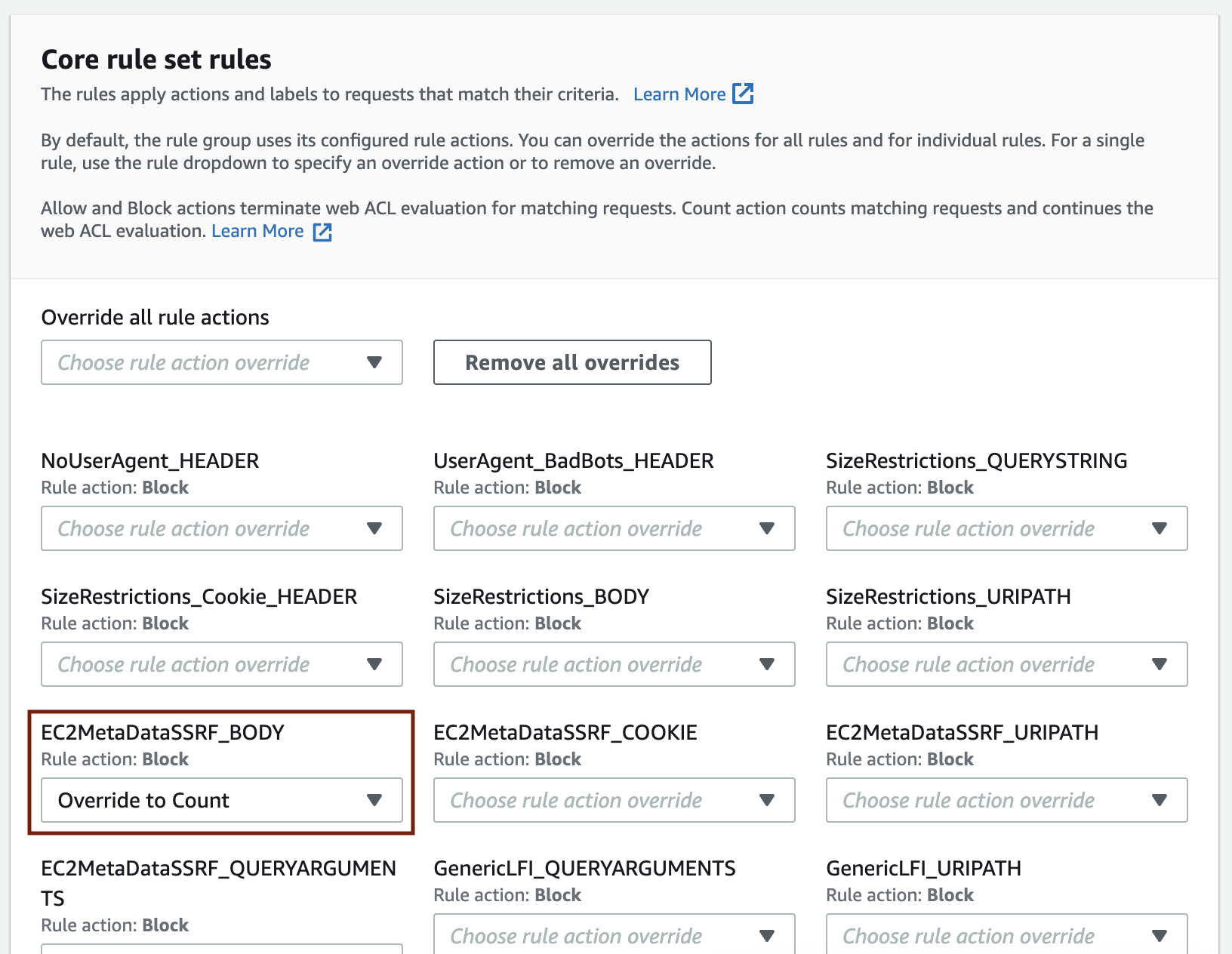
In addition, the second rule [A label of the said rule & a rule to block IP addresses that are not specified] uses IP addresses as part of a condition, so you must create an IP set beforehand. For labels, use the drop-down menu to choose the label or type in the rule name to find the correct label.
Example of the conditions to use:
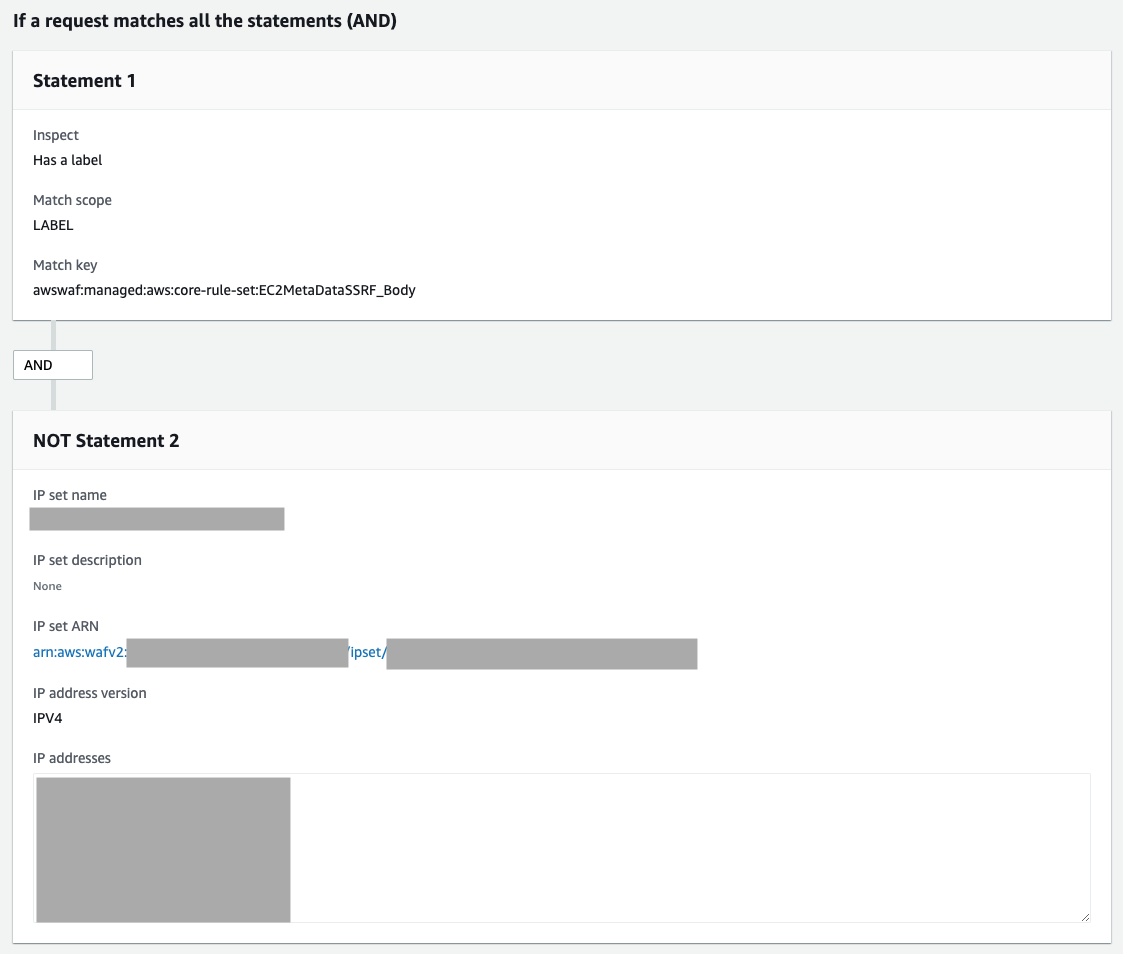
- If a request: matches all the statements (AND)
- First condition
- Inspect: Has a label
- Match scope: Label
- Match key: awswaf:managed:aws:core-rule-set:EC2MetaDataSSRF_Body
- Second conditions
- Negate statement (NOT): Checked
- Inspect: Originates from an IP address in
- IP set: Name of your IP set
- IP address to use to determine the country of origin: Source IP address
- Action: Block
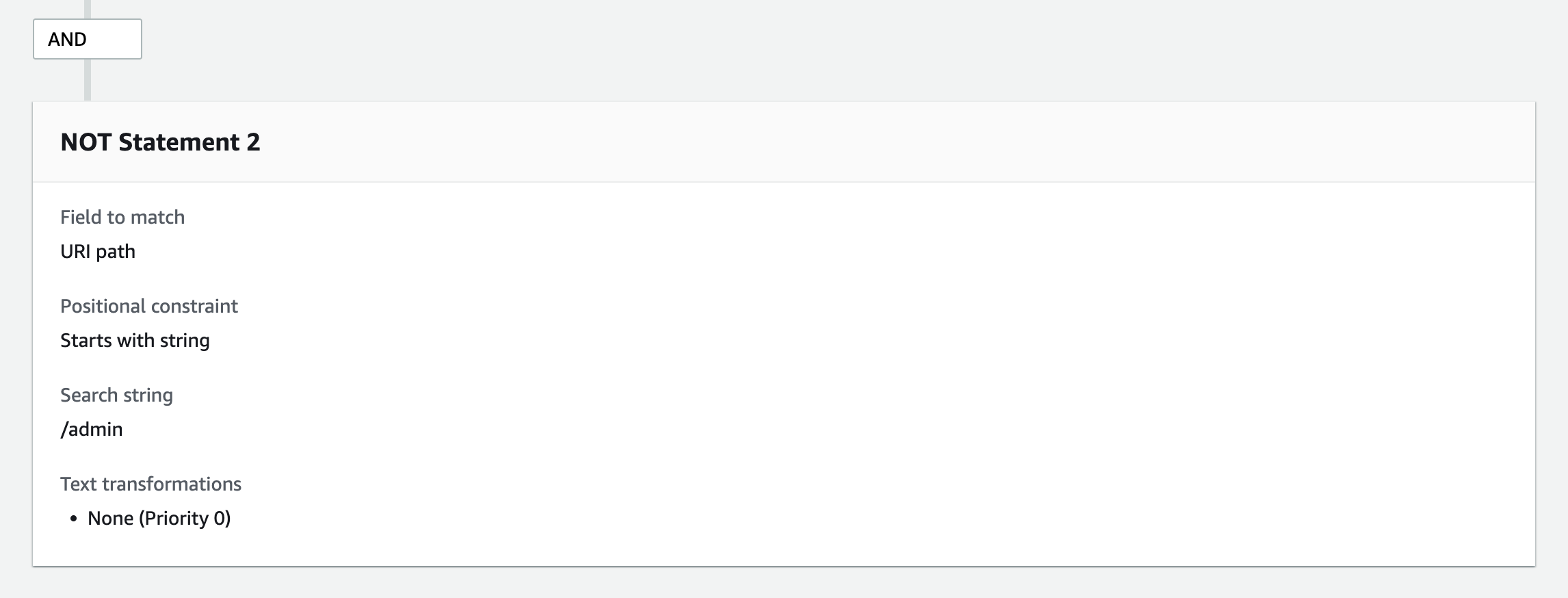
The second example is to exclude with URI when the admin pages are provided under specific URI paths and end users are not allowed to access them.
The method is the same as IP addresses; the difference here is that URI is used in the condition instead of IP addresses.
- Managed rules
Change the rule action of the rule that matched the admin users' requests to COUNT - A label of the said rule & a rule to block pages under specific URI paths that are not specified
To specify URI, choose [URI path] under the [Inspect] field.
String match rule statement must be specified for URI as well. If the admin pages are provided under a specific URI path, the URI is likely to start with a specific URI string. In that case, use the [Starts with string] option. If the specific string is always available somewhere in the URI, use the [Contains string] option or regular expressions.
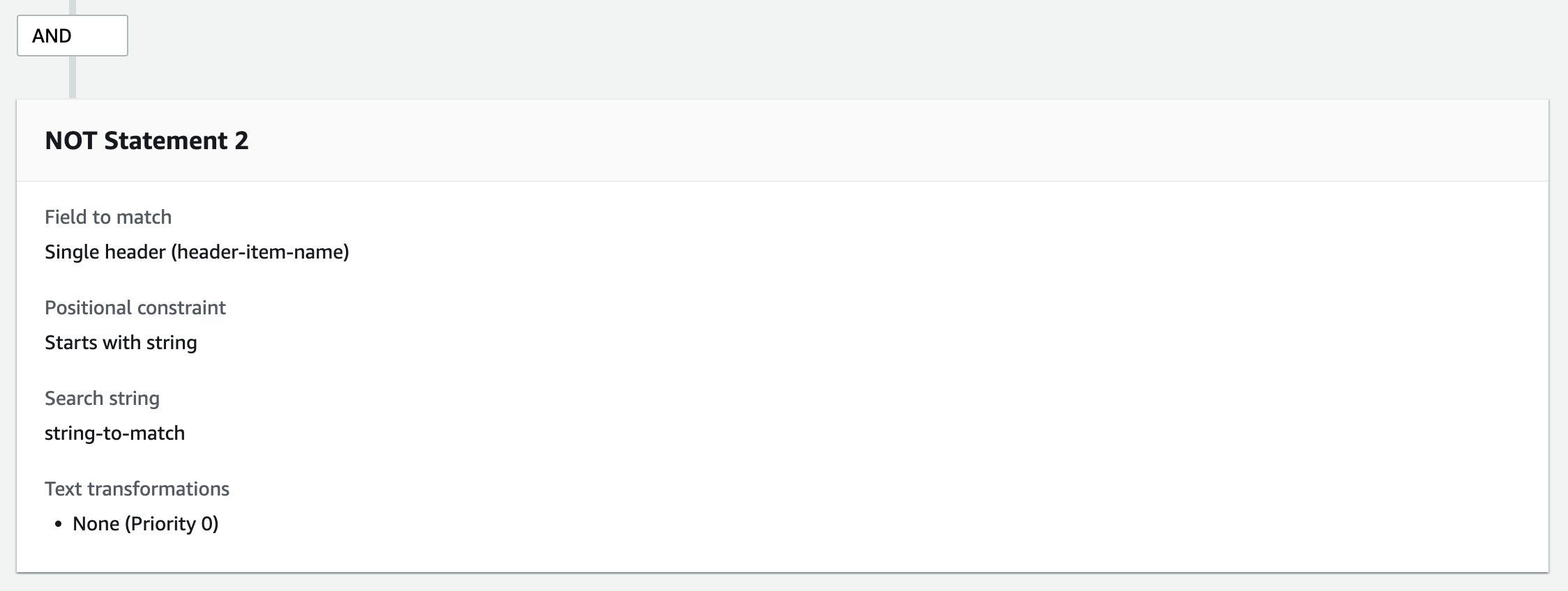
The third example is to use headers if requests made by admin users contain specific headers.
- Managed rules
Change the rule action of the rule that matched the admin users' requests to COUNT - A label of the said rule & a rule to block specific headers that are not specified
Headers use the same methods as IP addresses and URI paths. Select [Single header] under the [Inspect] field and enter header key and value.
4. Example 3: other requests to allow
If your environment only has one WAF that inspects accesses to multiple hosts, you may want to adjust the settings if a specific host is for unique environment or temporarily exclude a specific host from WAF inspection.
In such cases, you could use methods below.
Allow specific host
In this method, you will be allowing all requests with the specified host with top priority, so the requests are not inspected by following rules and can be excluded from WAF inspection.
- A rule that allows requests to a specific host
- Managed rules
You can create a rule that allows requests to a specific host like below.
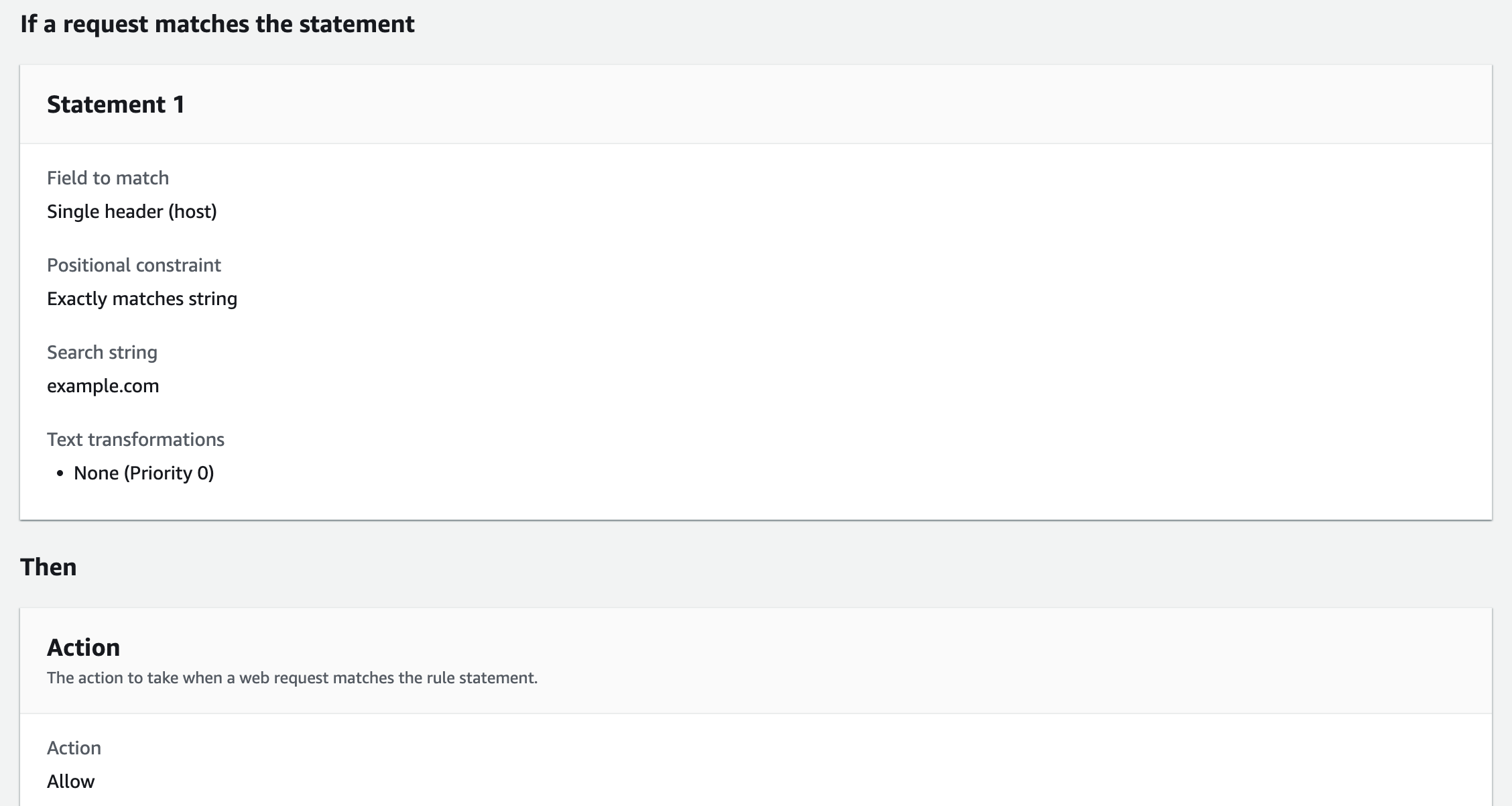
Example of the conditions to use:
- If a request: matches the statement
- Inspect: Single header
- Header field name: host
- Match type: Exactly matches string
- String to match: example.com
- Action: Allow
Exclude specific host
This is the same as the third example in the [Example 2: requests from admin users are falsely detected] section that uses headers.
When excluding requests from all rules in the managed rules, use the namespace instead of a single label as shown below.
awswaf:managed:aws:core-rule-set:
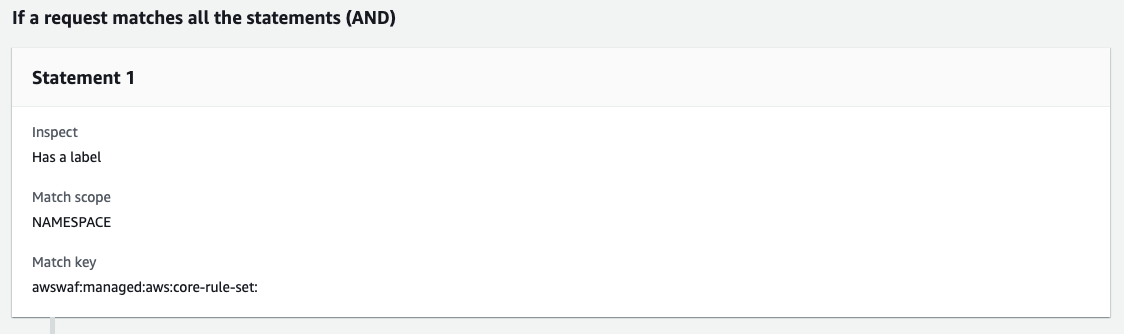
However, this method may make it difficult for you to figure out which rule detected the requests. To make the investigation easier, it might be better to create a new rule [A label of the said rule & a rule to block host headers that are not specified] for each rule in the managed rules.
This may not be realistic if there are a lot of rules in the managed rule because you will have to add many rules for exclusion, but this method may be helpful if you want to exclude from most of the rules in the managed rules but want to keep a few of them to inspect the requests.
Using scope-down statement
Although you cannot adjust the signatures of each rule in managed rules, you can narrow down the requests that are inspected by the entire set of manage rules by using scope-down statement.
Scope-down statement can be used with managed rules provided by both AWS and third-party vendors subscribed via AWS Marketplace.
Under the [Rules] tab, check the managed rule you want to exclude the host from and click [Edit] to see the scope-down statement section. Select [Only inspect requests that match a scope-down statement] to specify conditions.
Example of the conditions to use:
- If a request: doesn't match the statement (NOT)
- Inspect: Single header
- Header field name: host
- Match type: Exactly matches string
- String to match: example.com
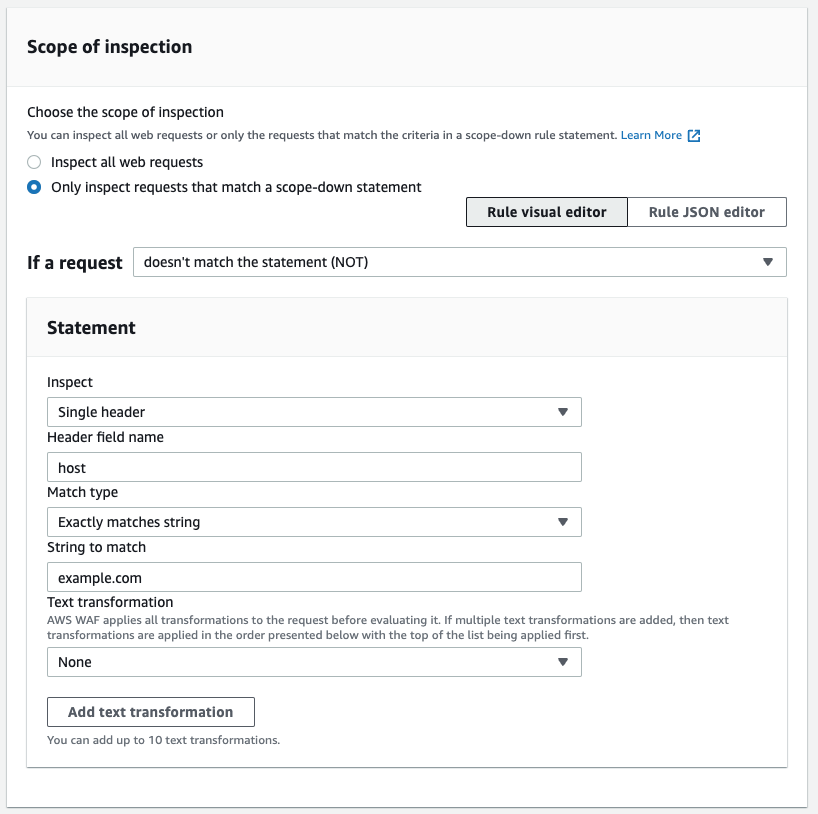
Since this is a scope-down statement, you don't have to specify an action. Most managed rules will block requests that match the rules, so to exclude specific requests, use Not Statement.
If the conditions for requests you want to inspect with WAF are limited (i.e., you want WAF to inspect just one host), you can select the [matches the statement] option in the [If a request] field to create a rule that only inspects a specific host.
5. Conclusion
Because managed rules do not allow users to edit the signatures of each rule, users are required to utilize exclusions using labels and other methods when allowing specific requests.
The effective methods are different based on each situation, so please refer to the examples above to choose the best method to allow requests for your environment.




