Table of Contents
- 1. Introduction
- 2. What is the SQL injection attack rule statement?
- 3. Configuration procedure
- 4. Effects on WafCharm
- 5. Conclusion
1. Introduction
On July 5th, 2022 (PTD), AWS WAF documentation was updated to include a new sensitivity level setting for the SQL injection attack rule statement. We are going to take a look at how to implement the sensitivity level setting.
2. What is the SQL injection attack rule statement?
In AWS WAF, you can use regular expressions to create your own rules. However, AWS WAF also provides rule statements to detect SQL injection attacks for easy usage in case you cannot create your own rules.
You can detect SQL injection attacks by selecting part of the requests to inspect (i.e., body) and the SQL injection attack rule statement in the match type.
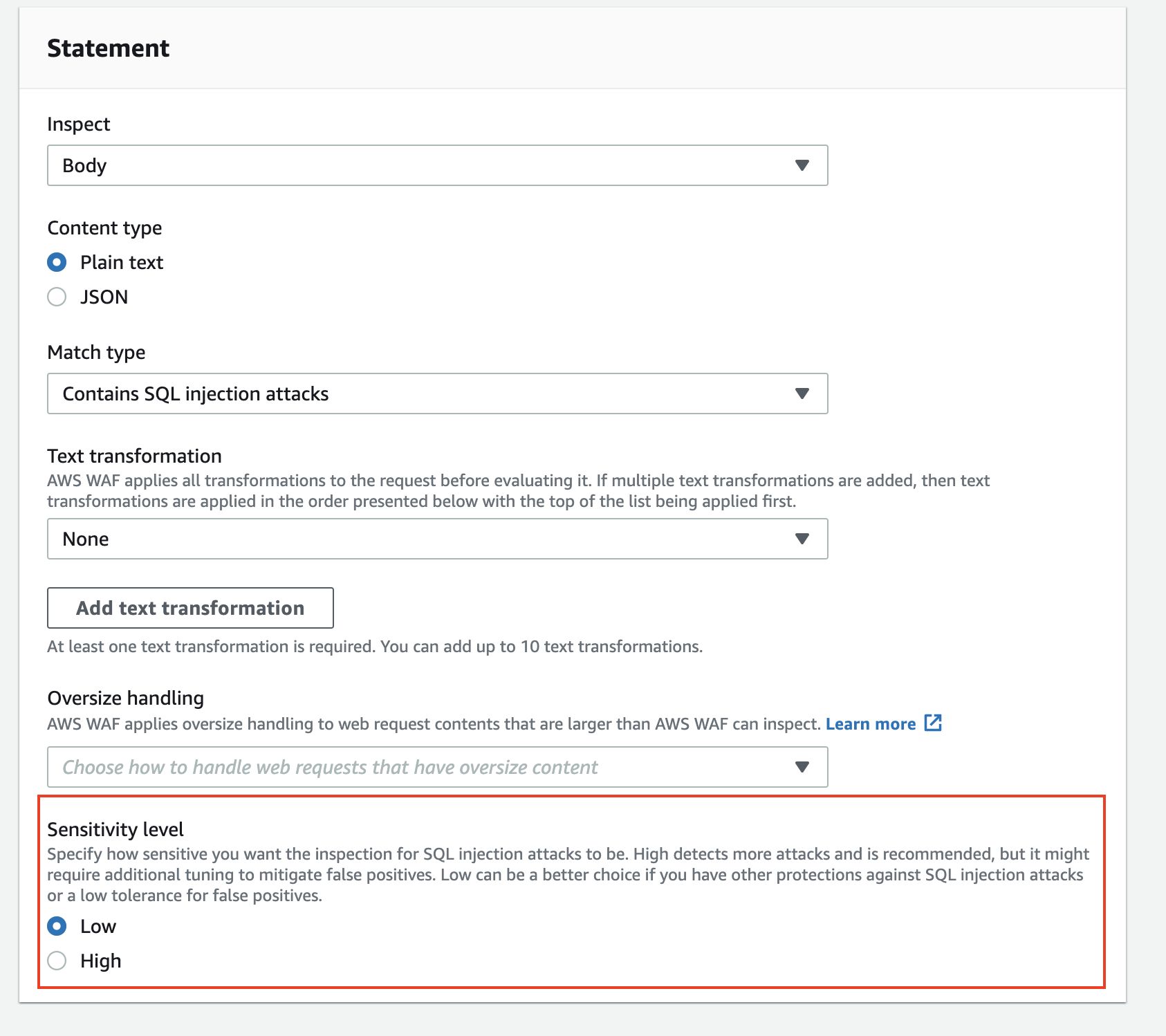
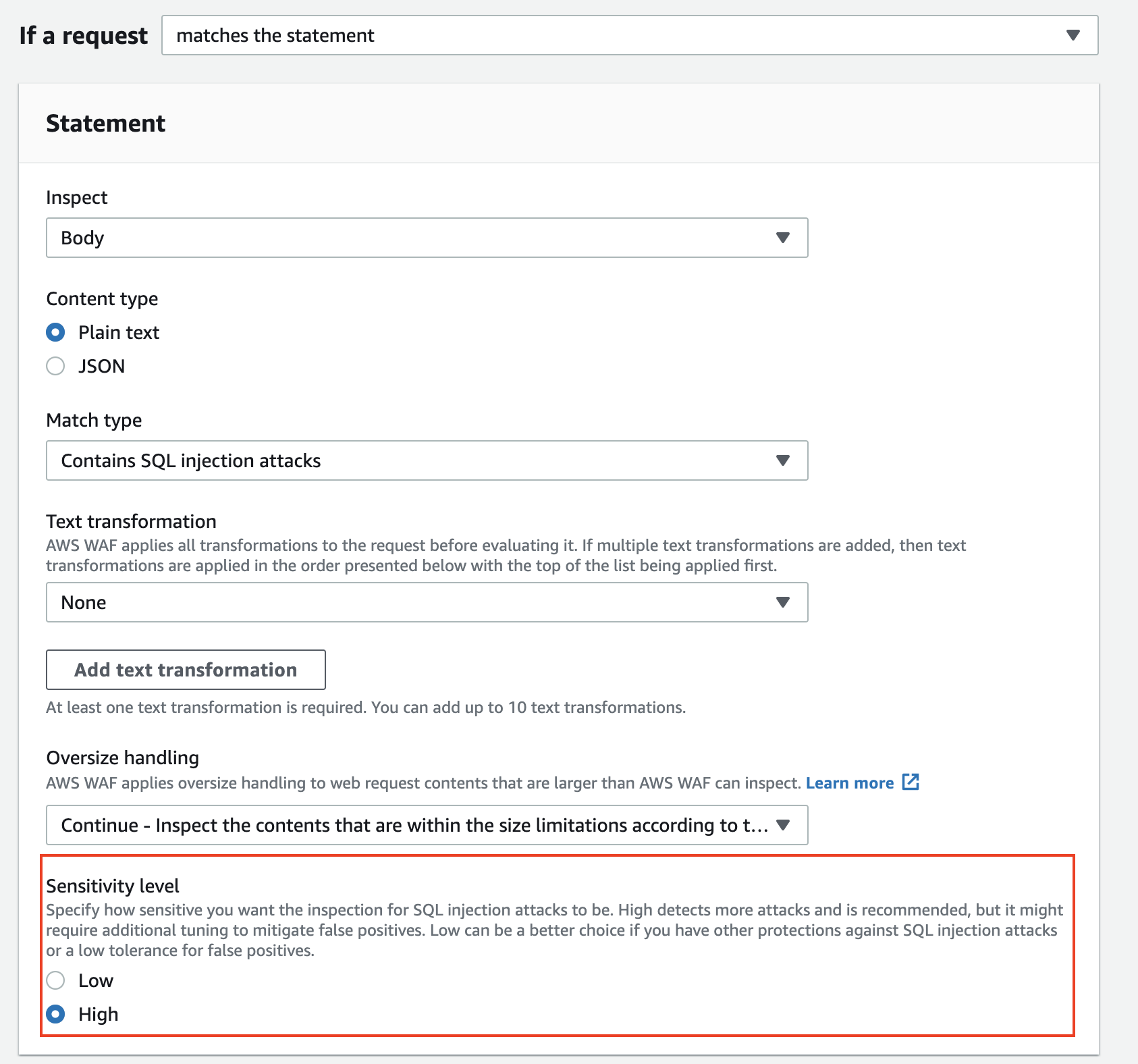
The sensitivity level options provided by this update are LOW or HIGH.
The option LOW is selected by default, but you can also select HIGH to accommodate more patterns.
However, increasing the probability of detection could lead to increased false positives. That seems to be why they have provided the users the option to choose the sensitivity levels to allow adjustments.
3. Configuration procedure
In this post, we will create a rule to detect the SQL injection attack in the body of the requests.
Open your Web ACL and click the “Add your own rules…” button.
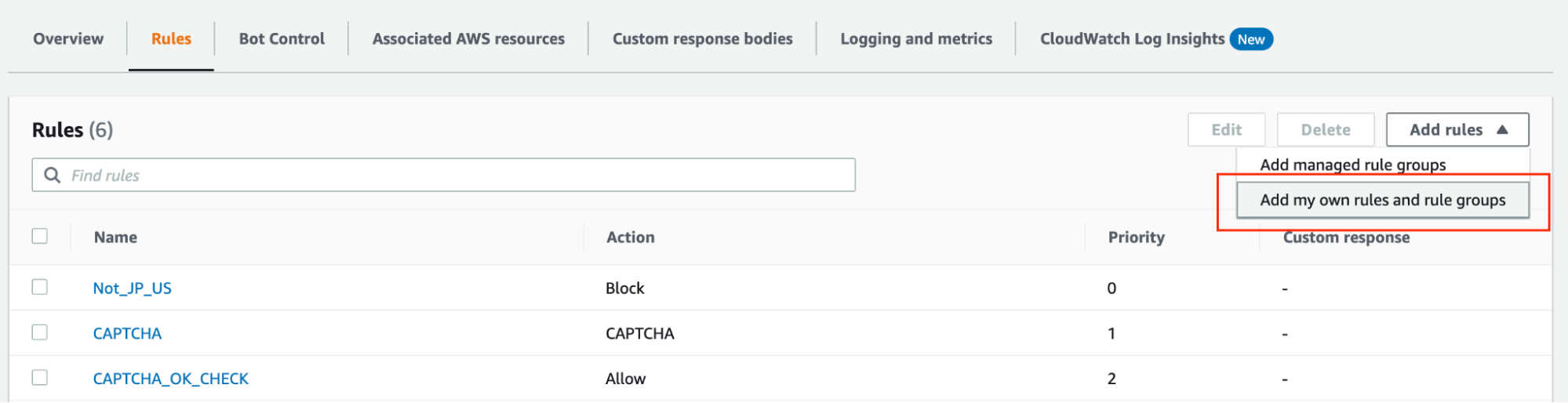
After you enter a rule name, select “Body” in the Inspect field and “Contains SQL injection attacks” for the Match type field.
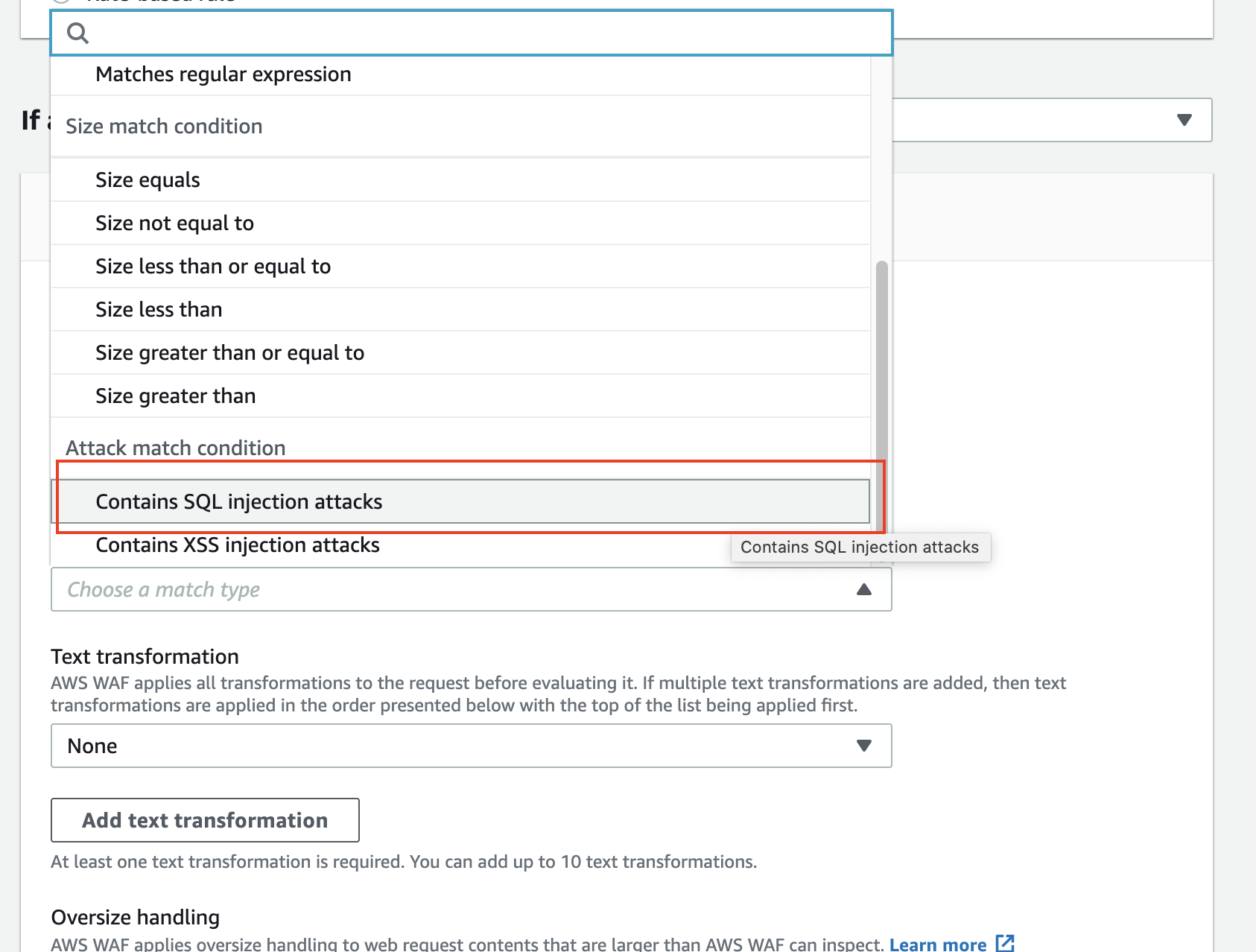
There is a section for the Sensitivity level under “Statement,” so select the option to complete the setting.
You can change the sensitivity level of the existing SQL injection attack rule statement by editing the rule.
4. Effects on WafCharm
WafCharm’s rules are individually created by using regular expressions. There are no settings like sensitivity level for WafCharm rules, and we do not use the SQL injection attack rule statement AWS WAF provides.
Moreover, please do not add the SQL injection attack rule statement as your own rule if you use WafCharm rules in your Web ACL. We will update our system soon so that you can add your own rule using the SQL injection attack rule statement.
5. Conclusion
The rule details are not disclosed, so comparing the differences between sensitivity levels is difficult. However, it is possible to experience more false positives by changing the sensitivity level to HIGH depending on the system. If you are considering adjusting the sensitivity levels for your current system, it might be better to apply the COUNT action to see the effect before fully implementing the setting with the BLOCK action.




