Table of Contents
- 1. Introduction
- 2. What is inspect all headers option?
- 3. What is oversize handling for request components option?
- 4. Configuration steps
- 5. Effects on WafCharm
- 6. Conclusion
1. Introduction
On April 30th, 2022 (PDT), AWS WAF updated inspect all headers option and oversize handling for request component option. In this post, we will talk about the features and configurations of the options.
2. What is inspect all headers option?
Previously, you had to specify a header in each rule if you wanted to have rules targeting headers in AWS WAF. Because you had to create a rule for each header, it consumed a lot of WCU, requiring you to narrow down the headers to inspect.
However, this option allows you to specify multiple headers in one rule. The specifications available are as below.
- All headers
- Excluded headers (inspect headers other than the specific header)
- Inspect header that includes specific strings
You can also specify key, value, or both for the match scope.
3. What is oversize handling for request components option?
In AWS WAF, the size of a request it can inspect is limited to a maximum of 8 KB. Therefore, rule settings were also only limited to inspecting up to 8 KB.
Below are the limitations based on the AWS WAF specification.
-
Body and JSON Body
The first 8 KB of the body of a request can be inspected. -
Headers
At most, the first 8 KB of the request headers and the first 200 headers can be inspected. The content is available for the inspection up to the first limit reached. -
Cookies
At most, the first 8 KB of the request cookies and the first 200 cookies can be inspected. The content is available for the inspection up to the first limit reached.
With this new option, you can select what AWS WAF does when a request exceeds the limits from the choices listed below.
-
Continue
Inspect the request according to the rule inspection criteria and by following the AWS WAF specification (the same as before). -
Match
Treat the request as matching the rule statement. If a rule has BLOCK action, then the request will be blocked. -
No match
Treat the request as not matching the rule statement.
4. Configuration steps
We will create a rule just like other rules.
Select “All headers” under the “Request components.”
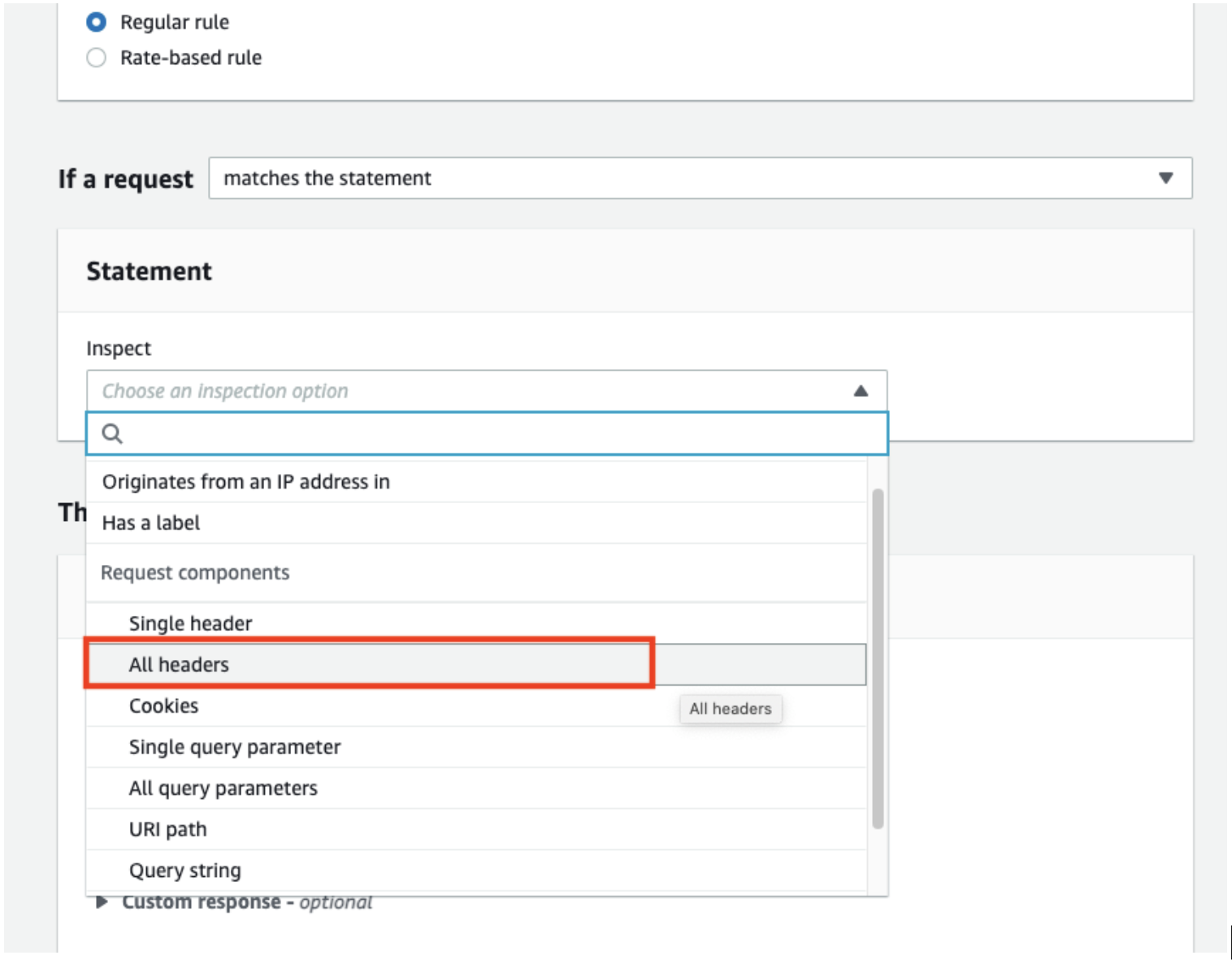
When you select “All headers,” options for headers match scope and content to inspect will appear.
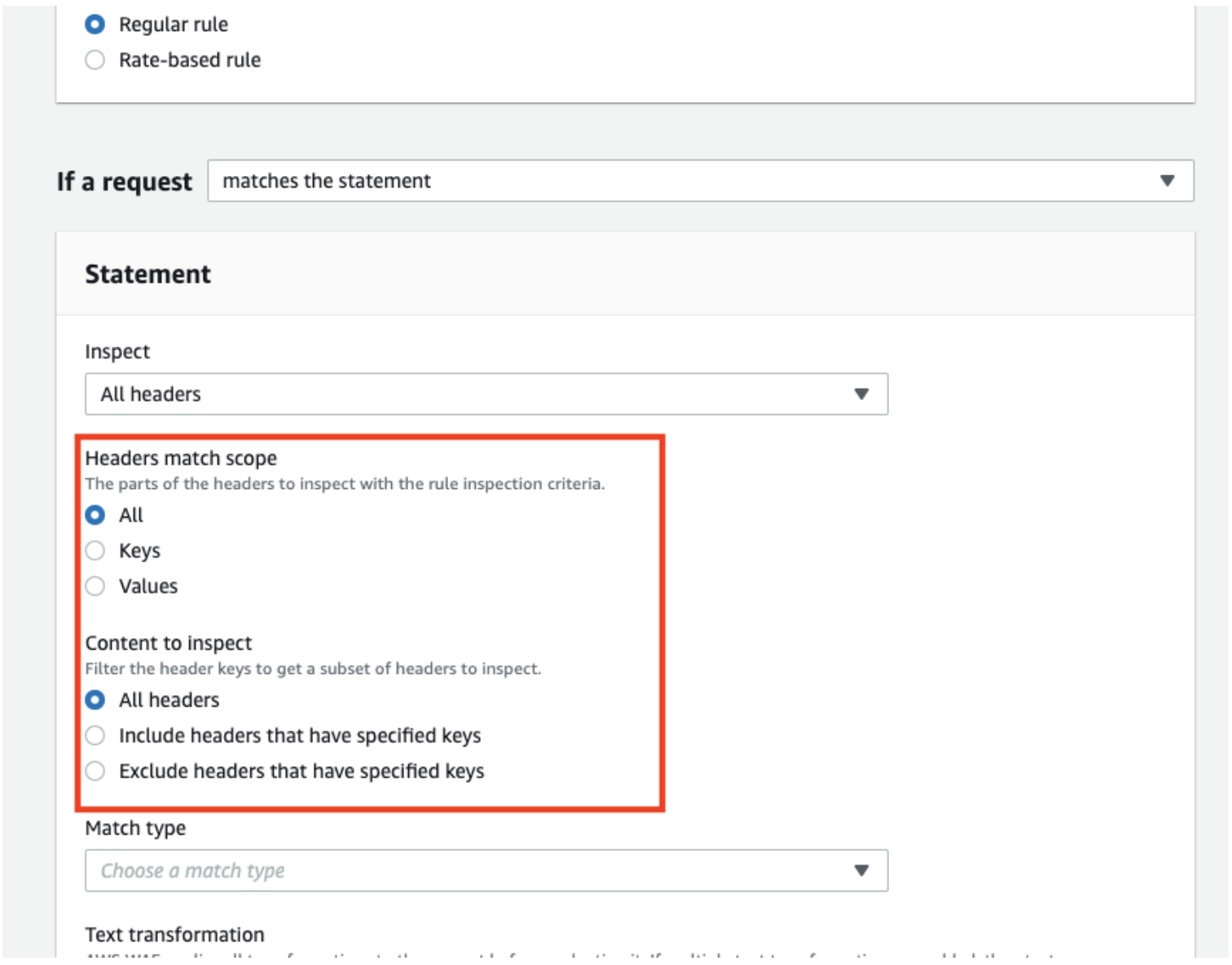
By selecting the “Exclude headers that have specified keys” option, you’ll see a text field to enter keys to exclude.
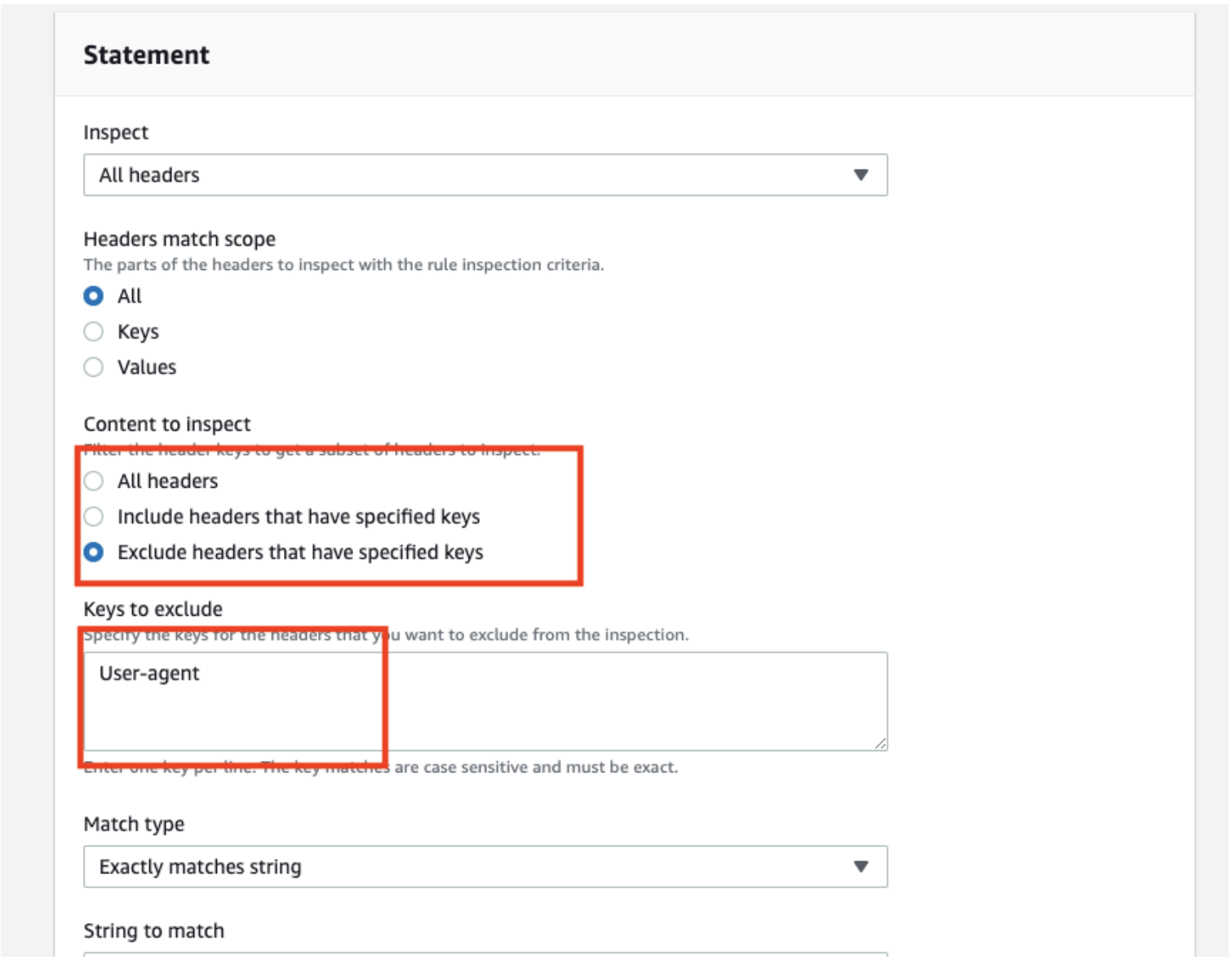
For requests exceeding the inspection limit, select an option below the “Oversize handling” field.
*Oversize handling can only be selected when you have specified Body, Cookies, or All headers under the “Inspect” field.
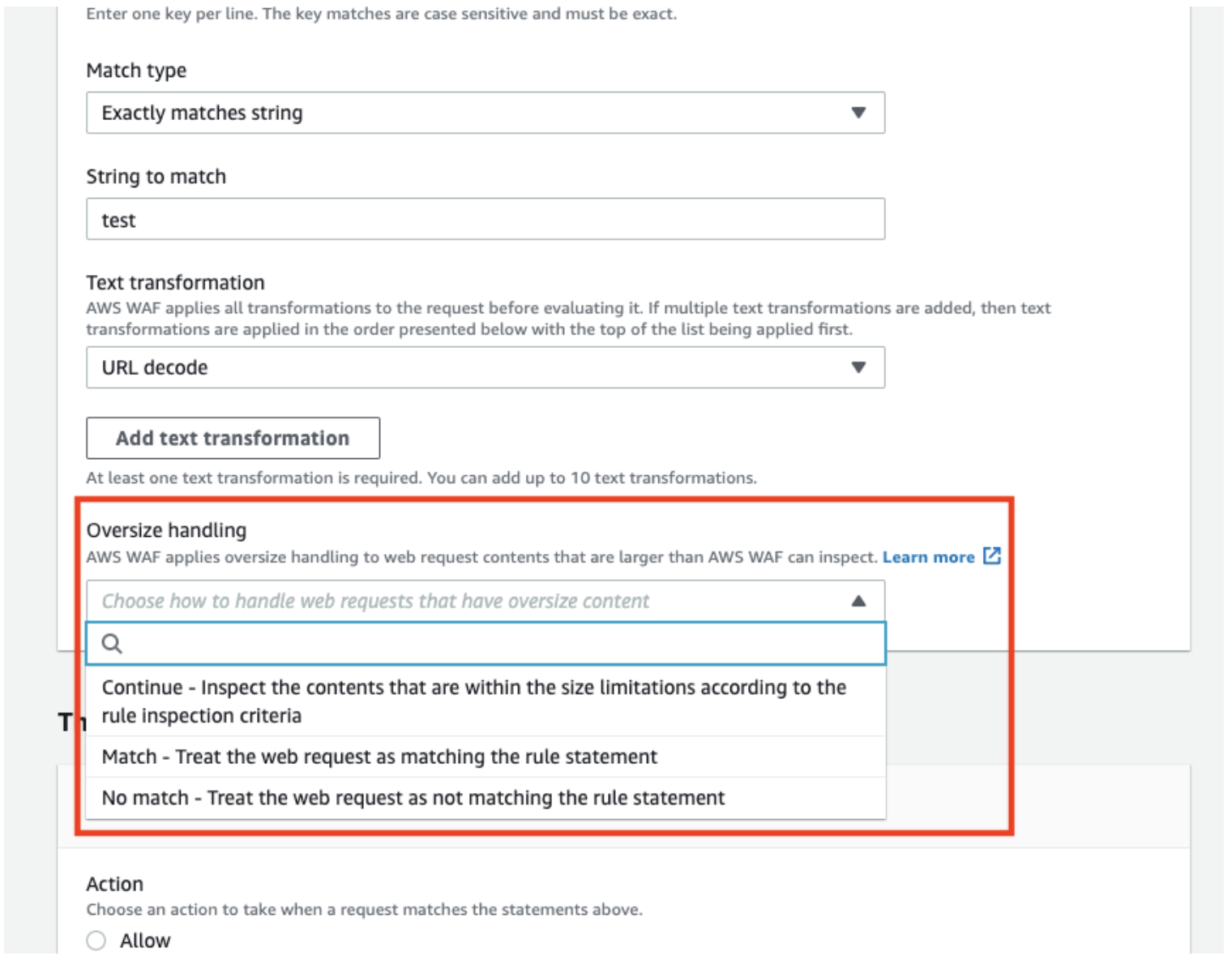
When you look at the created rule in JSON format, you can see that all the options selected are listed under the Headers, and a property “OversizeHandling” is added.
{
"Name": "test",
"Priority": 6,
"Action": {
"Block": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "test"
},
"Statement": {
"ByteMatchStatement": {
"FieldToMatch": {
"Headers": {
"MatchScope": "ALL",
"MatchPattern": {
"ExcludedHeaders": [
"User-agent"
]
},
"OversizeHandling": "CONTINUE"
}
},
"PositionalConstraint": "EXACTLY",
"SearchString": "test",
"TextTransformations": [
{
"Type": "URL_DECODE",
"Priority": 0
}
]
}
}
}
On May 6th, 2022, we found that if you use regex rules (regular expressions and regex pattern set) via the AWS management console, the OversizeHandling option is not applied correctly. A workaround is to use the JSON editor and add the OversizeHandling property manually.
5. Effects on WafCharm
We have updated WafCharm to avoid any issues that may be presented with this AWS WAF update.
6. Conclusion
You will have a higher chance of detection by inspecting all headers, but it could also cause you to have a higher chance of false positives.
Even if a value contains what seems to be an attack, if that value is not processed in your system, it may not cause effects. However, it is definitely suspicious access, so it could be helpful to implement these new options after considering the impact of false positives.
For the oversize handling for request components option, if your system does not expect to exceed the limit, you could set the option to block requests once their size exceeds the limit. If there are no limitations within the system, you could use CONTINUE for the action.



