In this blog, we will explain about Rule Group Exceptions for Managed Rules for AWS WAF and how to set it up. Rule Group Exceptions allows you to override individual rules within a managed rule group, i.e. excluding a rule from the rule group. You can choose which rules within the rule group should be excluded and set in count-only mode, preventing those rules from blocking a request. This will allow you to modify the behavior of a managed rule group so that it can be modified to your unique environment.
Typically, any customization within the managed rule group requires you to reach out to your managed rules provider. However, using this function, you can customize it on your own by changing the action for the individual rule to COUNT. Therefore, requests that match an excluded rule are counted, but not blocked. This helps you try out new managed rule groups for AWS WAF, react faster to abnormal conditions, and gives you more control over your web ACLs.
Contents
- 1. Setting up "Rule Group Exception"
- 2. Operation of Rule group exceptions and confirmation of full logging
1. Setting up "Rule Group Exceptions"
Adding a managed rule to the exception list is done in three steps.
Step1. Enable AWS WAF full logging feature.
Step2. Identifying the "ruleId" of the unwanted rule from the log.
Step3. Excluding the rule either through the AWS WAF console or through the API.
Step1. Enable AWS WAF full logging feature.
If not already enabled, enable AWS WAF full logging. For more information, see "Output Full Log of AWS WAF to S3". Analyze incoming traffic using the full logging feature and look for unexpected behavior within the rule group.
Step2. Identifying the "ruleId" of the unwanted rule from the log
Use the AWS WAF logs to identify the IDs of the rules that you want to exclude. These are typically rules that are blocking legitimate requests.
There are two modes in Managed Rules: BLOCK mode (No override) and COUNT mode (Override to count).
The output contents of the full log differ slightly depending on these two modes, but the "ruleId" that requires our attention, is described in the same place.
Also note that "ruleId" is different for each region, so be very careful. For example, "ruleId" for Managed Rules of Tokyo region is different than "ruleId" for Managed Rules of N.Virginia region.
| Managed Rules is in BLOCK mode (No override) |
Managed Rules is in COUNT mode (Override to count) |
|
| Location of "ruleId" required for Rule Group Exceptions |
The specific "ruleId" is the one in "terminatingRule" in "ruleGroupList". | The specific "ruleId" is the one in "terminatingRule" in "ruleGroupList". |
Full log contents when Managed Rules is in BLOCK (No override) mode
(The Managed Rules used this time was "Fortinet Managed Rules for AWS WAF - Complete OWASP Top 10")
{
"timestamp": xxxxxxxxxxx,
"formatVersion":1,
"webaclId":"5ad3da2f-e79d-xxxx-xxxx-xxxxxxxxxxxx",
"terminatingRuleId":"3747215b-91ff-xxxx-xxxx-xxxxxxxxxxxx",
"terminatingRuleType":"GROUP",
"action":"BLOCK",
"httpSourceName":"ALB",
"httpSourceId":"app/f6ba4d85d77dd153",
"ruleGroupList":[
{
"ruleGroupId":"3747215b-91ff-xxxx-xxxx-xxxxxxxxxxxx",
"terminatingRule":{
"ruleId":"c8dd8378-6959-xxxx-xxxx- xxxxxxxxxxxx",
"action":"BLOCK"
},
"nonTerminatingMatchingRules":[],
"excludedRules":null
}
],
"rateBasedRuleList":[],
"nonTerminatingMatchingRules":[],
〜Omitted〜
Full log contents when Managed Rules is in COUNT (Override to Count) mode
※ In COUNT mode, "ruleId" is in 2 places. "ruleId" in "terminatingRule" of "ruleGroupList" is the correct one. Don't use the "ruleId" in "nonTerminatingMatchingRules".
{
"timestamp": xxxxxxxxxxx,
"formatVersion":1,
"webaclId":"5ad3da2f-e79d-xxxx-xxxx-xxxxxxxxxxxx",
"terminatingRuleId":"Default_Action",
"terminatingRuleType":"REGULAR",
"action":"ALLOW",
"httpSourceName":"ALB",
"httpSourceId":"app/f6ba4d85d77dd153",
"ruleGroupList":[
{
"ruleGroupId":"3747215b-91ff-xxxx-xxxx-xxxxxxxxxxxx",
"terminatingRule":{
"ruleId":"c8dd8378-6959-xxxx-xxxx-xxxxxxxxxxxx",
"action":"BLOCK"
},
"nonTerminatingMatchingRules":[],
"excludedRules":null
}
],
"rateBasedRuleList":[],
"nonTerminatingMatchingRules":[
{
"ruleId":"3747215b-91ff-xxxx-xxxx-xxxxxxxxxxxx",
"action":"COUNT"
}
]
〜Omitted〜
Step3. Excluding the rule either through the AWS WAF console or through the API.
In Step 2, we were able to specify that the "ruleId" of the rule to be excluded is「c8dd8378-6959-xxxx-xxxx- xxxxxxxxxxxx」
In this step, we will set exclusion settings for this "ruleId".
Here, assuming that a false positive occurred while Managed Rules is in BLOCK (No override) mode, we introduce the flow to change only the rule with ruleId「c8dd8378-6959-xxxx-xxxx- xxxxxxxxxxxx」to COUNT mode.
Step3-1. Go to the AWS WAF console (https://console.aws.amazon.com/waf/).
Step3-2. AWS WAF Navigation > Web ACLs > select "applicable WebACL" > "Rules" tab > Choose "Edit web ACL"
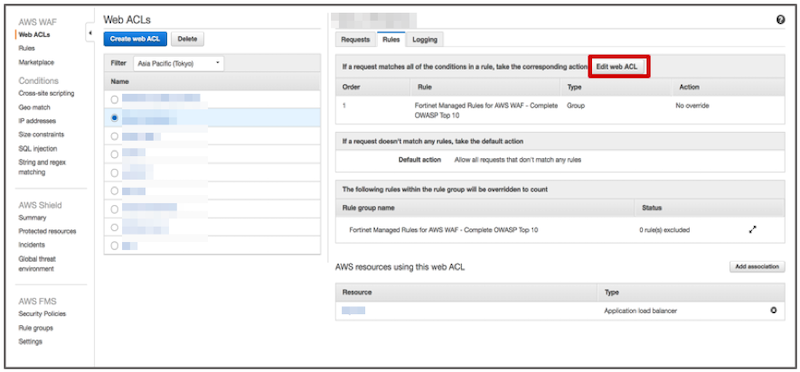
Step3-3. Click on the arrow button in the red frame.
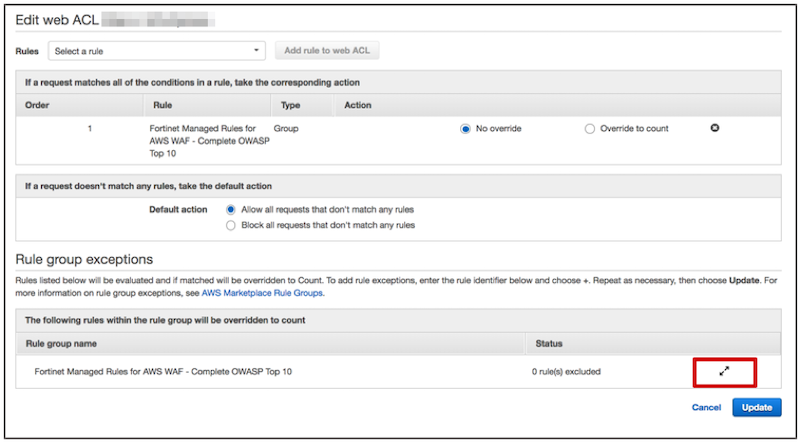
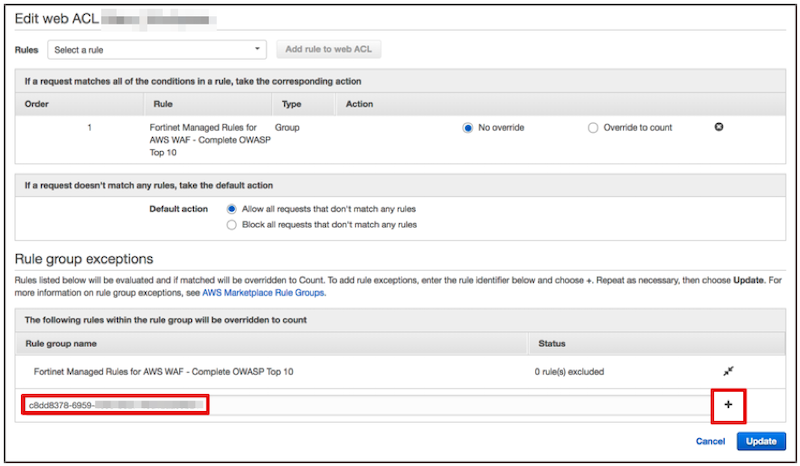
Step3-4. Enter "ruleId" in the red frame on the left and click the “+” button on the right red frame.
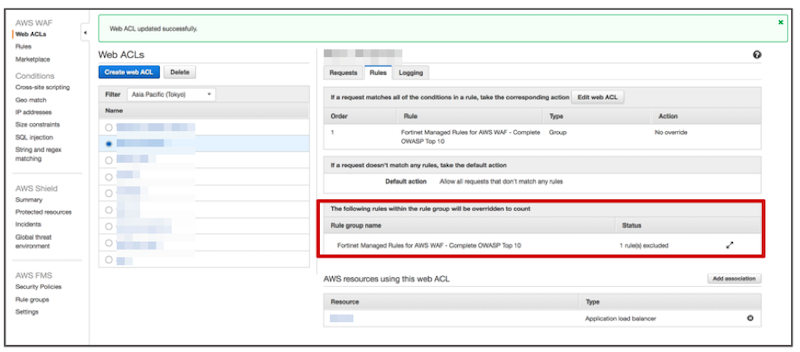
Step3-5. After confirming the status change from "0 rule (s) excluded" to "1 rule (s) excluded", choose "Update".
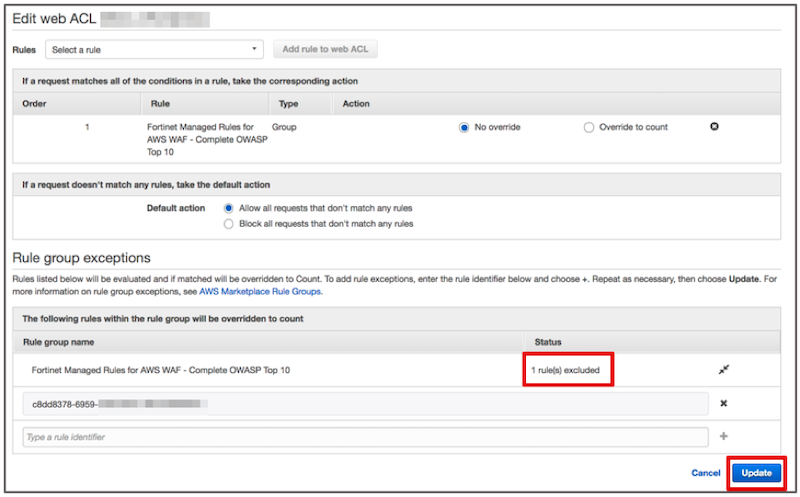
Step3-6. If it states "1 rule (s) excluded" for the corresponding managed rule like in the red frame below, the setting is complete.
2. Operation of Rule group exceptions and confirmation of full logging
It was confirmed that a pseudo attack request that returns "403 (forbidden)" before the "Rule Group Exceptions" setting, returns "200 OK" after the setting is complete.
Request: curl http://xxxxxxxx.ap-northeast-1.elb.amazonaws.com/?pw=%27%20or%201%20=%201
Before Rule Group Exceptions setting: 403 forbidden
After Rule Group Exceptions setting: 200 OK
As a result, with the Rule Group Exceptions setting, when Managed Rules is in BLOCK mode, individual rules can be excepted.
And on the full log, it was found that it is output to "ruleId" of "excludedRules" of "ruleGroupList" when it is detected by rule set in "Rule Group Exceptions".
Full log contents when Managed Rules is in BLOCK (No override) mode and only the rule with ruleId「c8dd8378-6959-xxxx-xxxx- xxxxxxxxxxxx」is excluded.
{
"timestamp": xxxxxxxxxxx,
"formatVersion":1,
"webaclId":"5ad3da2f-e79d-xxxx-xxxx-xxxxxxxxxxxx",
"terminatingRuleId":"Default_Action",
"terminatingRuleType":
"REGULAR","action":"ALLOW",
"httpSourceName":"ALB",
"httpSourceId":"app/f6ba4d85d77dd153",
"ruleGroupList":[
{
"ruleGroupId":"3747215b-91ff-xxxx-xxxx-xxxxxxxxxxxx",
"terminatingRule":null,
"nonTerminatingMatchingRules":[],
"excludedRules":[
{
"ExclusionType":"EXCLUDED_AS_COUNT",
"ruleId":"c8dd8378-6959-xxxx-xxxx- xxxxxxxxxxxx"
}
〜Omitted〜
Note: Excluding rules does not remove those rules from the rule group. Rather, it changes the action for the rules to COUNT. Therefore, requests that match an excluded rule are counted but not blocked. You will receive COUNT metrics for each excluded rule.



