Table of Contents
- 1. Introduction
- 2. How to start using Network Security Director
- 3. Dashboard screen
- 4. Resources screen
- 5. Findings screen
- 6. About the “Remediation recommendations” section
- 7. Conclusion
1. Introduction
On June 17, 2025, AWS announced a new feature called Network Security Director (currently in preview).
New AWS Shield feature discovers network security issues before they can be exploited (Preview)
As stated in the official AWS blog post above, Network Security Director is a feature of AWS Shield. It analyzes resources such as EC2 instances, ALB, CloudFront, AWS WAF, and other network security services to detect misconfigurations, suggest remediation steps, and recommend ideal configurations.
As this feature is currently in preview, its specifications and pricing may change in the future. For now, we’d like to explore the functionalities currently available.
2. How to start using Network Security Director
When you open the WAF & Shield screen, you’ll see an item called [AWS Shield network security director] in the left-hand menu. Click the [Getting started] link.
On the right side of the screen, click the [Get started] button to begin scanning the target resources. Once the analysis starts, a message indicating that the scan is in progress will appear at the top of the screen. Please wait until the analysis is complete.
3. Dashboard screen
After the analysis is complete, the results will be displayed on the Dashboard screen. Here, you can view an overview of the analysis, the number of each resource, and the types of findings.
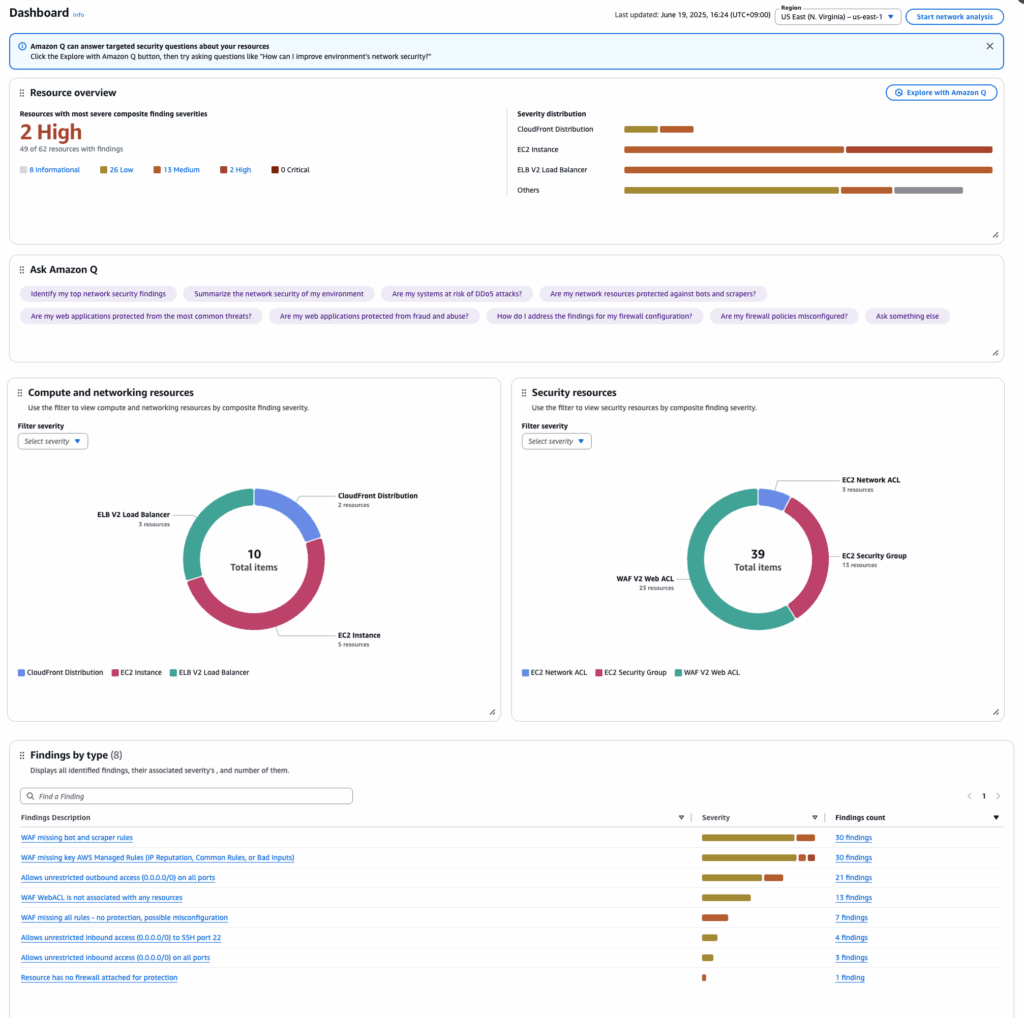
As indicated by the [Ask Amazon Q] panel in the middle of the screen, it appears that the feature is designed to let users analyze the findings using Amazon Q, AWS’s AI assistant.
When you click the button, the Amazon Q panel opens on the right with the selected question already entered in the input field.
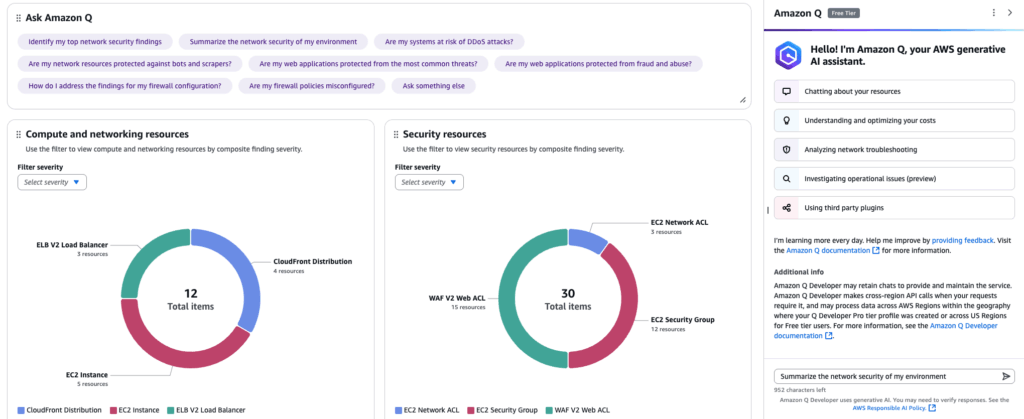
For example, by selecting [Summarize the network security of my environment] and sending the prompt, Amazon Q generates a summary based on the results from Network Security Director.
In the test environment scanned using Network Security Director, the summary noted findings related to internet access to EC2 instances and WAF configurations associated with ALB.
It also provided around four recommendations for actions that should be taken right away. These appear to be based on factors like severity levels and the specific details included in the Network Security Director findings.
In Amazon Q, as the [Ask something else] option in the panel suggests, you can also ask free-form questions.
In this test environment, there was a web ACL with no rules applied, so we asked Amazon Q to suggest rules other than the AWS Managed Rules. It recommended actions such as creating rate-based rules targeting suspicious requests, and applying rules to detect SQL injection and cross-site scripting attacks.
While it appeared to have some difficulty providing highly detailed regular expressions or rules tailored to the characteristics of the application, it could still be useful as a reference when creating rules or thinking through your policy.
It also seems to be able to answer questions like what risks are associated with the configurations flagged in the findings. The response included both the actual risks and best practices for mitigation, so Amazon Q might be helpful in situations where you have findings but aren’t sure how to proceed.
Amazon Q appears to generate responses based on the content of the screen you’re currently viewing. So if you want to ask questions related to Network Security Director, it’s probably best to do so while on the Network Security Director screen.
4. Resources screen
The Resources screen displays a list of analyzed resources. At the moment, it appears that only up to 100 resources can be displayed.
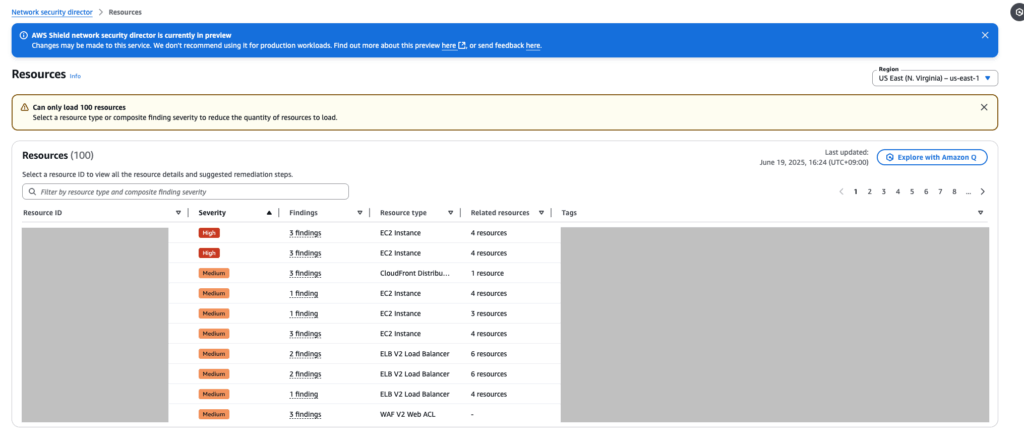
When you click the resource ID on this screen, you’ll be taken to a page called Network topology. There, you’ll see a digram showing how the selected resource is connected to other resources.
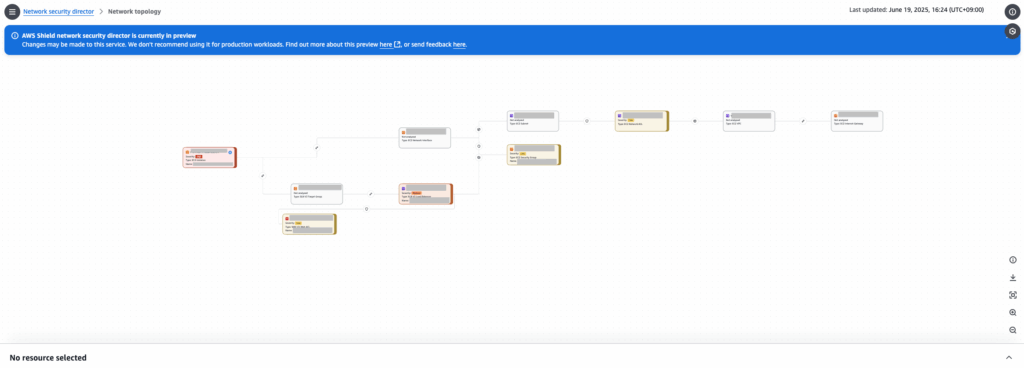
In the bottom-right corner, you’ll see buttons for interacting with the Network Topology diagram. By clicking the download button (the second one from the top), you can download a CSV file containing information about internet gateways.
When you click a resource in the diagram, a panel will appear below displaying information about that resource.
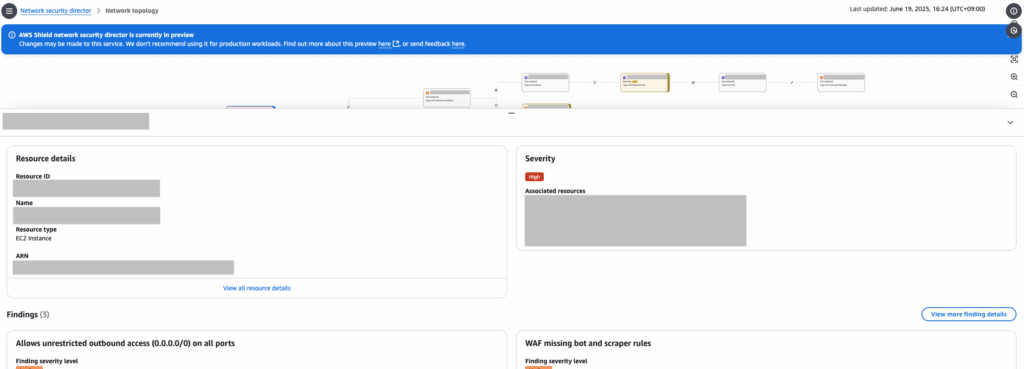
The panel has a limited viewing area. By clicking the [View all resource details] link in the panel, you can view the same information on a larger screen. If you want to take a closer look at a specific resource, this option might be more suitable.
5. Findings screen
When you open the Findings screen, you’ll see a list of detected findings instead of resources. At the moment, it appears that only up to 100 findings can be displayed.
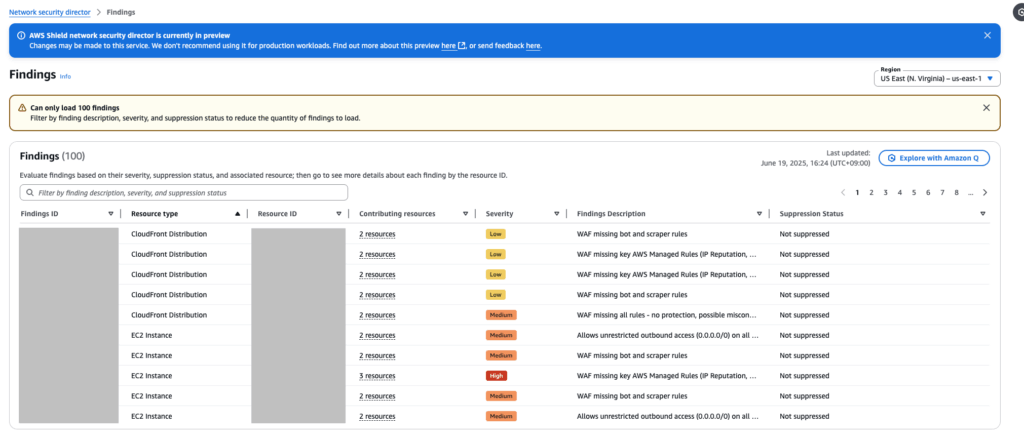
When you click a Findings ID, you'll be taken to the details screen of the resource associated with that finding. This is the same screen you see when you click the [View all resource details] link in the Network Topology resource details panel.
In the Findings screen, you can also see the suppression status for each result listed.
As of July 29, 2025, we couldn’t find any information about the suppression status in the official documentation. However, since the interface allows us to suppress findings on the screen, we believe it likely serves the same purpose as suppression in other AWS services like Security Hub, indicating that no further action is needed for that particular finding.
For example, one of the checks in Network Security Director analyzes whether AWS Managed Rules (e.g., AWSManagedRulesAmazonIpReputationList and AWSManagedRulesCommonRuleSet) are applied to a given web ACL.
Even if rules provided by WafCharm are applied, the finding will still be flagged because they are not considered part of AWS Managed Rules.
However, if you're already using WafCharm, you may have intentionally chosen not to use AWS Managed Rules. In such a case, you can mark the finding about the missing AWS Managed Rules as unnecessary by changing its status to suppressed, which may help you manage the overall findings more appropriately.
Please note that enabling the Suppression status on a finding will also reduce the [Findings count] shown on the Dashboard screen.
6. About the “Remediation recommendations” section
Remediation recommendations are suggested actions displayed for each finding, shown on the resource details page.
For example, in the finding about the missing AWS Managed Rules mentioned earlier, the remediation recommendation provides detailed steps for creating a web ACL and attaching AWS Managed Rules (e.g., AWSManagedRulesAmazonIpReputationList and AWSManagedRulesCommonRuleSet).
As in the example above, if you've already addressed the issue using other measures and determined that no further action is needed, you can complete the process by clicking the [Suppress] button.
However, depending on the nature of the finding, there may be no existing mitigation in place. If you're confident that applying the recommended remediation will not negatively impact your current system, it's likely best to implement the suggested steps accordingly.
7. Conclusion
Network Security Director is useful for reviewing your current configuration, spotting any missing security settings, and seeing how to remediate them in detail.
On the other hand, it can be difficult to determine whether remediation is necessary if you don’t have a thorough understanding of the current configurations.
In addition, since this feature is still in preview, the user interface and internal behavior may change in the future. There are no additional costs at the moment, but pricing may vary in the future depending on the number of scans or resources involved.




